Remote Code Execution Flaw in ImunifyAV Puts Millions of Websites at Risk

A remote code execution (RCE) vulnerability in ImunifyAV, a malware scanner deployed across Linux hosting environments, creates significant exposure for tens of millions of websites. The flaw enables attackers to compromise the underlying host system through malicious file uploads.
What ImunifyAV Is and Why This Matters
ImunifyAV functions as a core component of Imunify360, a security platform used by hosting providers and shared hosting services running on Linux. Here's what you need to know about the deployment model:
Installation Context: Hosting providers install ImunifyAV at the platform level, not individual website owners. This means the average site owner has no direct interaction with the scanner, yet relies entirely on their hosting provider to maintain and patch it.
Deployment Scale: According to CloudLinux's October 2024 statistics, ImunifyAV protects over 56 million websites. The broader Imunify360 platform has more than 645,000 active installations across hosting environments.
Business Impact: When a vulnerability exists in software deployed at the hosting platform level, the risk multiplies exponentially. A single compromised hosting server can expose hundreds or thousands of customer websites simultaneously.
Technical Details of the Vulnerability
The vulnerability, which currently lacks a CVE identifier, affects the AI-bolit malware detection component in versions prior to 32.7.4.0. AI-bolit is present across three product variations: Imunify360 (full security suite), ImunifyAV+ (paid malware scanner), and the free ImunifyAV version.
Timeline of Discovery and Remediation:
Patchstack researchers identified the flaw in late October 2025, prompting CloudLinux to release initial patches. On November 10, 2025, the vendor backported fixes to older versions of Imunify360 AV. CloudLinux published a security bulletin this week warning customers about the critical nature of this vulnerability and urging immediate deployment of patched version 32.7.4.0.
Root Cause Analysis:
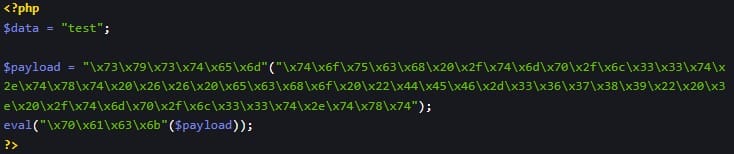
The vulnerability stems from unsafe handling of input data during the deobfuscation process in AI-bolit. The scanner uses PHP's call_user_func_array function without proper validation of the data being processed. Here's how the attack chain works:
- Attacker uploads a specially crafted, obfuscated PHP file to a website hosted on a server running vulnerable ImunifyAV
- Scanner attempts to deobfuscate the file during routine malware inspection
- Malicious function names embedded in the obfuscated file get passed to
call_user_func_array - Scanner executes dangerous PHP functions (
system,exec,shell_exec,passthru, oreval) with attacker-controlled parameters - Attacker achieves remote code execution in the context of the scanner's privileges
Attack Prerequisites:
Patchstack notes that successful exploitation requires Imunify360 AV to actively perform deobfuscation during file analysis. In the standalone AI-Bolit CLI configuration, this deobfuscation option defaults to disabled. However, the integration into Imunify360 changes this behavior significantly.
When AI-bolit runs as part of Imunify360, deobfuscation activates in "always on" mode across multiple scan types:
- Background scans (continuous monitoring)
- On-demand scans (administrator-initiated)
- User-initiated scans (triggered by hosting customers)
- Quick scans (rapid threat assessment)
This "always on" configuration matches the exact conditions needed for exploitation, meaning most production deployments are vulnerable by default.
Proof of Concept and Real-World Impact
Patchstack included a proof of concept (PoC) exploit in their report demonstrating the practical exploitation path. The PoC creates a malicious PHP file in the server's tmp directory. When ImunifyAV scans this file, the embedded payload executes, granting the attacker remote code execution capabilities.
Privilege Escalation Risk:
The severity increases substantially in shared hosting environments where ImunifyAV typically runs with elevated system privileges. If the scanner operates with root or similar high-level permissions (standard practice for security tools that need system-wide visibility), successful exploitation can lead to complete server compromise.
In a shared hosting scenario, this means:
- Attacker gains control of the entire physical or virtual server
- All customer websites hosted on the compromised server become accessible
- Attacker can read databases, configuration files, and sensitive credentials
- Lateral movement to other systems becomes possible if the hosting infrastructure uses shared authentication or management systems
What Hosting Providers and Website Owners Should Do
For Hosting Providers:
The immediate priority is patching. Update Imunify360, ImunifyAV+, and free ImunifyAV installations to version 32.7.4.0 or later. For organizations running older versions of the platform, CloudLinux has backported the fix, making updates available across the product line.
Risk Assessment Actions:
- Inventory all servers running ImunifyAV to identify vulnerable versions
- Review logs for suspicious PHP file uploads or unusual scan activity
- Examine tmp directories for unexpected PHP files created during the vulnerability window
- Verify that automatic updates are enabled for security patches going forward
For Website Owners:
Your direct action options are limited since ImunifyAV operates at the hosting provider level. However, you can take these steps:
- Contact your hosting provider to verify they've applied the security patch
- Ask specifically about Imunify360/ImunifyAV version numbers (confirm version 32.7.4.0 or higher)
- Request confirmation of their patch management timeline and process
- Consider reviewing hosting provider security practices and incident response capabilities
The Broader Context for OSINT Investigations
This vulnerability highlights several patterns I track in my OSINT investigations for clients:
Supply Chain Security: Software deployed at the infrastructure level (hosting platforms, security tools, monitoring systems) represents a high-value target. Attackers who compromise these systems gain access to multiple downstream organizations simultaneously. When evaluating acquisition targets or vendor relationships, I specifically look for:
- How hosting providers manage security patches for platform-level software
- Whether organizations have visibility into their hosting provider's security posture
- The presence of vendor security assessment processes in IT governance
Shared Hosting Risk: This vulnerability exemplifies why shared hosting environments require careful evaluation during due diligence. A single compromised server can expose dozens or hundreds of businesses, yet individual tenants have limited visibility and no control over platform security.
Disclosure Timelines: The gap between vulnerability discovery (late October 2025) and public disclosure (November 2025) is relatively short, but given the deployment scale (56 million websites), even a brief window creates substantial exposure. Organizations should ask vendors about their security patch deployment practices and typical timelines.
Key Takeaways
This ImunifyAV vulnerability demonstrates that security tools themselves can become attack vectors when input validation and secure coding practices are overlooked. The use of call_user_func_array without proper input sanitization is a well-known antipattern in PHP development, yet it persisted in production code protecting tens of millions of websites.
For hosting providers, the lesson is clear: security tools require the same rigorous secure development lifecycle as any other critical infrastructure component. For website owners, this incident underscores the importance of choosing hosting providers with strong security governance and transparent patch management practices.
The patched version (32.7.4.0) is available now. If you're responsible for infrastructure running ImunifyAV, update immediately. If you're a website owner on shared hosting, verify your provider has applied this critical security patch.+
Sources:
- Patchstack vulnerability report on ImunifyAV RCE
- CloudLinux security bulletin (November 2025)
- Imunify360 deployment statistics (October 2024)
Disclosure: All information in this article comes from publicly available security research and vendor disclosures. Red Dog Security conducts OSINT investigations using only publicly accessible information sources in compliance with our documented Research Ethics Policy.


