The RondoDox Botnet Exploits 56 Vulnerabilities Across Dozens of Devices
Security researchers have uncovered a large-scale botnet dubbed RondoDox, which exploits 56 vulnerabilities across more than 30 types of internet-connected devices — including flaws first demonstrated at the Pwn2Own hacking competition.
The campaign targets a wide spectrum of hardware such as digital and network video recorders (DVRs/NVRs), IP cameras, and web servers. According to Trend Micro, the botnet relies on what they call an “exploit shotgun” approach — simultaneously launching multiple exploits to maximize infections, even though this noisy tactic often attracts attention from defenders.
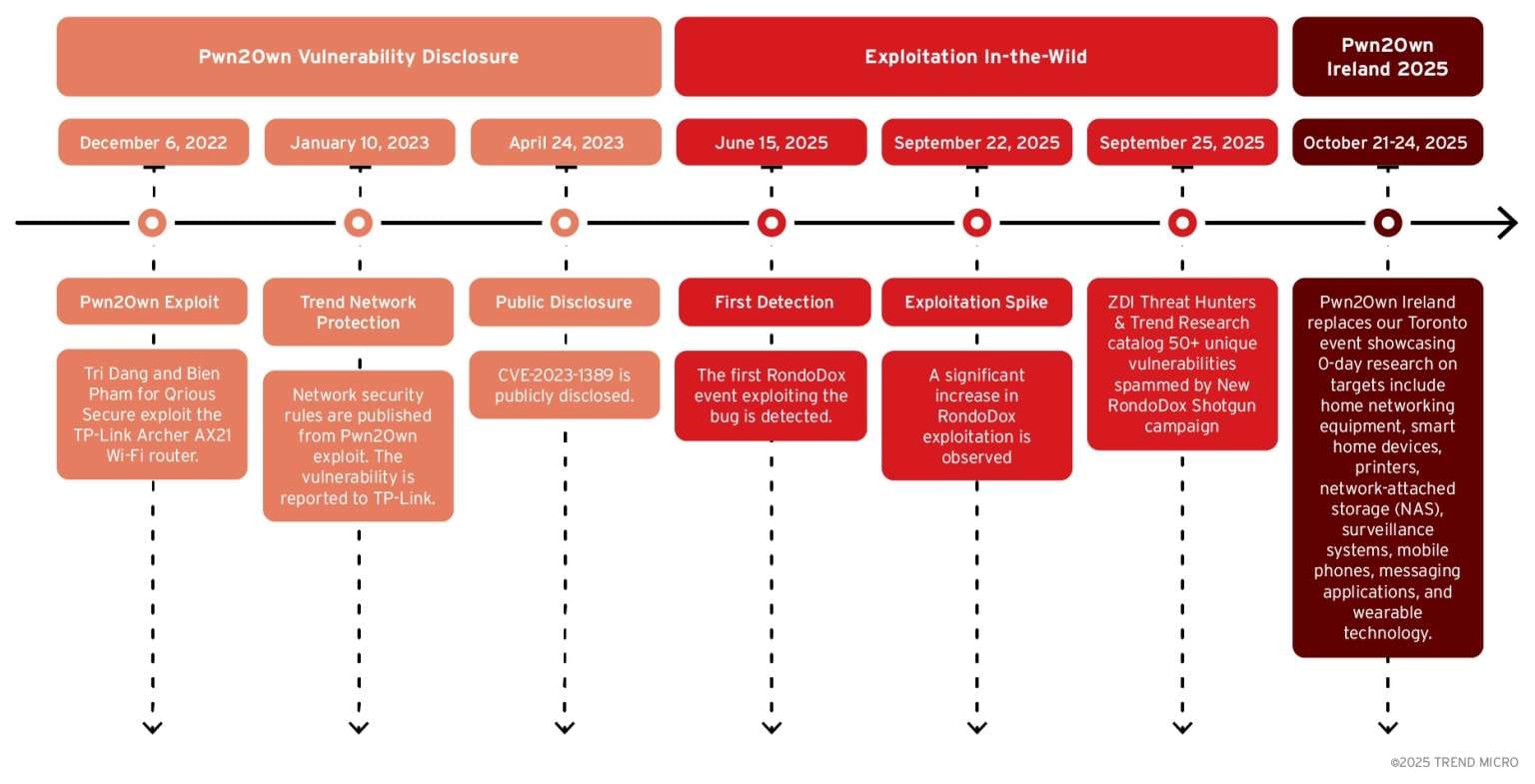
Pwn2Own Exploits Go Live
RondoDox developers closely follow the release of Pwn2Own proofs-of-concept, often integrating them into attacks within weeks. For instance, the botnet has been observed exploiting CVE-2023-1389, a TP-Link Archer AX21 router vulnerability first demonstrated at Pwn2Own Toronto 2022.
Researchers have also identified dozens of n-day exploits in the botnet’s arsenal, targeting major vendors and IoT brands:
- Digiever: CVE-2023-52163
- QNAP: CVE-2023-47565
- LB-LINK: CVE-2023-26801
- TRENDnet: CVE-2023-51833
- D-Link: CVE-2024-10914
- TBK: CVE-2024-3721
- Four-Faith: CVE-2024-12856
- Netgear: CVE-2024-12847
- AVTECH: CVE-2024-7029
- TOTOLINK: CVE-2024-1781 / CVE-2025-1829 / CVE-2025-5504
- Tenda: CVE-2025-7414
- Meteobridge: CVE-2025-4008
- Edimax: CVE-2025-22905
- Linksys: CVE-2025-34037
- TP-Link: CVE-2023-1389
Exploiting the Old and the Neglected
Trend Micro researchers warn that outdated devices remain a major security gap, as many have reached end-of-life status and no longer receive patches. But even supported devices are vulnerable when users fail to apply firmware updates after the initial setup — a common oversight in both home and enterprise networks.
Beyond the known CVEs, RondoDox also exploits at least 18 unassigned command-injection vulnerabilities, affecting D-Link NAS units, TVT and LILIN DVRs, Fiberhome routers, ASMAX devices, Linksys hardware, and Brickcom cameras.
DDoS Attacks Disguised as Gaming Traffic
According to FortiGuard Labs, RondoDox is capable of launching HTTP, UDP, and TCP-based DDoS attacks. To evade detection, it disguises its malicious traffic as that of popular gaming and communication platforms — including Valve, Minecraft, Dark and Darker, Roblox, DayZ, Fortnite, and GTA, as well as legitimate software such as Discord, OpenVPN, WireGuard, and RakNet.
This camouflage allows the botnet to blend into ordinary traffic patterns, complicating network-level detection.
Defense Recommendations
To defend against RondoDox and similar IoT botnets, researchers recommend the following steps:
- Install the latest firmware available from device manufacturers.
- Replace end-of-life devices that no longer receive security updates.
- Segment the network, isolating critical assets from IoT and guest devices.
- Change default credentials and enforce strong, unique passwords.
The Bigger Picture
The discovery of RondoDox underscores the continued weaponization of IoT vulnerabilities and the security community’s struggle to keep pace with the rapid reuse of Pwn2Own exploits.
As Trend Micro notes, RondoDox’s scale and agility demonstrate how attackers turn public research into mass exploitation — transforming proof-of-concept vulnerabilities into full-blown botnets within months.


