Zimperium Identifies Over 760 Active NFC Malware Apps Targeting Eastern Europe

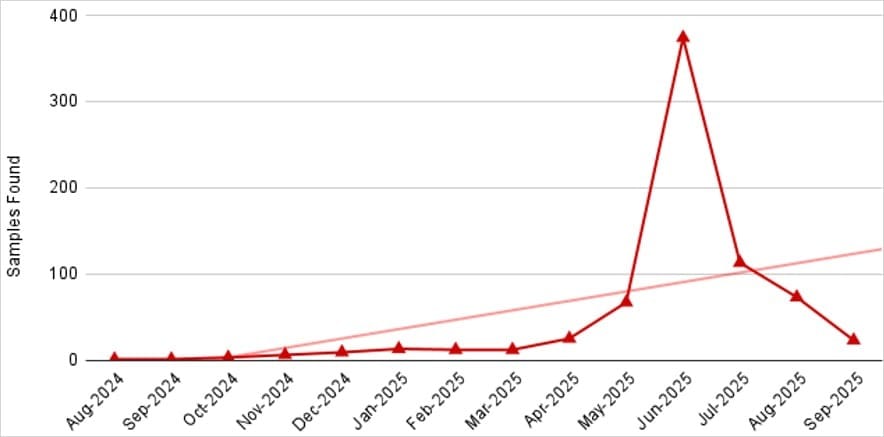
Zimperium researchers are warning about a surge in NFC-based malware targeting Android users across Eastern Europe. In recent months, the security firm identified more than 760 malicious applications that exploit NFC technology to steal payment data from victims. This represents a sharp increase from the isolated samples discovered when these attacks first emerged.
How NFC Malware Differs From Traditional Banking Trojans
Traditional banking Trojans rely on familiar tactics. They display phishing overlays that capture login credentials, or they gain remote access to devices through RATs (Remote Access Trojans). Users typically see fake login screens or grant permissions that give attackers control over their devices.
NFC malware takes a different approach. It exploits a legitimate Android feature called Host Card Emulation (HCE). Google built this feature to let phones emulate contactless payment cards—the technology that lets you tap your phone at checkout instead of using a physical credit card. Attackers abuse this same feature to intercept and manipulate payment transactions.
Three Types of NFC Malware Operations
The researchers identified three distinct operational methods these malicious applications use:
Data Interception Variants
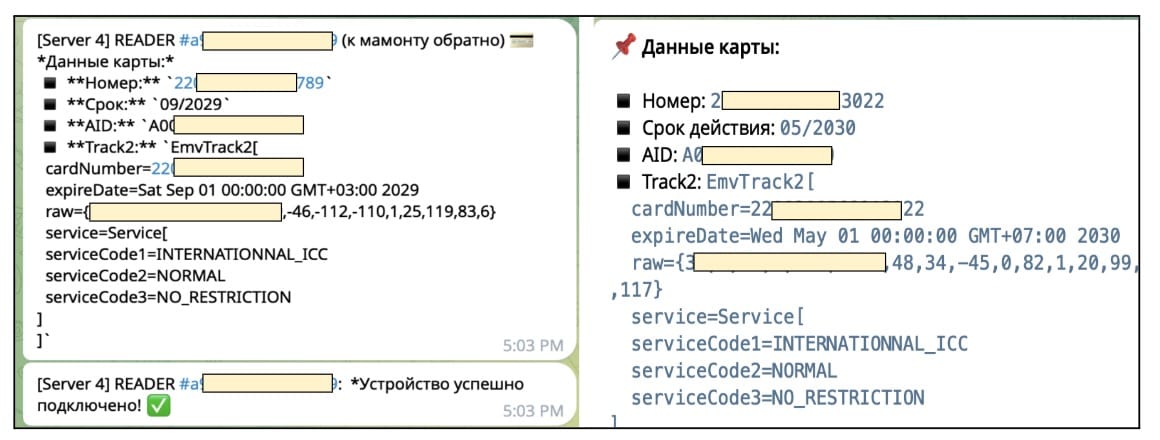
The first type intercepts EMV fields during payment transactions. EMV refers to the chip card standard (Europay, Mastercard, and Visa) used in contactless payments. These malware variants capture the payment data and send it to attackers through two channels: Telegram bots or command-and-control servers. The stolen information includes card details that criminals can use for fraudulent transactions.
APDU Command Relay Variants
The second type operates more actively in payment processing. These applications forward APDU commands from point-of-sale terminals to remote servers controlled by attackers. APDU (Application Protocol Data Unit) commands represent the communication between payment terminals and cards. The attackers' servers generate appropriate responses to authorize payments. This happens without a physical card present and without the owner's knowledge or consent. The victim's phone essentially becomes a relay device, processing transactions the owner never initiated.
Ghost Tap Advanced Variants
The third type uses sophisticated techniques like Ghost Tap. These variants manipulate HCE responses in real-time during the payment process. The malware intercepts the transaction at the checkout, modifies the payment authorization data, and completes fraudulent purchases on the spot. This represents the most advanced version of NFC attacks because it requires precise timing and technical execution.
Disguises and Installation Methods
Many samples disguise themselves as Progressive Web Apps (PWAs) or fake banking applications. During installation, they register themselves as the default payment handler on Android devices. This positioning gives the malware priority access to all NFC payment interactions on the phone.
The Evolution From NFCGate to Widespread Attacks
These attacks trace back to the fall of 2023, when security researchers first noticed unusual activity targeting customers of major Czech banks. The initial attacks centered around NFCGate, an open-source application created in 2015 by students at Darmstadt University of Technology.
The original developers built NFCGate as a debugging tool for NFC data transmission protocols. The application includes numerous legitimate functions for testing and analyzing NFC communications. However, one feature attracted criminal attention: the ability to capture NFC application traffic and transmit it to a remote device—either a server or another smartphone.
Attackers modified NFCGate to serve their purposes. What started as an academic tool became the foundation for financial fraud campaigns.
The Russian Case Study: Rapid Growth and Significant Losses
Russia provides clear data on how quickly these attacks spread and the financial damage they cause. The first attacks using weaponized versions of NFCGate appeared in August 2024. By the end of March 2025—just seven months later—the total financial damage reached 432 million rubles.
Researchers at F6 tracked the attack frequency during the first quarter of 2025. Criminals successfully executed an average of 40 attacks per day during January through March. The average loss per attack was 120,000 rubles. These numbers demonstrate both the scale and effectiveness of NFC malware campaigns.
Current Scale of the Threat
Zimperium's research reveals the scope of this malware ecosystem. The firm discovered:
- Over 760 malicious NFC applications currently active
- More than 70 command-and-control servers
- Dozens of malware distribution platforms
- Multiple Telegram bots used for coordinating operations
- Private Telegram channels where attackers receive stolen data
"What started as a few isolated [malware] samples has grown to over 760 malicious applications. NFC attacks are not slowing down but continue to accelerate," the Zimperium team notes in their report.
This infrastructure supports a mature criminal operation. The attackers maintain multiple servers for redundancy, use encrypted messaging platforms for communication, and operate distribution networks that reach victims across Eastern Europe.
Targeted Financial Institutions
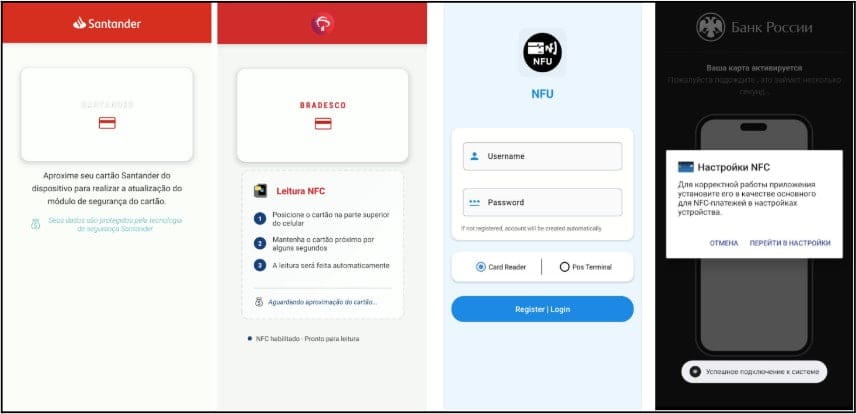
The malware primarily spreads through fake applications that impersonate legitimate banking and payment services. Attackers exploit the brand recognition of major financial institutions to trick users into installing their malicious apps.
The research identified fake applications mimicking these brands:
- Google Pay (payment platform)
- Santander Bank
- VTB Bank
- Tinkoff Bank
- Bank of Russia
- ING Bank
- Bradesco Bank
- Promsvyazbank
The researchers emphasize that these fake applications can be visually convincing. The attackers invest effort into making their malware look identical to legitimate banking apps. Users see familiar logos, color schemes, and interface layouts that match the real applications.
My Assessment of This Threat
In my opinion, NFC malware represents a significant evolution in mobile financial threats. The attacks exploit a feature that users trust implicitly—contactless payment. People tap their phones hundreds of times without thinking about the underlying technology. This trust creates opportunity for criminals.
Per the Zimperium findings, the rapid growth from isolated samples to over 760 active applications shows this approach works. Criminals continue developing new variants because they generate revenue. The 432 million ruble loss figure from Russia alone proves these campaigns are profitable.
Why These Attacks Succeed
Several factors make NFC malware effective:
Technical Sophistication: The attacks exploit legitimate Android features rather than system vulnerabilities. This makes detection harder because the malware uses authorized functionality.
User Trust: Contactless payment feels secure to users. They associate tapping their phone with bank-approved technology, not malware.
Visual Deception: The fake applications look authentic. Users who download what appears to be their bank's app have no reason to suspect malware.
Low Detection Rates: Traditional security software struggles to identify these attacks because the malware operates within permitted Android parameters.
Quick Execution: Transactions happen in seconds. By the time victims notice unauthorized charges, the criminals have already moved the money.
Practical Protection Steps
Zimperium provided recommendations for Android users. I'll expand on these with additional context:
Source Control for Applications
Never install APK files from third-party sources or untrusted publishers. This recommendation deserves emphasis. Banking applications should only come from official app stores. Even then, verify the publisher name matches the bank exactly.
Install banking applications using official links from the banks' websites. Don't search for banking apps in the Play Store—go to your bank's website first, then click their link to the official app. This step prevents installing lookalike applications with similar names.
Permission Scrutiny
Carefully examine requested permissions before installing any application. Two permissions should raise immediate suspicion:
- NFC access: Food delivery apps, social media apps, and most other applications have no legitimate reason to access NFC. If an app requests this permission without clear justification, don't install it.
- Background service privileges: Payment apps need some background permissions, but be wary of apps requesting extensive background access. Legitimate banking apps explain why they need specific permissions.
Regular Security Scanning
Use Play Protect to scan your device regularly. Google's built-in security system can detect known malware signatures. Enable automatic scanning in your device settings.
Consider installing reputable third-party security software from established vendors. These applications provide additional detection layers beyond Play Protect.
NFC Management
Disable NFC when you're not actively using it for payments. Most Android devices let you turn NFC on and off through quick settings. This simple step eliminates the attack surface when you're not at a checkout.
To disable NFC completely:
- Open Settings
- Navigate to Connected Devices or Connections
- Find NFC and turn it off
Enable it only when making a payment, then disable it again.
Additional Protective Measures
Beyond Zimperium's recommendations, consider these steps:
Monitor Financial Accounts: Check your bank statements and transaction history frequently. Set up alerts for all transactions so you receive immediate notification of any payment.
Use Official Payment Apps: Stick with Google Pay, Apple Pay, or your bank's verified application. Don't experiment with third-party payment apps promising extra features or rewards.
Keep Android Updated: Install security patches as soon as they become available. These updates often address vulnerabilities that malware exploits.
Research Before Installing: Before downloading any banking or payment app, search for reviews and security reports. If researchers have identified an app as malicious, you'll find warnings online.
Verify Publisher Information: In the Play Store, check the developer's name carefully. Attackers create accounts with names similar to legitimate banks. "VTB Bank Official" might be fake while "VTB Bank" is real—or vice versa. Cross-reference with your bank's website to confirm the correct publisher name.
For Financial Institutions
Banks and payment providers should take active measures to protect their customers:
Education Campaigns: Inform customers about NFC malware threats. Send emails explaining how to identify fake applications and verify legitimate ones.
Official Download Pages: Maintain clear, prominent links to official applications on your website. Include screenshots showing what the real app looks like in the store.
Brand Monitoring: Actively search app stores for applications impersonating your brand. Submit takedown requests immediately when you find fake apps.
Customer Support: Train support staff to help customers verify they've installed legitimate applications. Provide clear guidance when customers report suspicious app behavior.
The Outlook for NFC Malware
The acceleration Zimperium reports suggests these attacks will continue growing. The 760 active applications represent significant criminal investment. Attackers wouldn't maintain this many variants if the approach wasn't generating profits.
Furthermore, the infrastructure supporting these campaigns—70+ command servers, multiple Telegram channels, distribution platforms—indicates organized operations with resources. This isn't amateur hour. Professional criminals are running these campaigns.
The shift from Czech banks in 2023 to widespread Eastern European attacks in 2025 shows geographic expansion. As security improves in one region, attackers likely move to new markets. Organizations and users in other parts of Europe, Asia, and eventually other regions should prepare for similar campaigns.
Final Thoughts
NFC technology provides convenience, but that convenience comes with risk when criminals abuse legitimate features. The rapid evolution from NFCGate debugging tool to 760 malicious applications demonstrates how quickly attackers adapt new technologies for fraud.
Users must approach mobile payments with the same caution they apply to desktop banking. Your phone handles the same sensitive financial data as your computer—it deserves the same security attention. Verify applications before installation, scrutinize permissions, and disable NFC when not in use.
The 432 million ruble loss in Russia during seven months proves the financial stakes. These attacks cause real harm to real people. Taking protective steps now prevents becoming another statistic in next quarter's damage reports.


