Spyware LandFall Attacked Samsung Devices via WhatsApp Messages

Researchers from Palo Alto Networks have discovered previously unknown spyware called LandFall that exploited a zero-day vulnerability in Samsung devices. The attacks started in at least July 2024, with hackers distributing the malware through malicious images sent via WhatsApp.
The Target and the Vulnerability
The attackers targeted specific users of Samsung Galaxy devices in the Middle East. They exploited a critical vulnerability, CVE-2025-21042 (CVSS score 8.8), in the image processing library libimagecodec.quram.so. This flaw allowed arbitrary code execution on the target device through an out-of-bounds write. Samsung didn't patch this issue until April 2025—meaning the malware operated undetected for approximately nine months.
How the Attack Worked
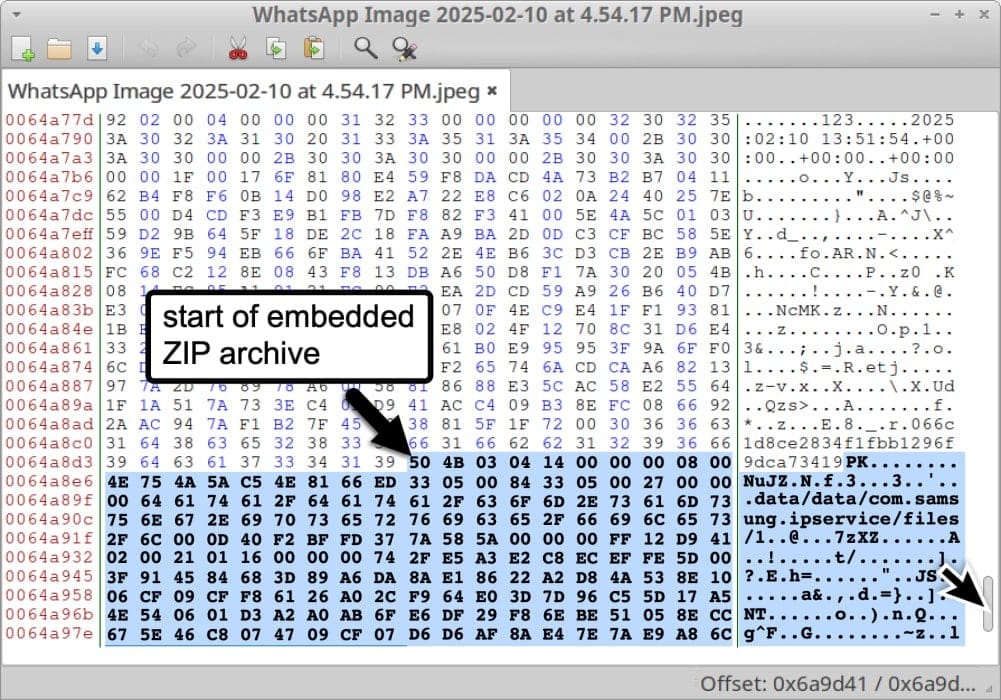
The attack began with a specially crafted .DNG format image sent via WhatsApp. Hackers hid a ZIP archive containing malicious components inside the image. When the victim received the file, the exploit triggered automatically during the system's image processing—no user interaction required beyond receiving the message.
Samples of the malicious files used by LandFall first appeared on VirusTotal on July 23, 2024. In all cases, they were linked to WhatsApp as the distribution channel. VirusTotal data shows victims were located in Iraq, Iran, Turkey, and Morocco.
Technical Components
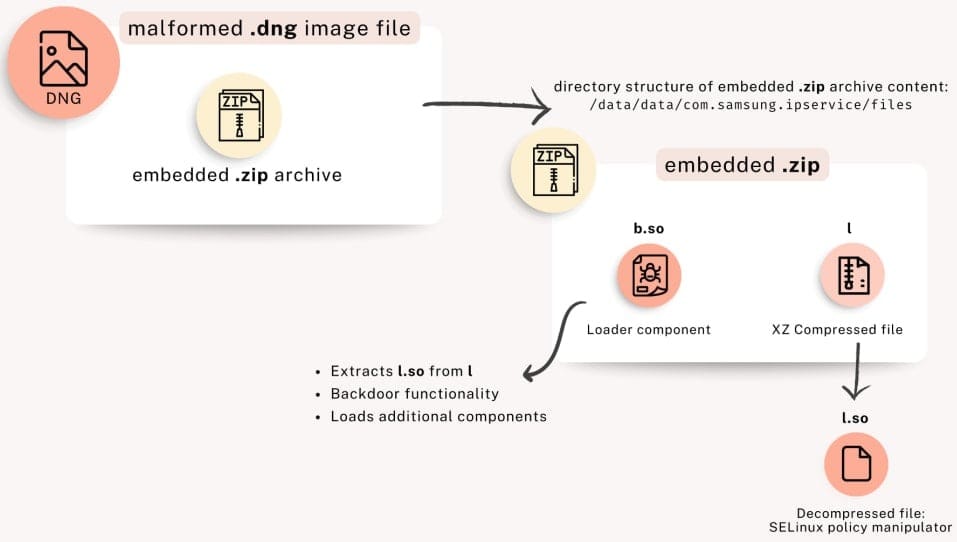
LandFall spyware consists of two key modules:
- Loader (
b.so) — Downloads and launches additional components - SELinux policy modification component (
l.so) — Alters security settings for privilege escalation and persistence on the system
Surveillance Capabilities
LandFall collects a complete digital fingerprint of the device: IMEI, IMSI, SIM card number, account data, Bluetooth information, geolocation, and the list of installed applications. The spyware can also:
- Record audio from the device's microphone and phone calls
- Track the victim's location in real-time
- Steal photos, contacts, SMS, and call logs
- Access files and browser history
- Download and execute additional modules
- Evade detection and bypass protection mechanisms
Affected Devices
The victims owned Samsung Galaxy S22, S23, and S24 series devices, as well as the foldable Z Fold 4 and Z Flip 4 models. The latest S25 series devices were not affected.
Infrastructure and Attribution
Researchers identified six command-and-control servers associated with this campaign. Some have already been flagged as malicious by Turkish CERT.
The researchers believe LandFall is a commercial framework for targeted surveillance, but precise attribution hasn't been established. However, the C2 server infrastructure resembles that used by the hack group Stealth Falcon from the UAE. Furthermore, the name of the loader component (Bridge Head) matches naming patterns typically seen in spyware from developers like NSO Group, Variston, Cytrox, and Quadream.
Part of a Broader Pattern
LandFall isn't the only spyware exploiting DNG format images in attacks. Similar attack chains have previously targeted iOS users (CVE-2025-43300) and WhatsApp (CVE-2025-55177).
What This Means
In my opinion, this discovery highlights several concerning trends in the commercial spyware industry. First, the nine-month window between initial exploitation and Samsung's patch demonstrates how zero-day vulnerabilities give attackers a substantial operational advantage. During those nine months, targets had no defense—their devices were compromised simply by receiving a WhatsApp message.
Furthermore, the attack method is particularly insidious because it requires no user interaction beyond receiving a message. The victim doesn't need to click a link, open an attachment, or install anything. The exploit triggers during automatic image processing, making it nearly impossible for users to protect themselves through cautious behavior.
The targeting of Middle Eastern users, combined with infrastructure similarities to UAE-linked groups, suggests this was likely government-sponsored surveillance. The fact that LandFall resembles commercial spyware from NSO Group and similar vendors indicates a growing marketplace for these capabilities. These aren't hobbyist hackers—they're professional surveillance vendors selling sophisticated tools to government clients.
The use of WhatsApp as a distribution channel is also significant. WhatsApp's end-to-end encryption doesn't protect against this type of attack because the vulnerability exists in the device's image processing, not in WhatsApp's encryption. This means even security-conscious users who rely on encrypted messaging remain vulnerable to device-level exploits.
Recommendations
If you own a Samsung Galaxy device from the S22, S23, or S24 series, or a Z Fold 4 or Z Flip 4, ensure your device has received Samsung's April 2025 security update. Check your device's security patch level in Settings > About Phone > Software Information.
Be aware that simply using encrypted messaging apps doesn't guarantee protection against sophisticated spyware. Device-level security updates are just as important as application-level security.
Organizations operating in regions where targeted surveillance is common should implement additional security measures, including regular security audits of mobile devices used by executives and sensitive personnel.


