The Cavalry Werewolf Group is Attacking Russian Government Institutions

In July 2025, Doctor Web specialists investigated an incident at a Russian Federation state institution where unwanted emails were being sent from a corporate mailbox. What started as a seemingly simple email compromise investigation revealed something far more serious: a targeted attack by the hacker group Cavalry Werewolf, aimed at collecting confidential information and network configuration data.
This case demonstrates how modern APT (Advanced Persistent Threat) groups operate not through sophisticated zero-day exploits, but through patient, methodical approaches using modified open-source tools and social engineering.
The Initial Compromise: Classic Phishing with a Twist
The attack began with a phishing campaign that followed established patterns. The attackers sent emails posing as government bodies using compromised email addresses—meaning they weren't creating fake domains, but had actually breached legitimate government mailboxes to send their messages.
These emails contained password-protected archives. The password protection served a dual purpose: it bypassed automated email security scans that can't inspect encrypted files, and it added perceived legitimacy since government communications often arrive in protected formats.
Inside these archives was a previously unknown backdoor BackDoor.ShellNET.1, based on the open-source Reverse-Shell-CS project. The malware was disguised as documents with convincing names like "Service Memorandum dated 16.06.2025" or "List of Participants for the Public Reception Event."
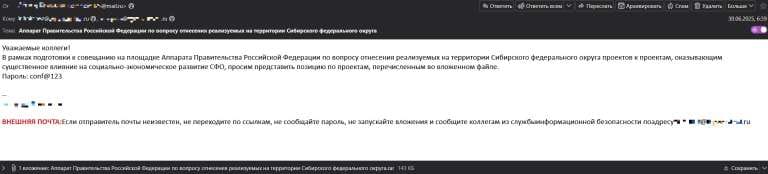
In my opinion, the use of specific dates and realistic document names shows careful reconnaissance. These weren't generic phishing attempts the attackers understood their targets' workflows and created lures that would seem routine and expected.
Establishing Remote Access
Upon execution, the malware established a remote connection to the infected computers via a reverse shell, allowing the execution of commands. This gave the attackers direct access to run whatever they needed on the compromised system.
Using this initial foothold, the hackers downloaded additional tools via Bitsadmin, a legitimate Windows utility designed for managing file transfers. This is a common tactic in modern attacks: use the victim's own administrative tools rather than dropping suspicious executables that security software might flag.
Data Theft and Covert Communication
The first component downloaded was the stealer Trojan.FileSpyNET.5, which targeted specific file types: documents in .doc, .docx, .xlsx, and .pdf formats, text files, and images. The attackers weren't grabbing everything they were selectively stealing the types of files most likely to contain valuable intelligence.
Then they installed the backdoor BackDoor.Tunnel.41, based on the open-source ReverseSocks5 project. This created SOCKS5 tunnels for covert connections to the infected system. Think of this as building a secret tunnel into the network that looks like normal traffic to security monitoring tools.
The Trojanized Application Strategy
Cavalry Werewolf employs a particularly clever tactic: they take popular, trusted applications and embed malicious code into them. The researchers documented modifications of programs like WinRar, 7-Zip, Visual Studio Code, AkelPad, and even the Sumatra PDF Reader. In one case, they disguised a trojanized PDF reader as the MAX messenger application.
When victims launch these programs, they lose their primary functionality the PDF reader doesn't read PDFs, the archive tool doesn't extract files. Instead, the programs initialize only the malicious components hidden inside.
These trojanized applications can contain various backdoors and malware, including:
- BackDoor.ReverseProxy.1 (based on ReverseSocks5) for creating covert tunnels
- BackDoor.Shell.275 and BackDoor.AdaptixC2.11 (both based on AdaptixC2) for command execution
- BackDoor.Havoc.16 (based on Havoc framework) for post-exploitation
- BackDoor.Meterpreter.227 (based on CobaltStrike) for advanced control
- Cryptocurrency-stealing clippers that monitor clipboard for wallet addresses
This approach is effective because users expect to see these programs on their systems. A security analyst reviewing running processes might not find "WinRar.exe" suspicious—even though this particular version is actually a backdoor.
Telegram as Command and Control
The attackers actively use the Telegram API to manage infected systems via bots. This functionality appears in several of their backdoors: BackDoor.Siggen2.5463, BackDoor.ShellNET.2, and Trojan.Clipper.808.
Using Telegram for command and control is increasingly common among APT groups. It offers several advantages: the traffic looks like normal social media usage, it's encrypted, it's available globally, and it provides a simple interface for operators to send commands and receive stolen data.
Reconnaissance and Persistence
After successfully gaining initial access, the hackers follow a standard reconnaissance playbook. They gather information about the victim's system using built-in Windows commands:
whoamito identify the current user and privilegesipconfig /allto map network configurationnet userto enumerate user accounts
They check network and proxy server configurations via curl and PowerShell. Throughout this process, they rely on legitimate Windows tools—PowerShell, Bitsadmin, and curl—to download additional components. This "living off the land" approach minimizes detection risk.
Persistence in the system is achieved through two methods: modifying the Windows Registry to create autostart entries, and placing malicious files in directories that users and administrators might not regularly inspect, such as:
C:\users\public\picturesC:\users\public\librariesC:\users\public\downloads
These public folders are often overlooked during security audits because they're shared locations that might contain legitimate files from multiple users.
Cavalry Werewolf's Signature Characteristics
The Doctor Web researchers identified several characteristics typical of Cavalry Werewolf operations:
First, heavy reliance on open-source tools. The group uses both unmodified open-source software and customized versions as the foundation for their operations. This approach offers several benefits: the tools are already tested and functional, the source code is available for modification, and attribution becomes harder when everyone has access to the same base code.
Second, preference for reverse shell backdoors. Their primary toolkit consists of backdoors that establish reverse connections from the victim's network outward. This bypasses many firewall configurations that block incoming connections but allow outbound traffic.
Third, embedding malicious code into legitimate applications. By trojanizing popular programs, they hide their activity within expected system processes. This makes detection significantly harder and gives them persistence that survives casual inspection.
Fourth, Telegram API integration for command and control. Using a legitimate messaging platform makes their command traffic blend with normal user activity.
Fifth, phishing emails sent from compromised government mailboxes. Rather than spoofing addresses, they actually breach legitimate accounts and send from those. This defeats email authentication mechanisms like SPF, DKIM, and DMARC that are designed to catch spoofed messages.
Sixth, continuous arsenal expansion and adaptation. The group doesn't rely on a static toolkit. They continuously develop new tools and adapt existing ones for specific targets.
The Bigger Picture: Targeted Government Espionage
The Doctor Web experts conclude that Cavalry Werewolf carries out planned, targeted attacks on the Russian government sector with the goal of long-term cyber espionage and the collection of confidential data.
This is not opportunistic cybercrime. The group isn't deploying ransomware or stealing credentials for resale. They're conducting deliberate intelligence collection operations against government institutions—the kind of activity typically associated with nation-state actors or groups working on behalf of nation-states.
The use of compromised government email accounts to send phishing messages shows deep penetration of their target environment. They're not just attacking from the outside—they've already compromised parts of the network and are using that access to expand their reach.
What This Means for Defenders
If you're defending government networks or critical infrastructure, this case study offers several important lessons:
First, email security needs to look beyond sender authentication. When attackers use legitimately compromised accounts, traditional email security measures fail. You need behavioral analysis that can detect unusual sending patterns even from valid accounts.
Second, application whitelisting isn't enough if the applications themselves are compromised. Allowing "WinRar.exe" to run seems reasonable, but what if that executable has been replaced with a trojanized version? You need integrity checking that verifies applications haven't been modified.
Third, monitoring for legitimate administrative tools used in unusual contexts is essential. PowerShell, Bitsadmin, and curl are all valid Windows components, but when they're being used to download files from external IPs at 3 AM, that should trigger alerts.
Fourth, public folders need security attention. Directories like C:\users\public\pictures are often ignored in security audits but provide convenient hiding spots for attackers.
Fifth, outbound connections to messaging platforms like Telegram should be scrutinized. If government workstations are making regular connections to Telegram servers, someone needs to verify that's for legitimate purposes and not command and control traffic.
The Open-Source Intelligence Paradox
One interesting aspect of this case is Cavalry Werewolf's heavy reliance on open-source tools. Projects like Reverse-Shell-CS, ReverseSocks5, AdaptixC2, Havoc, and CobaltStrike are all publicly available. Anyone can download them, study them, and modify them.
This creates a challenge for both attackers and defenders. For attackers, it means their tools might be well-known to security researchers. For defenders, it means attribution becomes nearly impossible—when everyone has access to the same base code, how do you determine who's behind a specific attack?
Furthermore, it raises questions about the responsibility of open-source security tool developers. These projects are created for legitimate penetration testing and red team operations. But they're also being used by APT groups targeting government institutions. Where's the line between providing useful security research tools and arming potential attackers?
I don't have a good answer to that question. Restricting access to security tools wouldn't stop sophisticated groups—they'd just develop their own. But the current situation, where nation-state level capabilities are available for download on GitHub, isn't ideal either.
Conclusion
The Cavalry Werewolf attacks on Russian government institutions demonstrate how modern APT operations work: patient reconnaissance, carefully crafted social engineering, extensive use of open-source tools, and persistence through legitimate-looking processes.
The group's success comes not from sophisticated zero-day exploits, but from understanding their targets, using compromised legitimate accounts for initial access, hiding in plain sight with trojanized common applications, and leveraging built-in Windows tools that security software won't flag.
For defenders, this case reinforces that protecting against APT groups requires looking beyond traditional security measures. You need behavioral analysis that can detect unusual patterns even when the tools and accounts being used are legitimate. You need integrity checking that verifies applications haven't been modified. You need monitoring that can distinguish between normal administrative activity and attacker reconnaissance.
The attacks are ongoing. The group continues to expand its arsenal and adapt its tools for specific targets. And as long as government institutions remain attractive intelligence targets, groups like Cavalry Werewolf will continue developing new techniques to compromise them.


