Sneaky2FA Phishing Kit Adopts Browser-in-the-Browser Attacks

Security researchers from Push Security report that the Sneaky2FA phishing platform has added browser-in-the-browser attack capabilities. This technique creates fake login windows that steal both credentials and active sessions from victims.
Sneaky2FA ranks among the most widely used PhaaS (phishing-as-a-service) platforms in cybercriminal circles. Along with Tycoon2FA and Mamba2FA, this kit focuses specifically on compromising Microsoft 365 accounts.
How Sneaky2FA Works
The phishing kit gained notoriety for attacks using SVG files and an attacker-in-the-middle approach. The kit proxies the authentication process through its phishing page to the legitimate service, which lets attackers intercept session tokens during login. This means that even accounts protected by two-factor authentication (2FA) can be compromised once victims enter their credentials.
The Browser-in-the-Browser Technique
The browser-in-the-browser (BitB) attack method was first documented in 2022 by security researcher mr.d0x. He showed how BitB creates convincing phishing login forms by simulating browser-in-browser windows.
The attack exploits a common authentication pattern: many websites offer the option to log in using existing accounts from Google, Microsoft, Apple, Twitter, Facebook, Steam, and other providers. When users click these buttons (such as "Login with Google"), a single-sign-on (SSO) window appears in the browser showing only the login form and an address bar with the URL.
These simplified windows display just the essential elements—the login form and a URL in the address bar. Users typically check this URL to confirm they're logging into a legitimate domain (like google.com), which reinforces their trust in the process.
Attackers create fake browser windows that appear inside real browser windows, then display login pages or other forms designed to capture credentials or one-time passcodes (OTP).
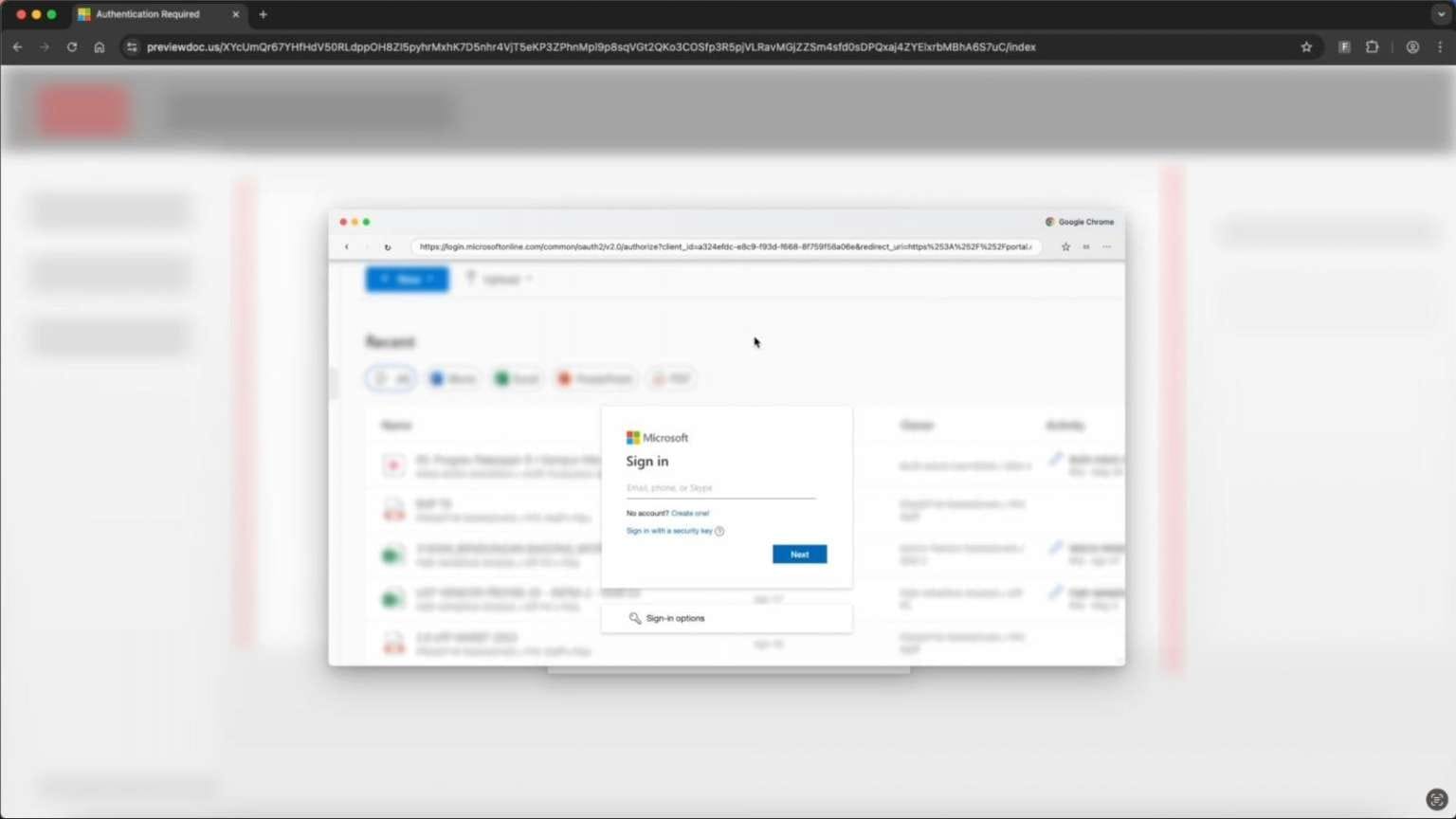
Sneaky2FA's Implementation
Sneaky2FA now actively deploys BitB techniques. The fake pages automatically adjust to match the victim's operating system and browser—for example, mimicking Edge on Windows or Safari on macOS. Here's how the attack unfolds:
- The victim clicks a phishing link to previewdoc[.]com
- The victim completes a Cloudflare Turnstile verification
- A prompt appears requesting login via a Microsoft account to view the document
- After clicking, a fake BitB window renders with a spoofed Microsoft address bar
- A reverse-proxy phishing page loads inside the window, using the legitimate login process to steal both credentials and the session token
The BitB technique adds another layer of deception to Sneaky2FA's existing functionality.
Advanced Evasion Tactics
Researchers note that the phishing kit employs sophisticated obfuscation of HTML and JavaScript to evade static detection methods. Text is hidden using invisible tags, and interface elements are rendered as encoded images. To victims, everything appears legitimate, but this obfuscation complicates the work of security tools. Sneaky2FA also redirects bots and security researchers to a separate, benign page to avoid detection.


