Shai-Hulud Worm Infiltrates Maven
The Shai-Hulud worm has expanded beyond the npm ecosystem and has been detected in Maven. Specialists at Socket discovered an infected package in Maven Central that contains the same malicious components used in the second wave of Shai-Hulud attacks.
Maven Infection Details
Experts identified the package org.mvnpm:posthog-node:4.18.1 in Maven Central, which contains two components characteristic of Shai-Hulud: the setup_bun.js loader and the main payload bun_environment.js. Currently, this is the only detected Java package with this malware.
"The PostHog project has been compromised in both the JavaScript/npm and Java/Maven ecosystems—in all cases, the same payload, Shai-Hulud v2, was used," the researchers stated.
The package in Maven Central is not published by the PostHog team itself. The org.mvnpm coordinates are generated automatically through the mvnpm process, which repackages npm components into Maven artifacts.
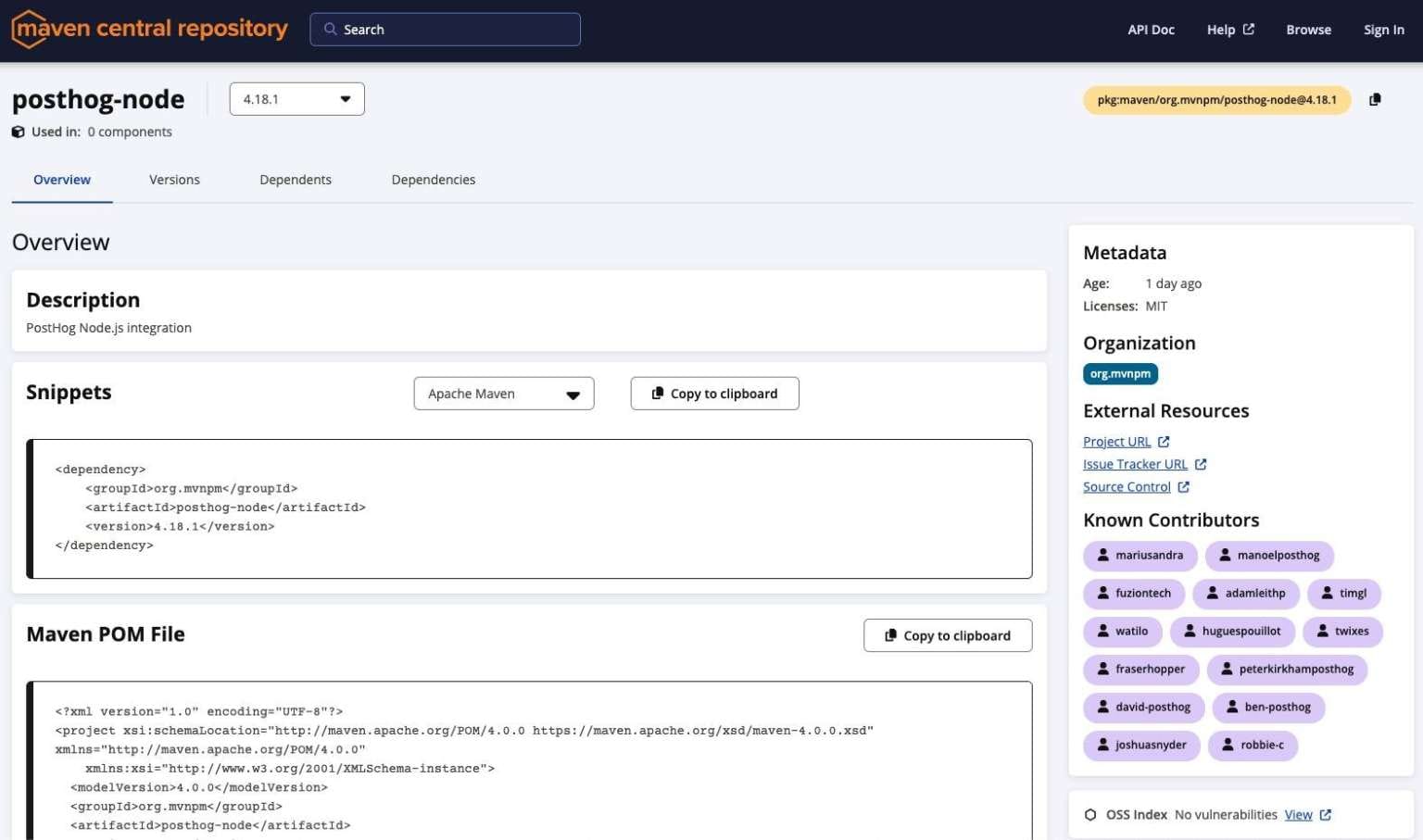
Maven Central representatives stated they are working on additional protective measures to prevent the repackaging of already known compromised npm components.
Second Wave Attack Campaign
The second wave of Shai-Hulud attacks, which began last week, targets developers worldwide with the goal of data theft. The new version of the worm has become more stealthy, and the malware allows attackers to gain unauthorized access to npm maintainer accounts and publish infected versions of packages on their behalf.
Per analysts from Wiz, as of November 24, 2025, over 25,000 repositories on GitHub had published secrets stolen from victims, with approximately 1,000 new repositories appearing every 30 minutes.
Technical Analysis
Per Step Security specialists, the malware consists of two files: setup_bun.js (a dropper disguised as a Bun installer) and bun_environment.js (10 MB), which uses complex obfuscation techniques including a hex-encoded string with thousands of entries, a separate loop for anti-analysis, and an obfuscated function for extracting each string in the code.
After infection, the malware executes five attack stages, including stealing secrets (GitHub and npm tokens, AWS, GCP, Azure credentials) and destructively overwriting the victim's entire home directory if four required conditions are not met: if the malware cannot authenticate on GitHub, create a repository, or find GitHub and npm tokens.
The stolen secrets are published to automatically generated GitHub repositories with the description "Sha1-Hulud: The Second Coming."
Attack Vector and Scope
Per analysts from Aikido Security, the attackers exploited incorrect CI configurations in GitHub Actions workflows. The attackers used vulnerabilities in the pull_request_target and workflow_run triggers, which allowed them to compromise projects like AsyncAPI, Postman, and PostHog.
Per specialists at GitGuardian, OX Security, and Wiz, this malicious campaign led to the leak of hundreds of GitHub access tokens and credentials for AWS, Google Cloud, and Azure (over 5,000 files with stolen secrets were uploaded to GitHub). An analysis of 4,645 repositories revealed 11,858 unique secrets, of which 2,298 remained valid and publicly accessible as of November 24, 2025.