SonicWall Confirms Breach Exposed Firewall Configurations from All Cloud Backup Users

SonicWall has confirmed that the data breach reported last month compromised firewall configuration backups for all customers who used its cloud backup service, overturning earlier statements that suggested only a limited subset of users were affected.
The exposed data comes from MySonicWall, the company’s customer portal used for product registration, licensing, firmware updates, support requests, and storage of firewall configuration files (.EXP).
Initial Breach and Early Warnings
In mid-September 2025, SonicWall urged customers to reset their credentials immediately after detecting unauthorized access to MySonicWall accounts.
At the time, the company did not disclose technical details but stated that it had blocked attacker access and was working with cybersecurity agencies and law enforcement to investigate.
Administrators were advised to reset all potentially compromised secrets and passwords and to monitor for suspicious activity in their environments. SonicWall initially estimated that only about 5% of customers used cloud backups, and claimed that only “some accounts” had been affected.
New Findings: Scope Expanded to All Cloud Backup Users
In an update released this week, SonicWall clarified that the incident’s scope was far broader than first believed.
“SonicWall has completed an investigation into the scope of the recent cloud backup security incident, conducted jointly with leading IR firm Mandiant,” the company said. “The investigation confirmed that an unauthorized party gained access to the firewall configuration backup files of all customers who used the SonicWall cloud backup service.”
The company emphasized that the compromised files contain credentials and configuration data encrypted with AES-256, though it has not confirmed whether encryption keys could also have been exposed.
Checking Exposure and Mitigation Steps
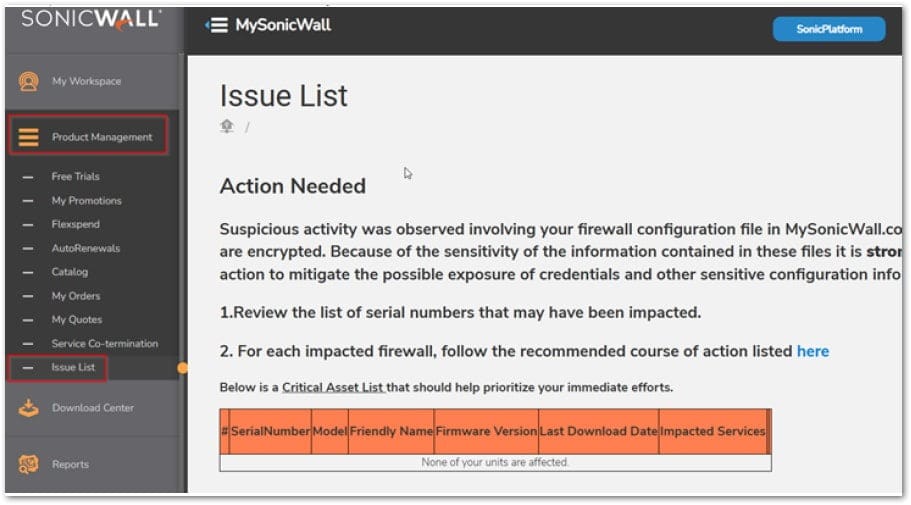
SonicWall has published updated guidance to help users verify whether their devices were affected.
Administrators should:
- Log into MySonicWall.
- Navigate to Product Management → Issue List.
- Review any items flagged for action and follow the Essential Credential Reset Guide, prioritizing active, internet-connected firewalls.
The company continues to advise users to reconfigure all passwords and shared secrets on affected devices and apply network monitoring for abnormal activity.
Why It Matters
The SonicWall incident underscores the risks of centralized cloud backups for critical infrastructure, where configuration data—though encrypted—can reveal sensitive network topology, VPN credentials, and administrative access details.
Security researchers note that even encrypted configurations may assist threat actors in targeted follow-up attacks, depending on how secrets were stored within the exported files.


