Unpatched Vulnerability in Gogs Leads to Compromise of 700 Servers

A zero-day vulnerability in the popular self-hosted Git repository service Gogs allows attackers to execute arbitrary code remotely, leading to the compromise of hundreds of servers worldwide.
Gogs is written in Go and is positioned as an alternative to GitLab or GitHub Enterprise. Many developers and companies make their Gogs instances accessible via the internet for remote project collaboration. However, this makes such servers easy targets for attacks, and researchers have now recorded a large-scale campaign exploiting a critical vulnerability.
The issue has been assigned the identifier CVE-2025-8110 and is related to a path traversal vulnerability in the service's PutContents API. The bug allows bypassing protection implemented for another remote code execution (RCE) issue (CVE-2024-55947), which developers had patched earlier. Per researchers, hackers learned to use symbolic links to overwrite files outside the repository.
The problem is that versions of Gogs where the CVE-2024-55947 vulnerability was fixed now validate file paths to prevent directory traversal. However, these checks do not account for symbolic links. As a result, attackers can create a repository with symlinks pointing to important system files and then use the PutContents API to write data through this link, overwriting files as they choose. By overwriting Git configuration files, specifically the sshCommand parameter, hackers can force the target system to execute arbitrary commands.
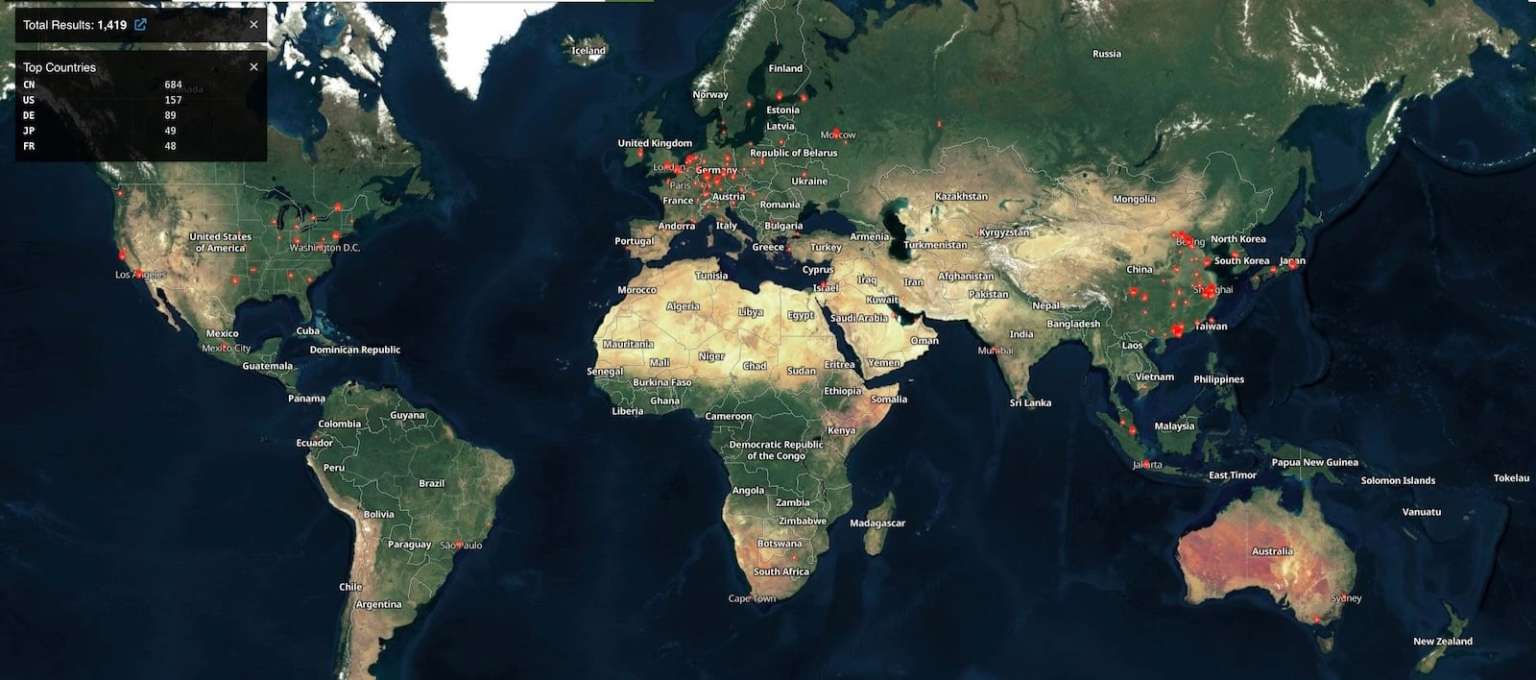
Researchers from Wiz discovered the new vulnerability in July 2025 while studying malware on a Gogs server belonging to one of their clients. Further analysis showed that more than 1,400 publicly accessible Gogs servers can be found on the internet, with over 700 of them showing signs of compromise. All compromised instances discovered during the investigation show the same pattern: repositories with random eight-character names, created around the same time (in July 2025). This suggests that a single threat actor or group using automated tools is behind the malicious campaign.
"During scanning, we discovered over 1,400 publicly accessible Gogs servers. Many of them run with the default Open Registration setting enabled, creating a large attack surface," the researchers reported.
Wiz researchers also found that the malware deployed on the servers was created using Supershell—an open-source C2 framework that establishes reverse SSH shells through web services. Additional analysis showed that the malware communicates with a command-and-control server at the address 119.45.176[.]196.
Researchers reported the issue to Gogs maintainers on July 17. The maintainers confirmed the vulnerability on October 30 and stated they were working on a patch. Per the timeline published by the Wiz team, a second wave of attacks began on November 1, 2025.
Since a fix is not yet available, Gogs users are advised to immediately disable the default Open Registration setting and restrict server access. To check if an instance has been compromised, look for suspicious activity related to the PutContents API and repositories with random eight-character names.