Vulnerability Found in CyberVolk Ransomware Allows File Decryption

Pro-Russian hacktivist group CyberVolk launched a ransomware-as-a-service platform called VolkLocker (CyberVolk 2.x), but SentinelOne researchers discovered critical flaws that let victims recover files for free.
The attackers embedded the encryption master key directly in the malware's binary and saved it as a plain text file in the %TEMP% folder. The file, named system_backup.key, contains all information needed for data decryption. SentinelOne suspects this is a debugging artifact left in the malware before release. The RaaS operators appear unaware their clients are distributing builds with the backupMasterKey() function intact.
CyberVolk is a pro-Russian group believed to operate from India. Unlike other hacktivists who focus on DDoS attacks, CyberVolk aimed to create ransomware. The group first announced this plan last year and, despite multiple Telegram bans, presented VolkLocker and its RaaS platform in August 2025.
Technical Details
VolkLocker, written in Go, works on Linux (including VMware ESXi) and Windows. RaaS access for one operating system costs $800–$1,100, both versions cost $1,600–$2,200, and separate RAT or keylogger tools cost $500. Buyers access a Telegram bot constructor to configure ransomware and generate payloads.
Configuration requires a Bitcoin address, Telegram bot token, chat ID, ransom payment deadline, encrypted file extension, and self-destruct options.
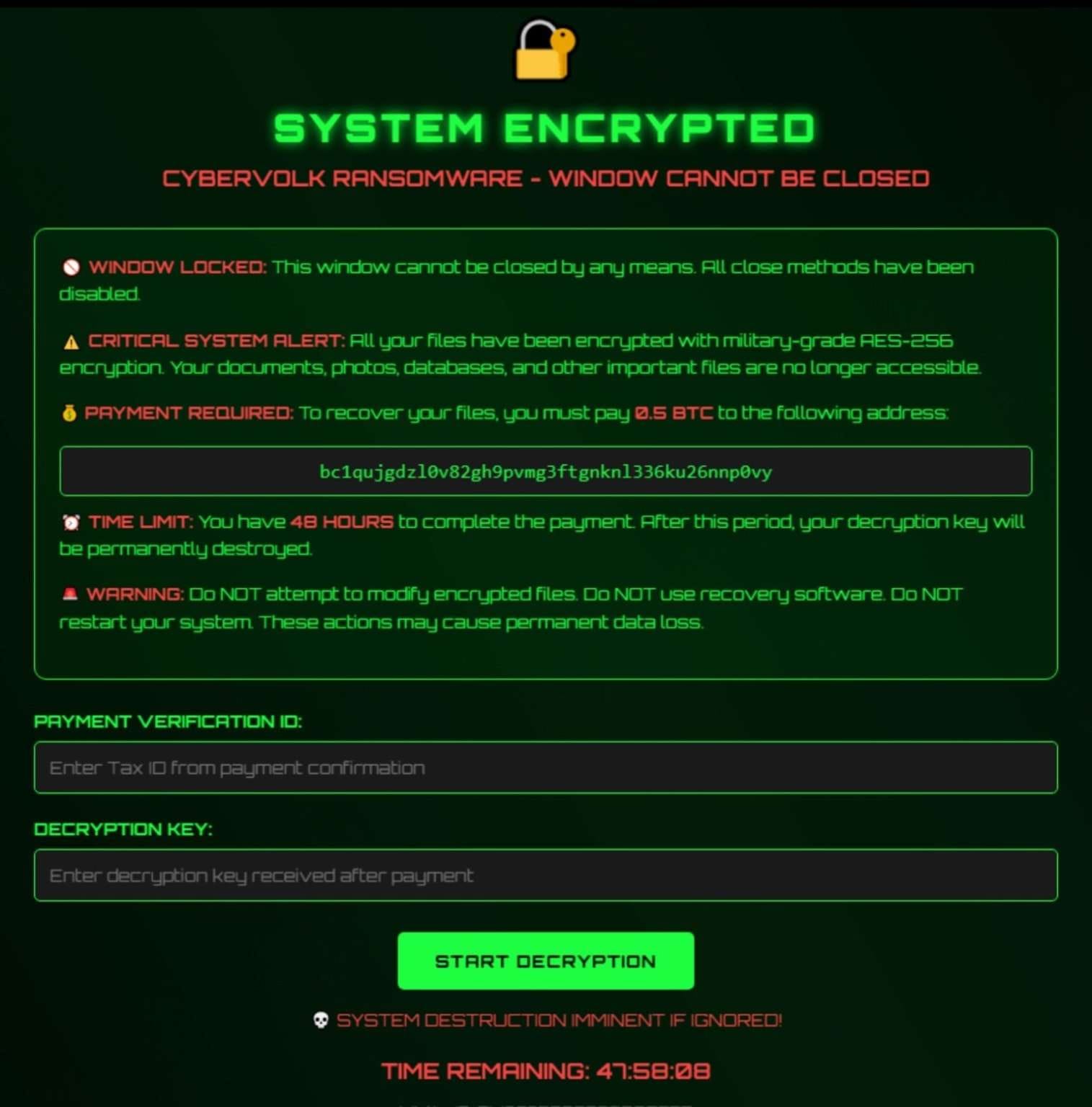
Once launched, VolkLocker elevates privileges (bypassing Windows User Account Control), selects files based on an exclusion list, and encrypts data using AES-256 in GCM mode. The code includes a timer that triggers a wiper, deleting user folders (Documents, Downloads, Pictures, Desktop) after the payment deadline expires or if victims enter an incorrect key.
Cryptographic Flaws
The malware's weakest element is its cryptography. VolkLocker doesn't generate keys dynamically but uses the same hard-coded master key for all files on infected systems. This key is written into the executable as a hex string and duplicated in a text file in %TEMP%.
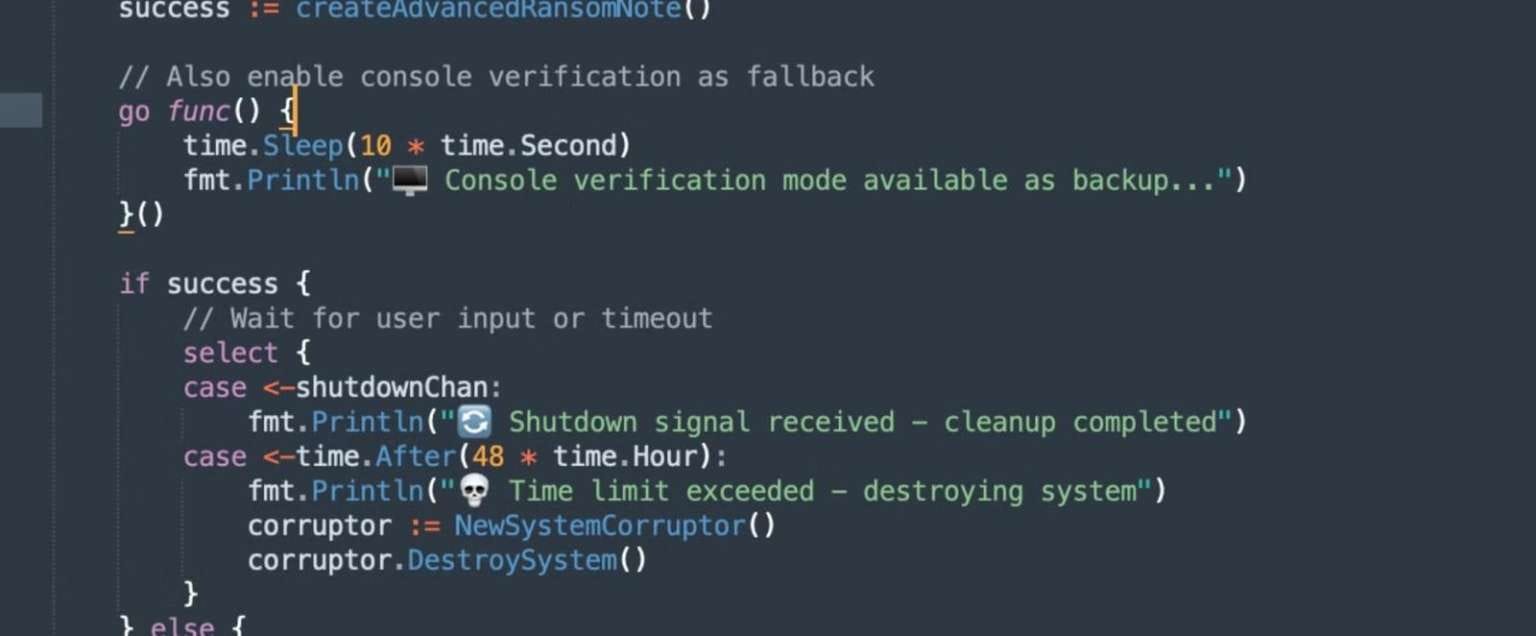
SentinelOne attributes these errors to quality control problems. The group is aggressively recruiting inexperienced "partners" but failing to manage basic operational security.
Typically, security researchers don't disclose ransomware vulnerabilities while attackers remain active. Instead, they notify law enforcement and ransom negotiation firms that can assist victims privately. SentinelOne explained that disclosing VolkLocker's flaws is unlikely to hinder law enforcement efforts against CyberVolk, since the group remains active.


