The Herodotus Trojan: Banking Malware That Types Like a Human to Beat Detection

A new banking Trojan called Herodotus has emerged in Italy and Brazil, and it brings something we haven't seen before in Android malware: the ability to mimic human typing patterns to fool behavioral analysis systems.
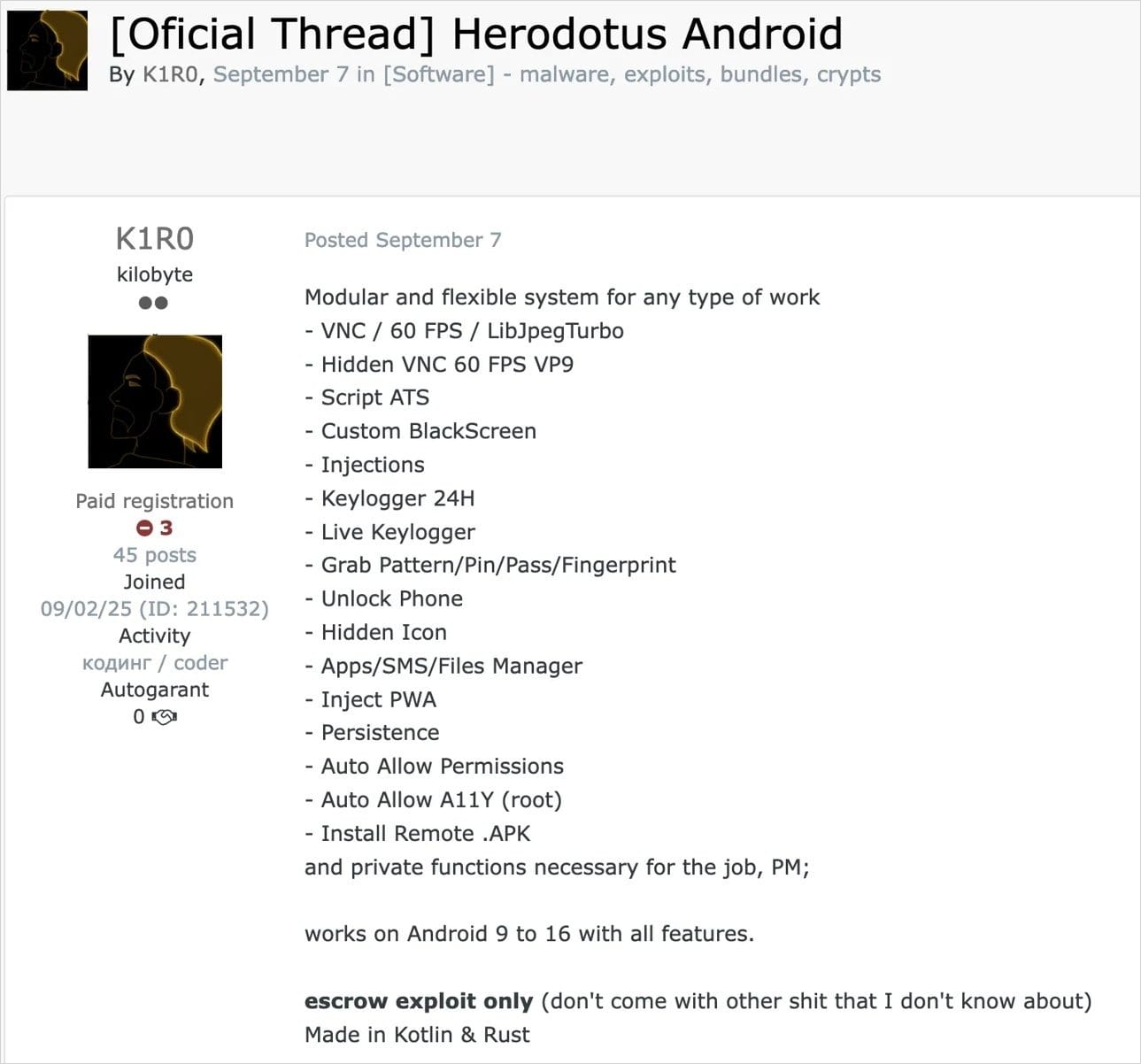
ThreatFabric researchers first spotted Herodotus advertised on hacker forums on September 7, 2025, operating as malware-as-a-service (MaaS). The developers claim it works on Android versions 9 through 16, casting a wide net across current devices.
Connection to Brokewell
While Herodotus isn't a direct successor to the Brokewell banking Trojan, the connection is clear. Researchers found similar obfuscation techniques and direct code references to Brokewell, including the string "BRKWL_JAVA" embedded in the malware. This suggests the developers either worked on Brokewell previously or studied its code extensively.
How Herodotus Spreads
The Trojan reaches victims through dropper applications disguised as Google Chrome (using the package name com.cd3.app). Attackers distribute these fake apps via SMS phishing and other social engineering tactics. Once installed, Herodotus exploits Android Accessibility services to take complete control of the infected device.
Core Capabilities
After gaining access, Herodotus can:
- Interact with screen elements and UI controls
- Display opaque overlays to hide malicious activity from the user
- Show fake login screens over legitimate banking applications
- Intercept SMS messages containing two-factor authentication codes
- Record everything displayed on the screen
- Automatically grant itself any permissions it needs
- Steal PIN codes and screen lock patterns
- Remotely install additional APK files
The Human Touch: Beating Behavioral Analysis
Here's what makes Herodotus particularly dangerous: it deliberately types like a human to evade detection.
Many banks and financial institutions now use behavioral analysis systems that monitor characteristic patterns of human actions—typing speed, finger movements, delays between keystrokes. These systems can spot automated attacks because machines typically type at consistent, rapid speeds that real people don't match.
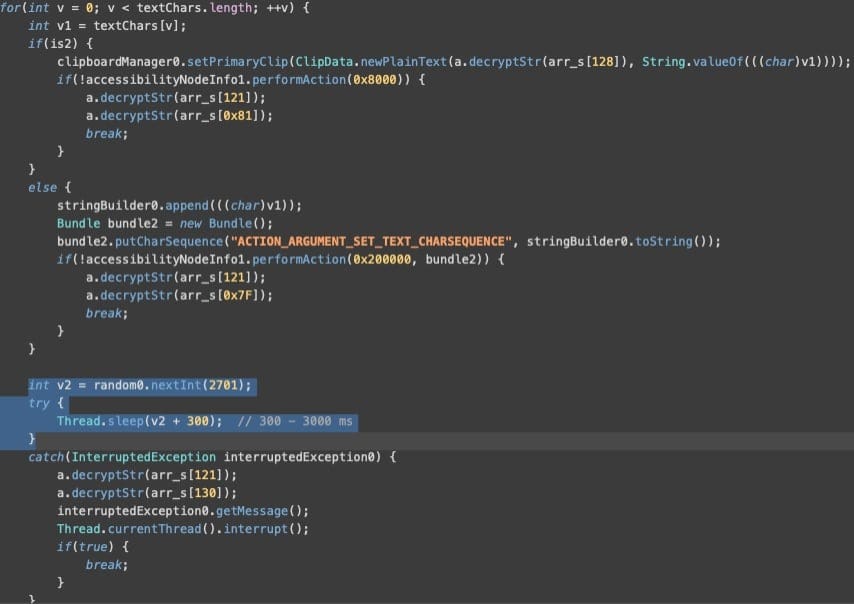
Herodotus counters this by adding random delays between 300 and 3,000 milliseconds (0.3 to 3 seconds) when entering text remotely. "This randomization of delays corresponds to how a live person types text," ThreatFabric explains. "The attackers consciously slow down the input using random intervals to avoid detection by anti-fraud solutions that detect machine-like typing speeds."
This represents the first documented case of Android malware specifically designed to trick behavioral analysis defenses.
Expanding Reach
While Herodotus initially targeted users in Italy and Brazil, researchers have already discovered overlays for banks and financial organizations in the United States, Turkey, the United Kingdom, and Poland. The malware operators also show interest in cryptocurrency wallets and exchanges, signaling plans for broader attacks.
What This Means
"The Trojan is under active development, borrows techniques from Brokewell, and is created not for simple theft of static credentials, but for maintaining active sessions with a focus on account takeover," ThreatFabric researchers conclude.
In other words, Herodotus isn't just stealing passwords—it's taking over active banking sessions, making it far more dangerous. The human-like typing behavior means traditional behavioral defenses may miss it entirely.
For users, this reinforces the importance of only downloading applications from official app stores, being skeptical of unsolicited SMS messages, and monitoring device permissions carefully. For security professionals, Herodotus signals that attackers are adapting to behavioral analysis defenses, and detection systems will need to evolve accordingly.


