ShadowV2 Botnet Leveraged AWS Issues to Test Attacks
FortiGuard Labs researchers discovered a new Mirai-based botnet named ShadowV2 that exploits at least eight vulnerabilities in IoT devices from D-Link, TP-Link, and other manufacturers. The malware first appeared during a major AWS outage in October 2024 and operated only for the duration of that incident, suggesting the attackers were conducting a test run.
Attack Vector and Targets
ShadowV2 spreads by attacking known vulnerabilities across various IoT products. Target devices include outdated DD-WRT systems (CVE-2009-2765), D-Link routers and cameras (CVE-2020-25506, CVE-2022-37055, CVE-2024-10914, CVE-2024-10915), DigiEver DVRs (CVE-2023-52163), TBK devices (CVE-2024-3721), and TP-Link routers (CVE-2024-53375).
The most serious vulnerability in this list is CVE-2024-10914, which allows arbitrary command execution on older D-Link routers. Last year, the manufacturer officially stated it would not release patches for the affected models.
D-Link took a similar stance on CVE-2024-10915. The company updated an old security bulletin to add the CVE identifier and published a new warning about ShadowV2 activity, reminding users that end-of-life devices no longer receive firmware updates.
For the CVE-2024-53375 bug in TP-Link routers, researchers report that a beta patch has already been developed.
Attack Infrastructure and Scope
Per FortiGuard Labs, ShadowV2 attacks originated from IP address 198[.]199[.]72[.]27 and targeted routers, NAS storage devices, and DVRs across seven economic sectors: government, technology, manufacturing, MSSPs, telecommunications, and education.
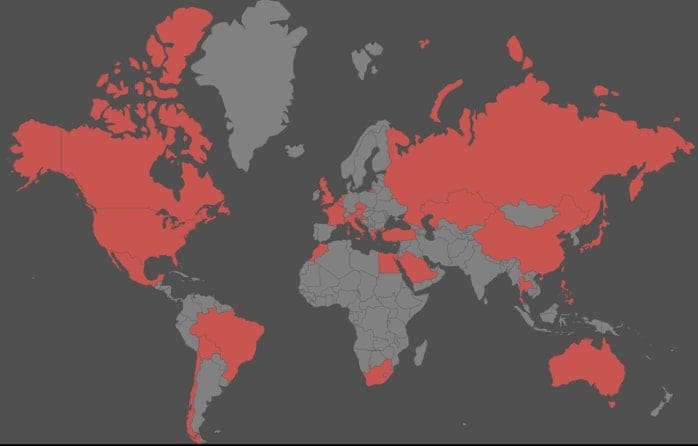
The attacks spanned 28 countries across six continents: Canada, the USA, Mexico, Brazil, Bolivia, Chile, the United Kingdom, the Netherlands, Belgium, France, the Czech Republic, Austria, Italy, Croatia, Greece, Morocco, Egypt, South Africa, Turkey, Saudi Arabia, Russia, Kazakhstan, China, Thailand, Japan, Taiwan, the Philippines, and Australia.
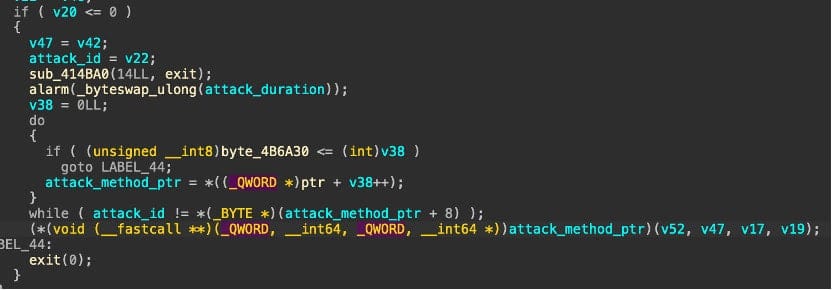
Technical Analysis
The malware's structure resembles the Mirai LZRD variant. The malicious payload is delivered to vulnerable devices via the binary.sh loader script, which fetches the main payload from server 81[.]88[.]18[.]108.
Using infected devices, ShadowV2 can launch DDoS attacks via UDP, TCP, and HTTP protocols, with various flood types for each protocol. The malware's command-and-control infrastructure directs attacks by sending commands to compromised devices.
Threat Actor Motives
DDoS botnet operators typically monetize their infrastructure by renting it to other criminals or engaging in direct extortion—demanding ransom from victims to stop attacks. However, the actors behind ShadowV2 and their monetization strategy remain unclear.
FortiGuard Labs included indicators of compromise in their report and emphasized the importance of timely firmware updates for IoT devices.