Tomiris Attacks Diplomatic Services and Government Institutions in Russia and CIS

Researchers from Kaspersky Lab discovered recent activity by the APT group Tomiris, which has been attacking the government sector in Russia and CIS countries since early 2025. The group's primary victims are foreign ministries and other diplomatic structures. Over the past year, more than 1,000 users have encountered Tomiris activity.
Tomiris activity was first documented in 2021. Previously, the group attacked state institutions in the CIS, with the main goal being the theft of internal documents.
Attack Vector
Hacker attacks typically begin with phishing emails containing password-protected archives. Inside the attachments is an executable file disguised as a document: either with a double extension like .doc[spaces].exe, or with a long name that hides the real extension when viewing the archive. One example of a lure is an email requesting feedback on projects allegedly aimed at developing Russian regions. Running the file from the archive leads to infection.
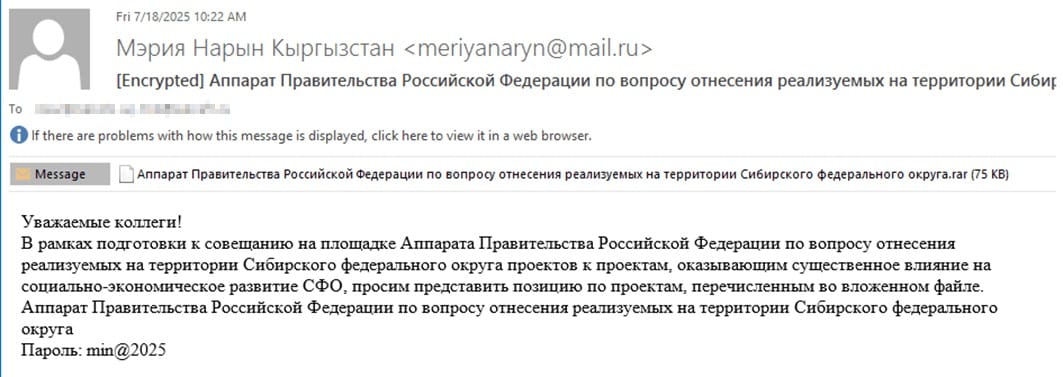
More than half of the targeted phishing emails and lure files in the 2025 campaign contained text in Russian. Based on this, specialists conclude that the group's primary targets were Russian-speaking users and organizations. The remaining emails were adapted for Turkmenistan, Kyrgyzstan, Tajikistan, and Uzbekistan and were composed in the respective languages.
Malware Arsenal
To penetrate victims' systems, the group uses various types of malware. In most cases, infection begins with the deployment of reverse shells (written in C/C++, C#, Go, Rust, and Python), awaiting further commands. Some of these use Discord and Telegram as command-and-control servers, and the attackers attempt to disguise malicious traffic as legitimate activity from these popular services.
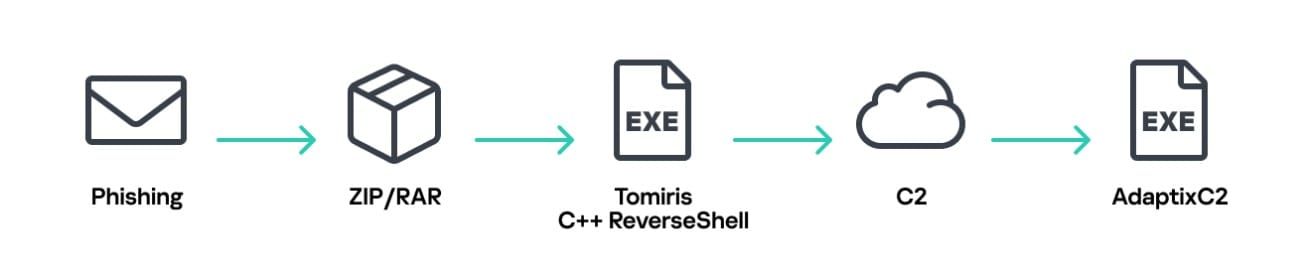
In subsequent attack stages, the malware installs additional tools, including the AdaptixC2 and Havoc frameworks, for further exploitation and persistence in the system. For lateral movement across the target network, reverse SOCKS proxies based on public GitHub projects are typically used.
Data Exfiltration
The malware searches infected devices for confidential data. Hackers are interested in files with the extensions .jpg, .jpeg, .png, .txt, .rtf, .pdf, .xlsx, and .docx.
One of the group's malware strains (Tomiris Rust Downloader) does not download the contents of files directly but only sends a list of their paths to Discord. Other tools, like the Tomiris Python FileGrabber, pack found documents into ZIP archives and transmit them to the command-and-control server via HTTP POST.
Expert Analysis
"Tomiris's tactics have clearly evolved: they are aimed at maximizing the concealment of malicious activity and establishing long-term persistence in the system. This is facilitated in part by the use of malicious implants written in different languages. The group has increasingly relied on tools that utilize publicly accessible services like Telegram and Discord as command servers. Most likely, this is how the attackers attempt to hide malicious traffic among the legitimate activity of these services," stated Oleg Kupreev, a cybersecurity expert at Kaspersky Lab.


