SantaStealer Steals Data from Browsers and Cryptocurrency Wallets

Rapid7 discovered SantaStealer, malware advertised on Telegram channels and hacker forums as operating exclusively in RAM to evade traditional security solutions. Analysis revealed the stealer is poorly secured and contains fundamental operational security flaws.
SantaStealer is a rebranded version of BluelineStealer. The presumed Russian-speaking developer plans an official launch by year-end. Two subscription tiers are currently available: basic for $175 monthly and premium for $300 monthly.
Rapid7 gained access to the service's administrative panel and analyzed several malware samples. Despite creators' claims about detection complexity, the samples are far from perfect. The malware contains unencrypted strings, lacks obfuscation, and retains original function and global variable names—all simplifying analysis.
"The leak of samples at such an early stage of development, when unencrypted data still remains in the code, is a serious operational error that can negate a significant portion of the developers' efforts and indicates a low level of their operational security," Rapid7 stated.
Technical Capabilities
SantaStealer deploys 14 specialized data collection modules, each operating in a separate thread. The malware steals:
- Browser passwords, cookies, history, and saved payment card data
- Telegram and Discord account credentials
- Steam platform login information
- Cryptocurrency wallet data and browser extension credentials
- Desktop screenshots
- User documents
Stolen data is written to memory, packaged into ZIP archives, and sent in 10 MB portions to command and control servers via port 6767.
SantaStealer bypasses App-Bound Encryption, a Chrome browser protection system introduced in summer 2024 that prevents malware from accessing saved credentials.
Customization Options
The control panel offers flexible build configurations—from aggressive versions that steal everything indiscriminately to specialized versions targeting specific data types. Options include excluding computers in CIS countries and delayed launch functions to complicate analysis.
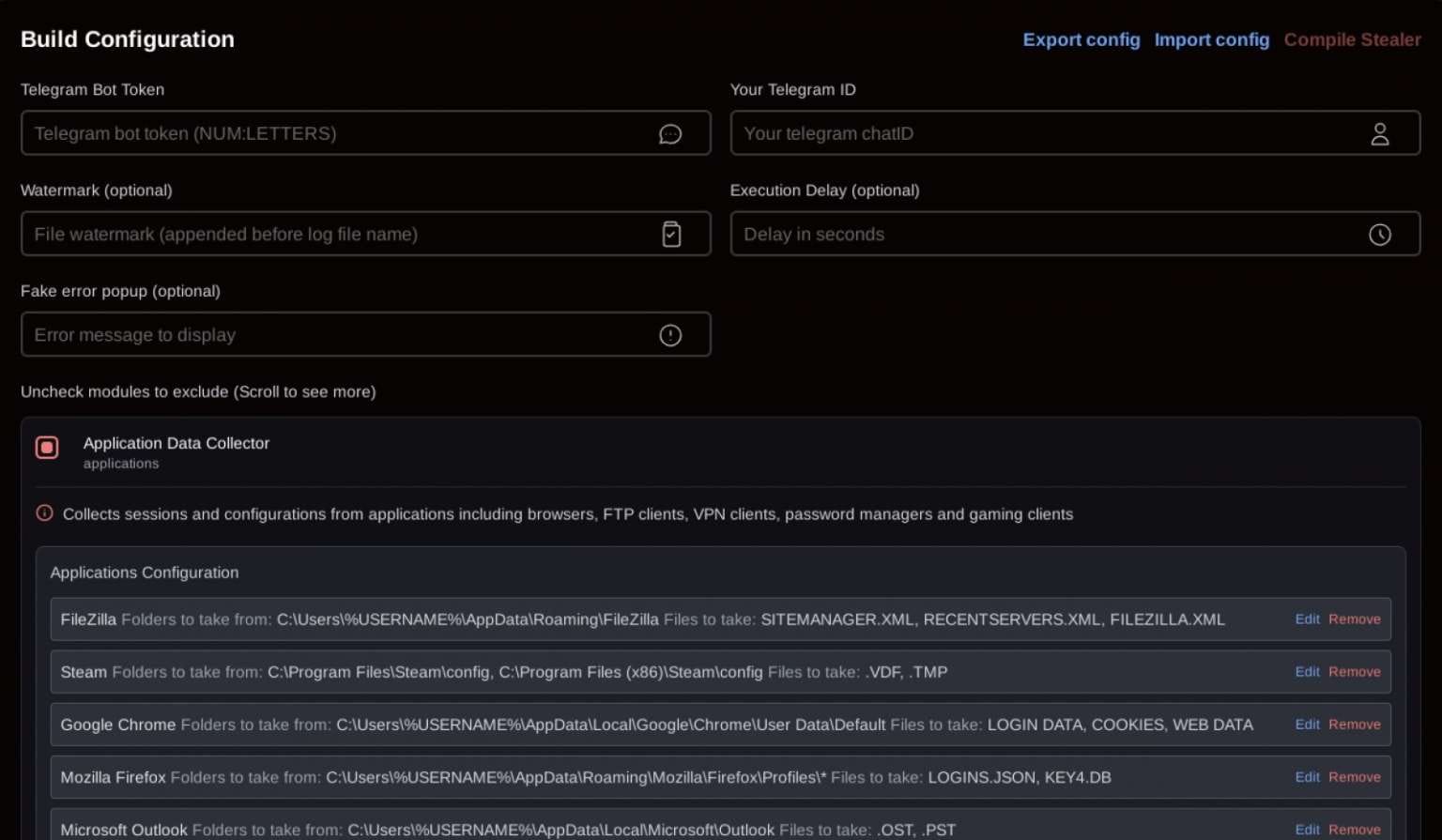
While SantaStealer remains unfinished and not widely distributed, Rapid7 suggests attackers may use ClickFix techniques for distribution, where victims are tricked into copying and executing malicious commands in Windows command line themselves. Traditional delivery methods remain relevant: phishing emails, pirated software, torrent trackers, malvertising, and YouTube comments.


