Researchers Spied on Satellite Traffic with an $800 Device

Scientists from the University of California San Diego and the University of Maryland have uncovered a major privacy and security flaw affecting satellite communications worldwide.
Their three-year study revealed that roughly half of all geostationary satellite transmissions are sent without encryption, exposing sensitive data from corporations, governments, and everyday users—all intercepted using equipment that cost less than $800.

A Research Project Called “Don’t Look Up”
The researchers titled their study “Don’t Look Up”—a nod to the misplaced confidence of satellite operators who assumed that, because few people had the tools to listen, their transmissions were safe.
Instead, the team demonstrated that “security through obscurity” is no defense at all.
Using readily available components—a $185 satellite dish, a $335 motorized roof mount, and a $230 tuner card—they assembled a signal interception system on the roof of a university building in San Diego. From there, they could capture data from geosynchronous satellites covering the western United States and Mexico—about 15% of global satellite traffic.
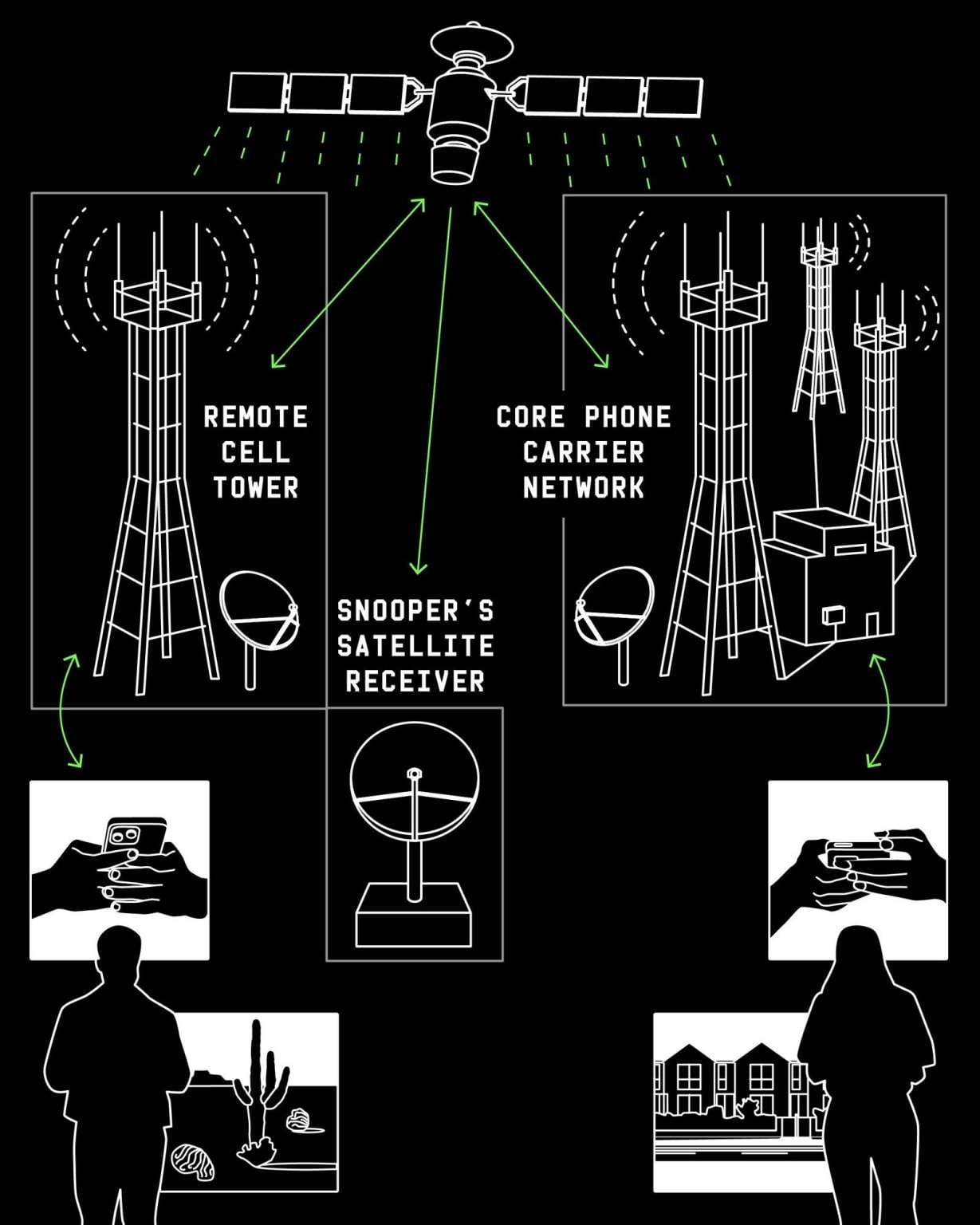
The Unprotected Backbone: Backhaul Traffic
One of the main focuses of the research was cellular backhaul traffic—the data that flows between remote cell towers and an operator’s core network via satellite links.
In regions where running fiber is too expensive, operators rely on this setup to stay connected. The problem? Anyone within the satellite’s coverage area—spanning thousands of kilometers—can intercept the same signals using similar equipment.
If those signals are unencrypted, everything is visible.
In just nine hours, the researchers captured the phone numbers, SMS messages, and call data of over 2,700 T-Mobile subscribers, all transmitted in plain text.
“When we saw all this, my first question was: did we just commit a felony? Are we wiretapping people’s phones?” said Dave Levin, a computer science professor at the University of Maryland.
He clarified that the team did not target any specific users—they simply recorded what was openly broadcast. “These signals are sent over more than 40% of the Earth’s surface at any given time,” Levin added.
Airlines, Banks, and Corporations in the Clear
The team didn’t just intercept phone data. They also accessed in-flight Wi-Fi traffic from ten airlines, including passengers’ web histories and audio from streaming services.
In Mexico, they picked up corporate communications from Walmart, ATM data from Santander, and other financial transactions, all unencrypted.
Military and Infrastructure Exposure
The findings turned even more serious when the researchers detected military and government traffic.
They intercepted US naval vessel identifiers and unprotected communications from the Mexican military, including real-time helicopter tracking (Mi-17 and UH-60 Black Hawk) and mission data related to counter-narcotics operations.
The vulnerabilities extended to critical infrastructure as well.
The Comisión Federal de Electricidad (CFE)—Mexico’s state-owned power company serving 50 million customers—transmitted work orders, customer data, and failure reports in plain text. Similar weaknesses were found in offshore oil and gas platforms.
“This just shocked us,” said Aaron Schulman, the project’s lead researcher. “Critical elements of our infrastructure rely on satellite communication, and we were sure everything was encrypted. But time and again, everything was in the open.”
Slow Fixes, Fast Risks
Starting in December 2024, the team began alerting affected organizations. T-Mobile moved quickly, encrypting its satellite links within weeks. But others—particularly infrastructure operators—have yet to act.
Given the low cost of interception, experts warn that nation-state intelligence agencies could exploit these gaps using far more advanced equipment. In fact, the NSA had already cautioned about unencrypted satellite transmissions back in 2022.
The Bigger Picture
Alongside their paper, the researchers published an open-source toolkit on GitHub to analyze intercepted satellite data, hoping transparency would pressure operators to secure their systems.
But the most sobering part?
Their equipment could monitor only about 15% of all satellite communications—meaning the real scope of exposure is likely far greater.
“If half of what we can see is unencrypted,” Schulman said, “imagine what’s happening across the rest of the sky.”


