Sophisticated Android Backdoor Hijacks 58,000+ Telegram Accounts Through Fake Apps

Baohuo malware hides in modified Telegram X apps, giving attackers complete control while remaining invisible to victims
Security researchers have uncovered a sophisticated Android backdoor targeting Telegram users in Brazil and Indonesia, marking the first known case of malware using Redis databases for command-and-control operations on mobile devices.
The malware, dubbed Baohuo, has infected over 58,000 devices since mid-2024 by masquerading as legitimate versions of Telegram X—a popular alternative Telegram client. What makes this threat particularly dangerous is its ability to operate completely invisibly while granting attackers full control over victims' accounts.
Hidden in Plain Sight
Doctor Web analysts discovered the backdoor embedded in modified versions of Telegram X distributed through malicious advertising campaigns and third-party app stores. The infected apps function normally, giving users no indication they've installed a weaponized version of the messenger.
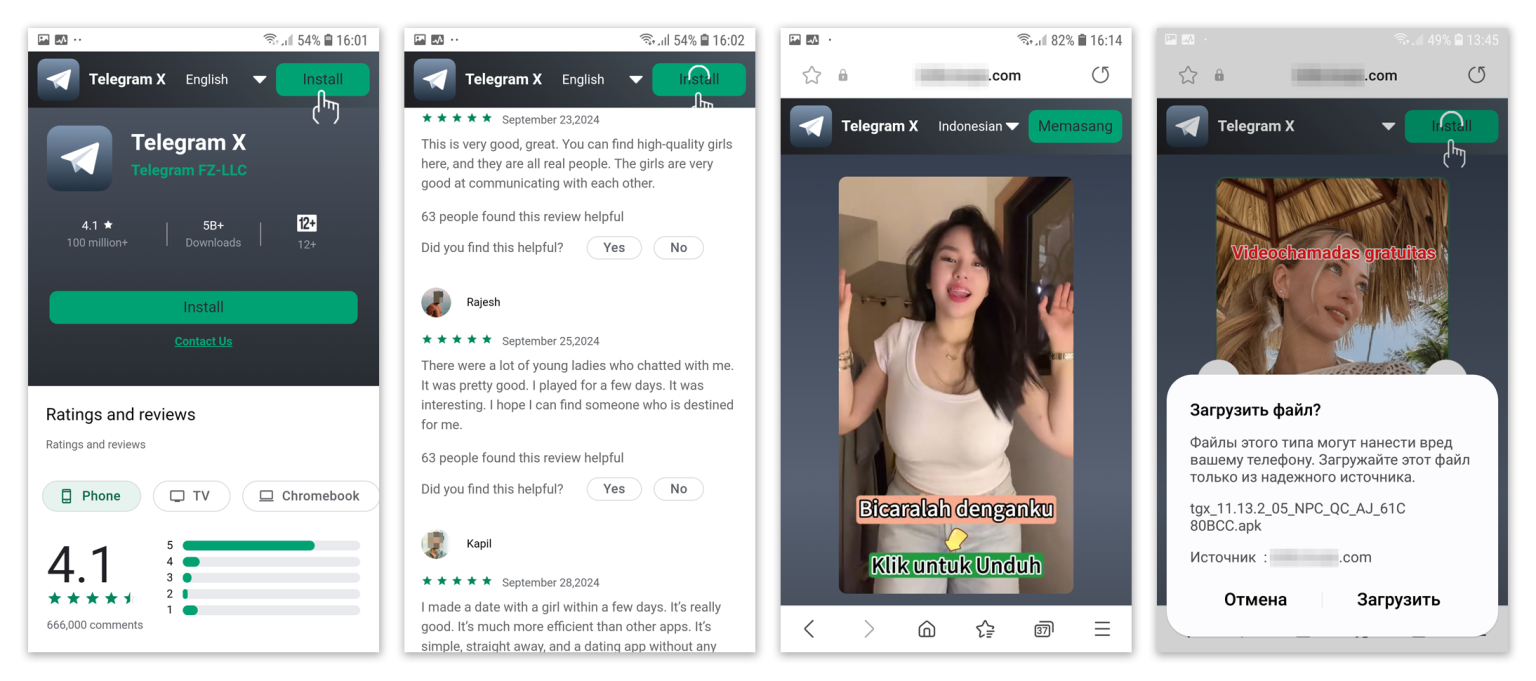
"The primary delivery method is advertising within mobile applications," the researchers noted. Victims see ads promoting Telegram X as a dating and communication platform, which redirect to fake app stores designed to look legitimate.
The malware has spread to approximately 3,000 different device types, including smartphones, tablets, Android TV boxes, and even vehicles with Android-based onboard computers.
Complete Account Takeover
Once installed, Baohuo grants attackers comprehensive control over victims' Telegram accounts. The backdoor can:
- Steal credentials and chat history while exfiltrating all message data and confidential information
- Manipulate channel subscriptions by joining or leaving channels without the user's knowledge
- Hide its tracks by concealing unauthorized devices from the victim's active sessions list
- Intercept clipboard data including passwords, cryptocurrency seed phrases, and sensitive documents
- Display convincing phishing windows that are visually indistinguishable from legitimate Telegram interfaces
- Harvest contacts and SMS messages from the infected device
The malware operators use these capabilities primarily for artificially inflating Telegram channel subscriber counts—a form of social media manipulation that can be monetized.
Unprecedented Control Infrastructure
What sets Baohuo apart from typical Android malware is its innovative dual command-and-control architecture. According to Doctor Web researchers, this represents the first documented use of Redis databases to manage Android threats.
The backdoor connects to traditional C2 servers for initial configuration but also maintains a Redis database connection for receiving real-time commands. This redundancy ensures attackers retain control even if one channel becomes unavailable.
"Communication with the attackers and receiving tasks from them were implemented in the traditional way via a command-and-control server," researchers explained. "But over time, the malware authors added the ability to send additional commands via a Redis database, providing themselves with two independent control channels."
The system also incorporates NPS servers that convert infected devices into proxies, potentially using victims' devices to route malicious traffic and mask attacker locations.
Technical Sophistication
Doctor Web identified three distinct variants of Baohuo, each using different injection methods:
- Direct embedding into Telegram X's main executable DEX file
- Dynamic injection using the LSPatch utility as a patch
- Separate module loading from the app's resource directory
Regardless of variant, the malware initializes alongside the legitimate messenger. For routine operations, Baohuo uses pre-prepared "mirrors" of Telegram's methods. For more complex manipulation, it leverages the Xposed framework to modify messenger functionality in real-time through dynamic method substitution.
This allows Baohuo to hide specific chats, conceal authorized devices, and intercept clipboard contents without disrupting normal app operation.
Constant Surveillance
The backdoor maintains aggressive surveillance schedules:
- Every minute: Requests new commands from C2 servers
- Every three minutes: Transmits device permissions, screen status, app activity, phone number, and account credentials
- Every 30 minutes: Collects data on installed apps, message history, contacts, and logged-in devices
Critical operations include intercepting clipboard data whenever users minimize and restore the messenger—a strategic timing that catches sensitive information like passwords or crypto wallet seed phrases that users copy between apps.
Distribution Networks
While malicious advertising remains the primary infection vector, researchers also found Baohuo in established third-party Android app stores including APKPure, ApkSum, and AndroidP.
Alarmingly, on APKPure, the malware appeared under the official Telegram developer's name despite having different digital signatures—a failure of platform verification that allowed the threat to masquerade as legitimate software.
Doctor Web has notified all platforms hosting the malicious apps, but the incident highlights ongoing security gaps in alternative app marketplaces.
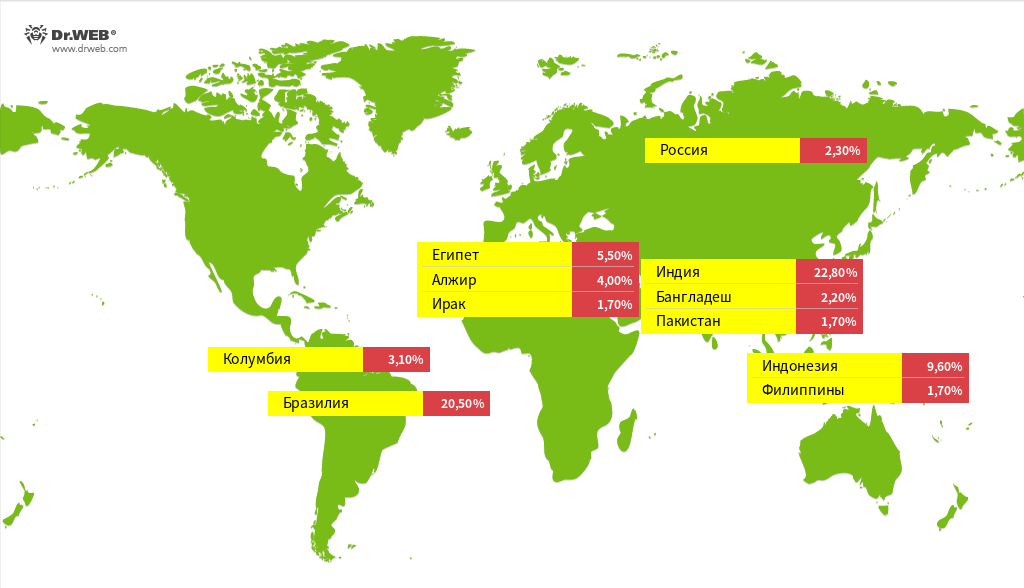
Geographic Focus—For Now
Current campaigns target Portuguese and Indonesian speakers, with malicious ads and fake store pages appearing only in those languages. However, researchers caution that the operation's sophistication and success suggest expansion to other markets is likely.
With approximately 20,000 active connections observed during analysis, the campaign represents a significant threat to Telegram's user base in affected regions.
Protection Recommendations
Security experts recommend:
- Download only from official sources: Install Telegram or Telegram X exclusively from Google Play Store or official websites
- Verify digital signatures: Check app signatures before installation when using third-party stores
- Monitor active sessions: Regularly review logged-in devices in Telegram's settings
- Be wary of ads: Avoid installing apps promoted through in-app advertisements
- Watch for anomalies: Unexplained channel subscriptions or missing devices in session lists may indicate compromise
The Bigger Picture
Baohuo represents an evolution in mobile malware sophistication. The Redis-based control mechanism, comprehensive account takeover capabilities, and advanced evasion techniques signal that Android threats are becoming increasingly complex.
"This is the first known case of using Redis to manage Android malware," researchers emphasized—a technique that may inspire copycat operations.
As alternative app stores proliferate and users seek unofficial versions of popular apps, the attack surface for such campaigns continues to expand. The Baohuo operation demonstrates how easily legitimate-looking apps can harbor sophisticated surveillance tools, particularly when distributed outside official channels with robust verification processes.
For Telegram users, the incident serves as a stark reminder: convenience features in modified apps come with significant security risks, and the cost of using unofficial versions may be complete loss of privacy and account control.


