RondoDox Botnet Exploits XWiki Vulnerability to Compromise Servers

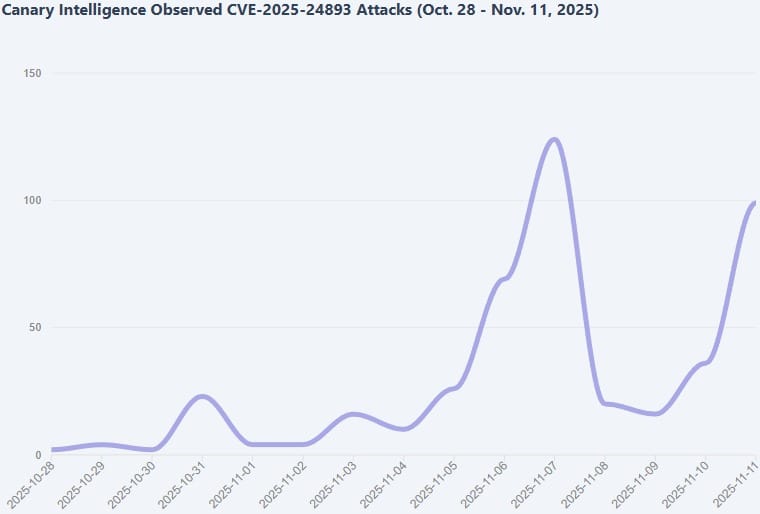
Security researchers are warning about a new attack wave from the RondoDox botnet exploiting a critical remote code execution vulnerability in XWiki Platform (CVE-2025-24893). CISA has already added the flaw to its catalog of actively exploited vulnerabilities, with exploitation attempts increasing since early November.
RondoDox first appeared on researchers' radar in summer 2025. Fortinet analysts identified it as the work of a new threat actor group.
Within months, the botnet has expanded significantly. According to Trend Micro researchers, recent malware versions target multiple device types—digital video recorders, network video recorders, video surveillance systems, and web servers—while exploiting dozens of vulnerabilities, including flaws first demonstrated at the Pwn2Own hacking competition.
RondoDox operators are now actively exploiting a new vulnerability in XWiki, a popular open-source wiki platform companies frequently deploy for internal knowledge management systems. CVE-2025-24893 affects all XWiki versions prior to 15.10.11 and 16.4.1.
VulnCheck researchers report that since November 3, 2025, RondoDox has used specially crafted HTTP GET requests to inject base64-encoded Groovy code through the XWiki SolrSearch endpoint. This technique triggers the download and execution of a remote shell script that deploys the main RondoDex payload.
Beyond initial compromise, threat actors have begun deploying cryptocurrency miners on infected devices. In some cases, attackers have established reverse shells for persistent access.
The XWiki vulnerability has attracted attention beyond RondoDox operators. VulnCheck observes widespread network scanning using Nuclei, with attackers deploying payloads to execute commands like cat /etc/passwd via Groovy injections. Researchers also detect OAST (Out-of-band Application Security Testing) scanning, indicating a broad search for vulnerable XWiki installations.
XWiki administrators should apply patches immediately. Multiple threat actor groups are actively exploiting the vulnerability, and exploitation activity is expected to intensify.