Rhadamanthys Stealer Disrupted: Evidence Points to Law Enforcement Operation

Cybersecurity specialists report that dozens of customers using the Rhadamanthys info-stealer are complaining about sudden loss of access to their malware servers. The disruption appears consistent with a law enforcement takedown operation.
What is Rhadamanthys?
Rhadamanthys is a popular info-stealer among criminals, operating on a Malware-as-a-Service (MaaS) business model. The malware can extract credentials, cookies, and other sensitive information from browsers, email clients, and various applications. Attackers typically distribute it through fake software cracks, YouTube video descriptions, and malicious search engine advertisements.
The service operates on a subscription basis. Hackers pay the developers for access to the malware itself, a web panel for collecting stolen data, and technical support.
Signs of Law Enforcement Involvement
Cybersecurity researchers g0njxa and Gi7w0rm told Bleeping Computer that many of the stealer's customers have grown alarmed in recent days, suspecting that information about their operations may have fallen into the hands of law enforcement.
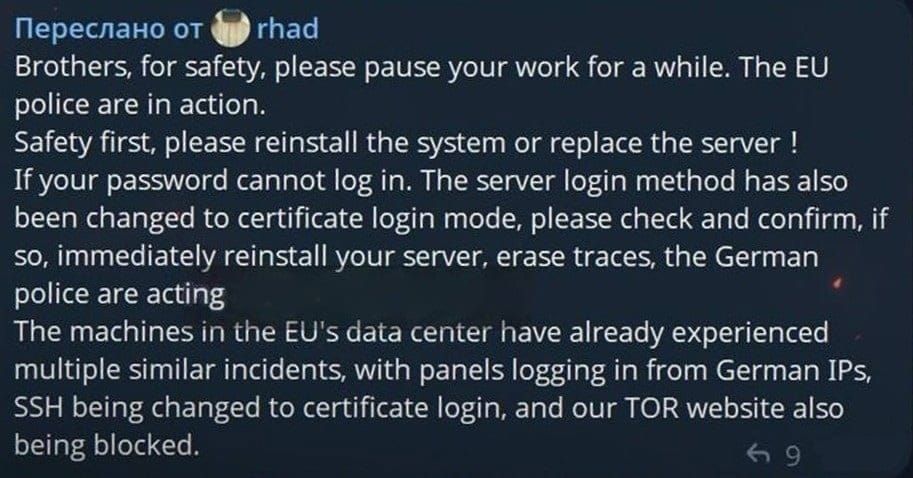
On hacking forums, Rhadamanthys operators report that SSH access to the stealer's panels has changed. The system now requires certificate-based authentication instead of the standard root password method.
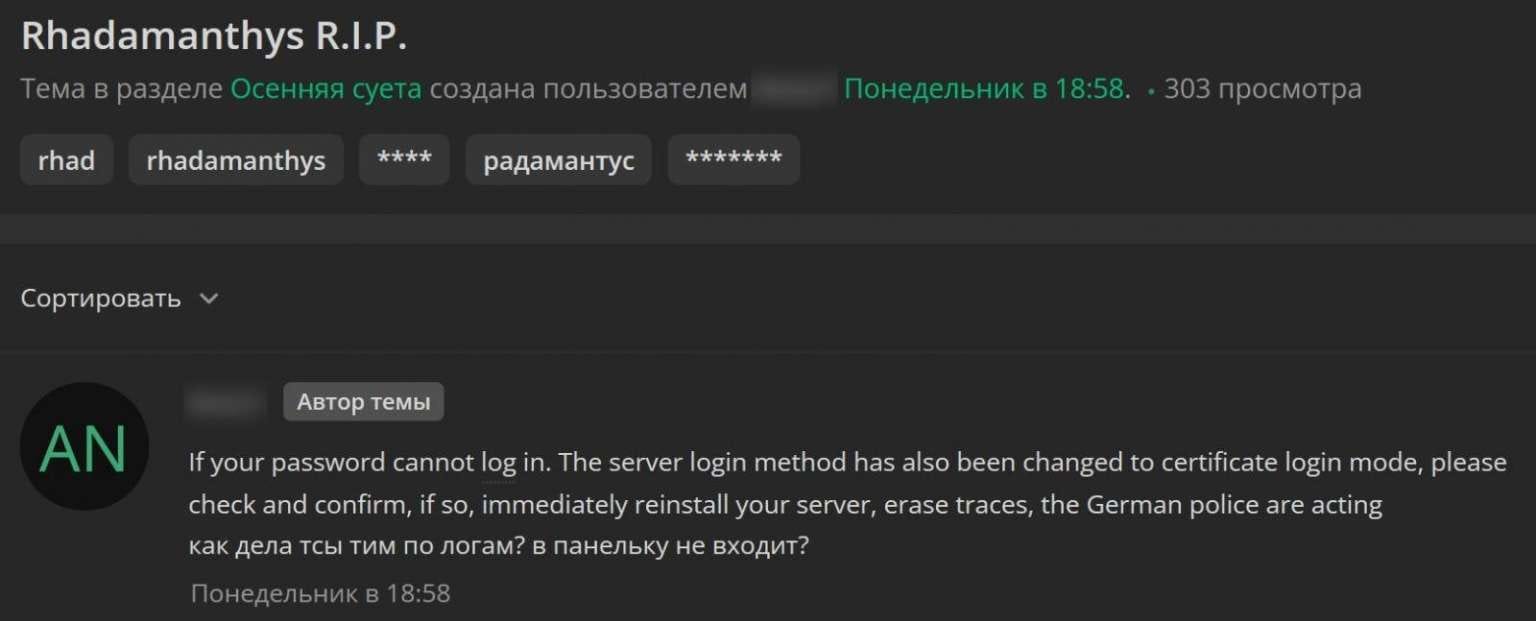
"If the password isn't working and the login method has been changed to certificate mode, check and immediately reinstall the server, wipe the traces—the German police are at work," one user warned on the forum.
Another customer confirmed the security changes:
"I can confirm, guests visited my server. The password was removed, login is only by certificate. I had to wipe everything and shut down the server. Those who set everything up manually probably weren't affected, but those who used the 'smart panel' were hit hard."
German Law Enforcement Connection
The Rhadamanthys developers themselves suggest the situation might involve German law enforcement. Before customers lost access to stealer panels hosted in European data centers, the systems recorded logins from German IP addresses.
Additionally, g0njxa reported that Rhadamanthys Tor sites are now offline. However, the typical law enforcement seizure banner that usually appears during such operations has not yet been posted.
Possible Link to Operation Endgame
Researchers believe these events could be part of Operation Endgame a large-scale international law enforcement campaign targeting MaaS services.
Operation Endgame has already achieved significant results. Previous actions dismantled the AVCheck service and took down infrastructure for multiple malware families, including SmokeLoader, DanaBot, IcedID, Pikabot, Trickbot, Bumblebee, and SystemBC.
Currently, a countdown timer is active on the official Operation Endgame website, suggesting a new announcement will be made later today. This timing coincides with the Rhadamanthys disruption, strengthening speculation about a coordinated law enforcement action.
What This Means
The apparent takedown of Rhadamanthys represents another blow to the cybercriminal ecosystem. MaaS platforms like Rhadamanthys lower the barrier to entry for cybercrime by providing turnkey malware solutions. Disrupting these services forces criminals to rebuild infrastructure, reestablish trust networks, and risk exposure during migration to alternative platforms.
If confirmed as a law enforcement operation, the Rhadamanthys takedown would mark another success in the ongoing campaign against commercial malware services that fuel credential theft and data breaches worldwide.


