WireTap Attack Compromises Intel SGX Enclave Security
A team of researchers from the Georgia Institute of Technology and Purdue University has demonstrated a new hardware attack known as WireTap, which compromises the Data Center Attestation Primitives (DCAP) mechanism in Intel Software Guard Extensions (Intel SGX).
Similar to the recently disclosed Battering RAM attack, WireTap requires physical access to an SGX-enabled server. The researchers showed that a passive DIMM interposer assembled from secondhand electronic components for under $1,000 can be used to intercept and manipulate DDR4 memory traffic, undermining SGX protections.

The attack highlights the growing risk from insiders and supply chain actors, such as data center technicians, malicious cloud provider employees, or even hardware suppliers during production and delivery phases.
“Like two sides of the same coin, WireTap and Battering RAM target complementary properties of deterministic encryption. If WireTap primarily aims to compromise confidentiality, Battering RAM focuses on integrity. But the essence is the same—SGX and SEV can be defeated by manipulating memory,” the researchers wrote.
What Is Intel SGX?
Intel Software Guard Extensions (SGX) is a security feature integrated into select Intel processors. It creates enclaves—protected, isolated areas of memory—that secure sensitive data and code even from the operating system or privileged processes. SGX is designed to ensure confidentiality and integrity of critical computations, such as protecting encryption keys, personal data, or proprietary algorithms used in cloud applications.
Even if the host system is compromised, SGX enclaves are meant to remain secure. However, WireTap shows that physical-level tampering can undermine this assumption.
How WireTap Works
After installing the interposer, the researchers slowed and monitored DDR4 bus traffic, eventually gaining control of the SGX enclave by flushing the cache. This allowed them to target SGX’s cryptographic mechanisms and extract the machine attestation key—a process that took about 45 minutes.
A compromised attestation key can be devastating, as it enables attackers to impersonate trusted systems and decrypt data across multiple platforms. The researchers demonstrated this by attacking several SGX-dependent networks:
- Phala Network and Secret Network: Attackers extracted smart contract encryption keys by forging attestation quotes inside a custom enclave, allowing decryption of smart contract states across the entire network.
- Crust Network: Using a forged key, the attackers were able to generate fake proofs of storage, disrupting the integrity of network nodes.
“It is possible to create a device that allows for the physical interception of all memory traffic cheaply and simply—using basic tools available online. By using an interposer against SGX attestation, we extracted the secret key from a fully trusted machine, effectively breaking SGX security,” the researchers explained.
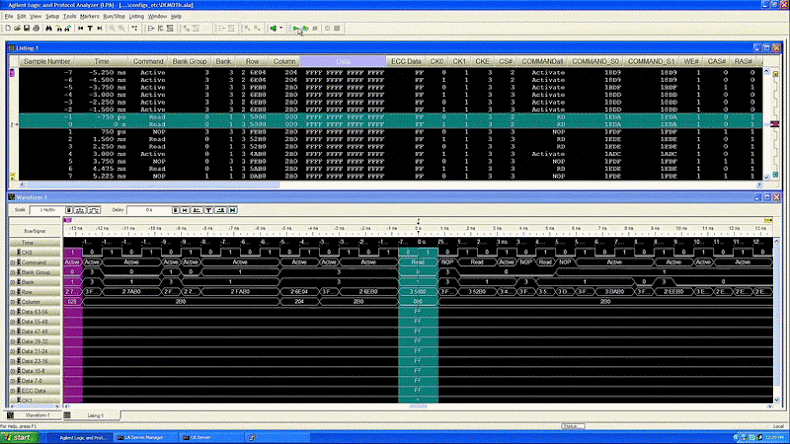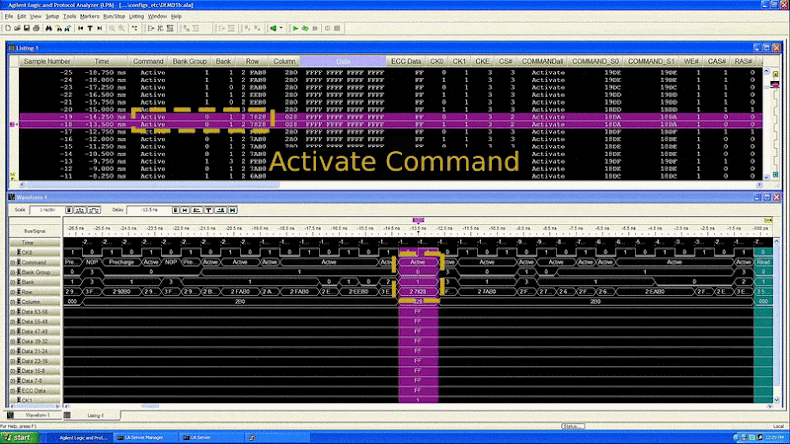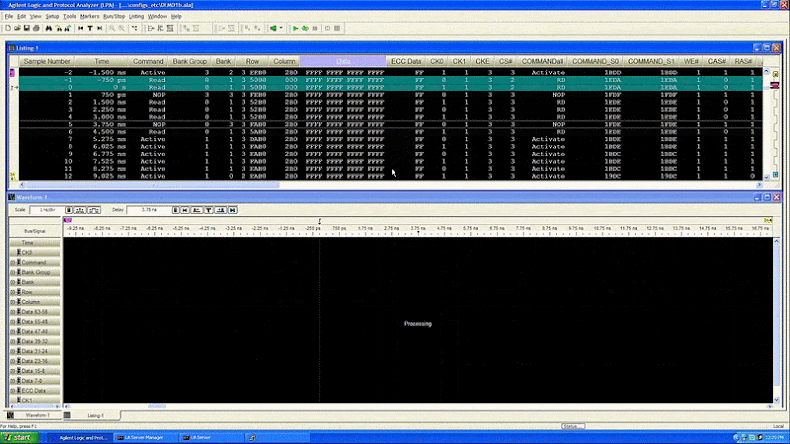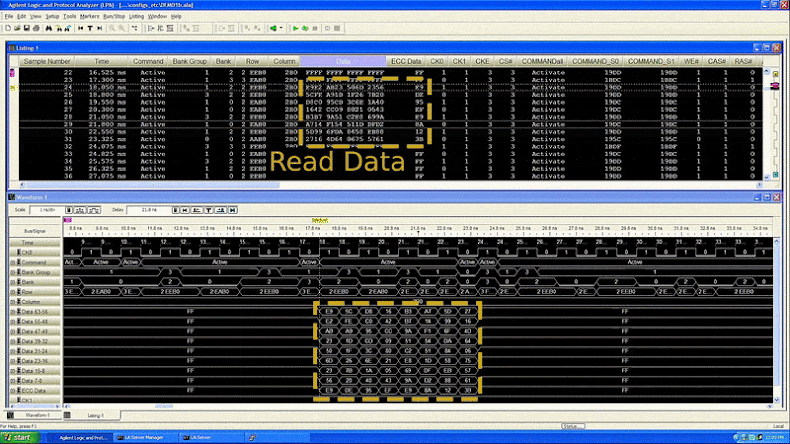
Mitigation and Intel’s Response
The researchers propose several defensive strategies:
- Abandon deterministic memory encryption
- Introduce more entropy per encryption block
- Encrypt attestation signatures internally
- Increase memory bus frequency
- Centralize key management across all enclaves
Intel was notified about the vulnerability in early 2025. After the study was published, Intel confirmed the issue but emphasized that the attack requires direct physical access and the installation of an interposer, conditions that fall outside the standard SGX threat model.
Editor’s Note
The method described here is presented solely for educational and research purposes. Red Dog Security does not endorse or assume responsibility for the use of these techniques outside legitimate security testing environments.


