StealC Infostealer Found in Blender Model Files
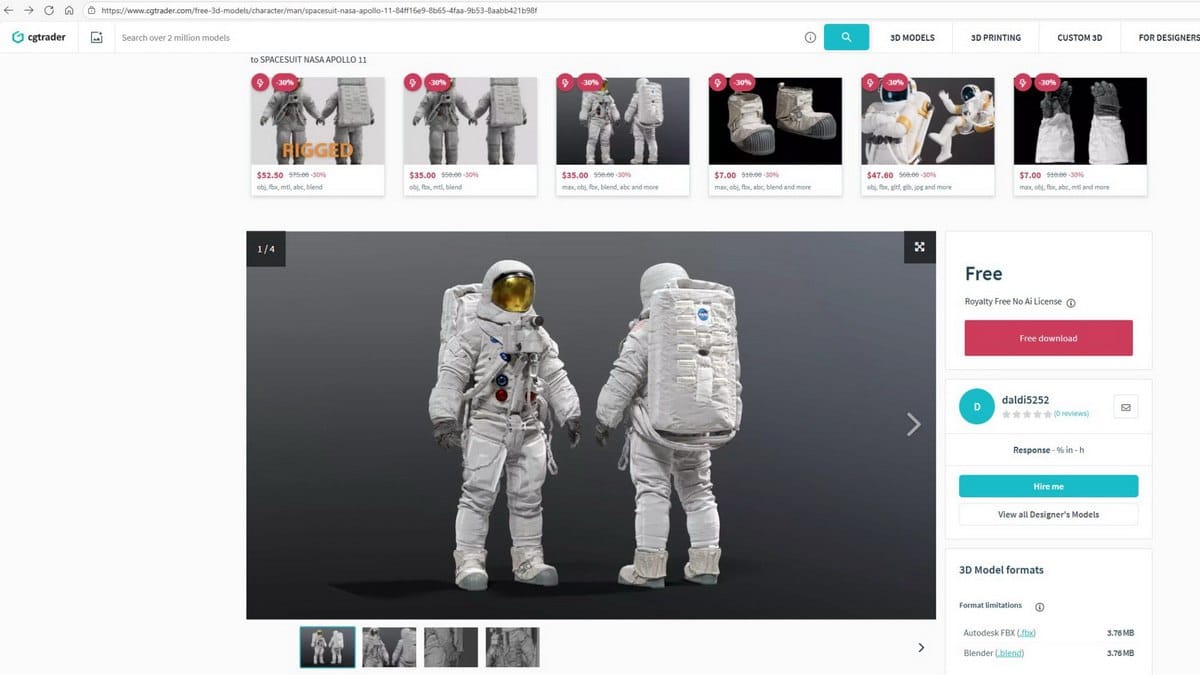
Researchers at Morphisec discovered a malicious campaign in which attackers are distributing the StealC V2 infostealer through infected files for the Blender 3D editor, uploading the malware to marketplaces like CGTrader.
Blender's Vulnerability Surface
Blender is a popular open-source project for creating 3D graphics. The software supports execution of Python scripts for automation, creating custom interface panels, add-ons, configuring rendering processes, and integration into development pipelines.
If the Auto Run function is enabled, opening a file with a character rig can automatically load facial animation controls and custom panels with the necessary buttons and sliders. Despite the risks, users often enable this option for convenience.
Attack Chain
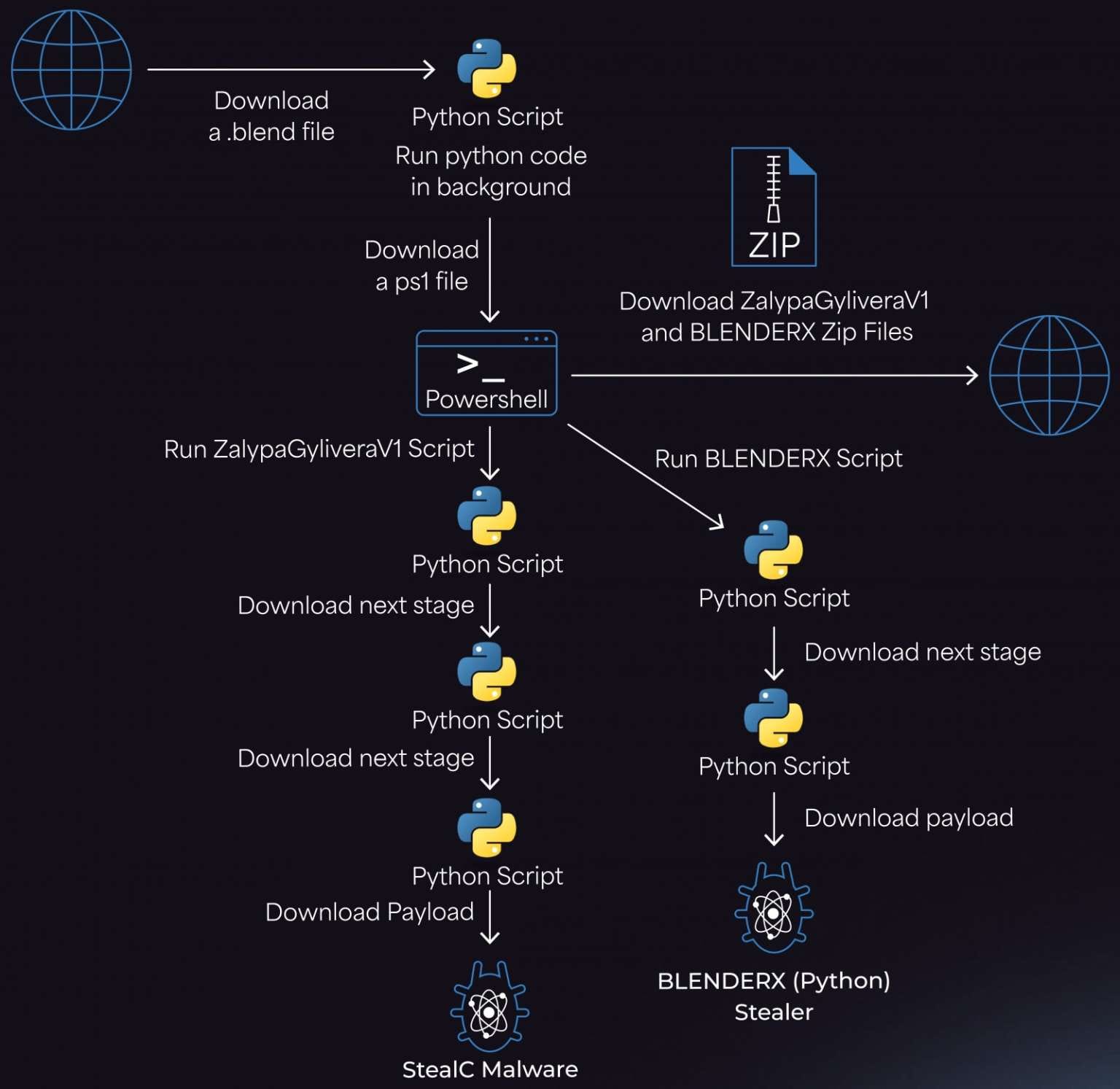
Per Morphisec specialists, the attacks use malicious .blend files with embedded Python code that loads a malware loader from a Cloudflare Workers domain. This loader then downloads a PowerShell script, which fetches two ZIP archives from the attackers' infrastructure—ZalypaGyliveraV1 and BLENDERX.
The archives are unpacked in the %TEMP% folder and create LNK files in the startup directory for persistence. After that, two payloads are deployed: the StealC infostealer and an auxiliary Python stealer, which likely serves as a backup solution.
StealC V2 Capabilities
This campaign uses the latest modification of the StealC version 2 stealer, which was previously analyzed by Zscaler experts earlier this year.
The newest StealC features enhanced information theft capabilities and supports data exfiltration from:
- 23+ browsers with server-side credential decryption and compatibility with Chrome 132 and above
- 100+ browser crypto extensions and 15+ desktop cryptocurrency wallets
- Telegram, Discord, Tox, Pidgin, VPN clients (ProtonVPN, OpenVPN), and mail clients (Thunderbird)
The new malware version also includes an updated UAC (User Account Control) bypass mechanism.
Detection Challenges
Although this malware was first documented in 2023, subsequent releases and updates have made it nearly undetectable for antivirus programs. Per Morphisec, no product on VirusTotal detected the specific StealC variant they analyzed.
Security Recommendations
Given that 3D model marketplaces cannot verify the code within files uploaded by users, Blender users should exercise caution when using assets from such platforms and disable auto-execution of code.
3D assets should be treated as executable files. Users should only trust verified publishers with good reputations. For all other assets, researchers recommend using isolated environments.