React2Shell Vulnerability Targets Russian Companies as Ransomware Groups Join Attacks

The critical React2Shell vulnerability continues spreading across the threat landscape. Attackers have hit Russian companies, while Google reports growing exploitation by Chinese and Iranian groups. Ransomware operators now use the flaw, and React developers have patched several additional bugs in React Server Components.
The Vulnerability
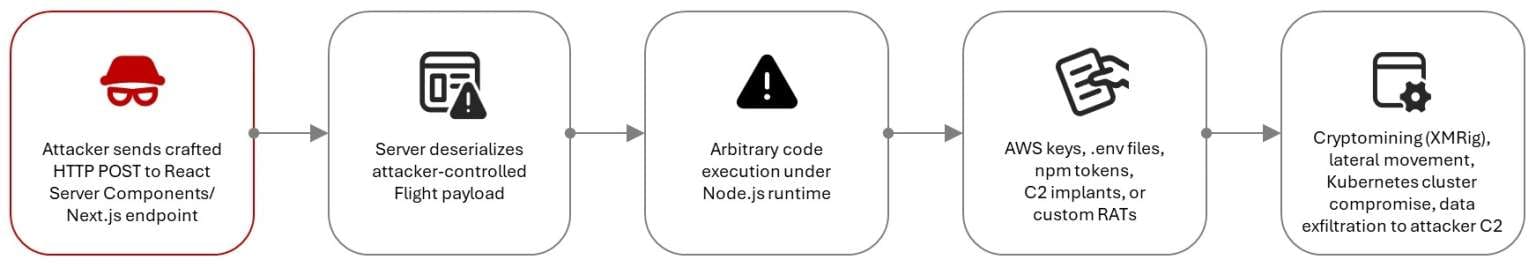
React2Shell (CVE-2025-55182) is a critical flaw discovered in December 2024 in Meta's React JavaScript library. The vulnerability scored 10/10 on the CVSS scale and stems from unsafe data deserialization in React Server Components, allowing remote code execution through a standard HTTP request without authentication or privileges.
The bug affects React versions 19.0, 19.1.0, 19.1.1, and 19.2.0 in default configurations, plus the popular Next.js framework. Patches were released in React versions 19.0.1, 19.1.2, and 19.2.1, along with affected Next.js releases.
Security researchers warn that similar issues may exist in other libraries with React Server implementations, including Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodSDK, and Waku.
Early Exploitation
Chinese hacking groups Earth Lamia and Jackpot Panda, along with North Korea's Lazarus group, exploited the vulnerability almost immediately after disclosure. At least 30 organizations suffered attacks in early December.
Attacks on Russian Companies
BI.ZONE specialists recorded the first three attacks on Russian businesses using React2Shell. An insurance company, an auto parts retailer, and an IT company serving government agencies were targeted. All attacks deployed the XMRig miner to mine Monero cryptocurrency using compromised machine resources.
One attack also attempted to deploy the Kaiji and RustoBot botnets on infected machines for DDoS attacks and traffic proxying.
Mass Exploitation
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) initially gave federal agencies until December 26, 2024, to patch but shortened the deadline to December 12 as the threat escalated.
Per Kaspersky Lab, over 35,000 exploitation attempts of CVE-2025-55182 were recorded by December 10. Attackers deployed miners, Mirai/Gafgyt and RondoDox botnets, Cobalt Strike, Sliver beacons, and Go backdoors with reverse shell and reconnaissance capabilities. Some used TruffleHog and Gitleaks to harvest secrets from repositories.
Huntress analysts identified previously unknown malware samples spread through React2Shell:
- PeerBlight - Linux backdoor with code overlapping RotaJakiro and Pink malware
- CowTunnel - Reverse proxy server
- ZinFoq - Go-written post-exploitation framework
- d5.sh and fn22.sh - Loader scripts deploying Sliver C2
- wocaosinm.sh - Kaiji malware variant for DDoS attacks
State-Sponsored Activity
Google Threat Intelligence Group (GTIG) linked React2Shell exploitation to at least five Chinese APT groups:
- UNC6600 delivered the MINOCAT tunneling tool
- UNC6586 delivered the SNOWLIGHT loader
- UNC6588 delivered the COMPOOD backdoor
- UNC6603 delivered an updated HISONIC backdoor
- UNC6595 delivered the Linux version of ANGRYREBEL trojan
Iranian hackers also exploited React2Shell for cryptomining via XMRig.
Microsoft reported several hundred compromised machines across multiple organizations. Attackers used CVE-2025-55182 with TruffleHog and Gitleaks tools, plus custom scripts to steal AWS credentials, Azure tokens, OpenAI API keys, and Kubernetes credentials.
Ransomware and Linux Backdoors
S-RM researchers recorded a Weaxor ransomware attack on December 5, 2024, exploiting React2Shell. From intrusion to ransomware deployment took less than one minute. Hackers executed an obfuscated PowerShell command, deployed Cobalt Strike, disabled Windows Defender, and launched the malware. The attack remained on a single host without lateral movement.
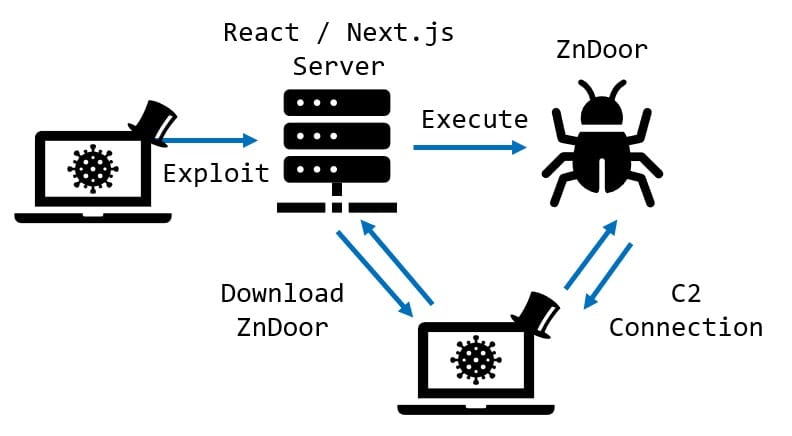
Palo Alto Networks and NTT Security described campaigns spreading the Linux backdoors KSwapDoor and ZnDoor through React2Shell.
KSwapDoor is a professionally developed RAT that creates internal mesh networks between compromised servers, uses military-grade encryption, and features a sleep mode to evade security solutions.
ZnDoor, first seen in attacks on Japanese organizations in December 2023, provides an interactive shell, file operations, SOCKS5 proxy deployment, and timestamp modification.
Additional React Vulnerabilities
While attackers exploited React2Shell, researchers discovered three more vulnerabilities in React Server Components: CVE-2025-55184, CVE-2025-67779, and CVE-2025-55183.
The first two involve unsafe deserialization of HTTP request data, leading to denial of service through infinite loops that crash the server process. The third allows source code leakage of any Server Function via crafted HTTP requests.
React developers explained that discovering new issues after critical vulnerability disclosure is standard industry practice—researchers examine adjacent code for bypass methods. Patches were released in versions 19.0.3, 19.1.4, and 19.2.3.
Current Threat Landscape
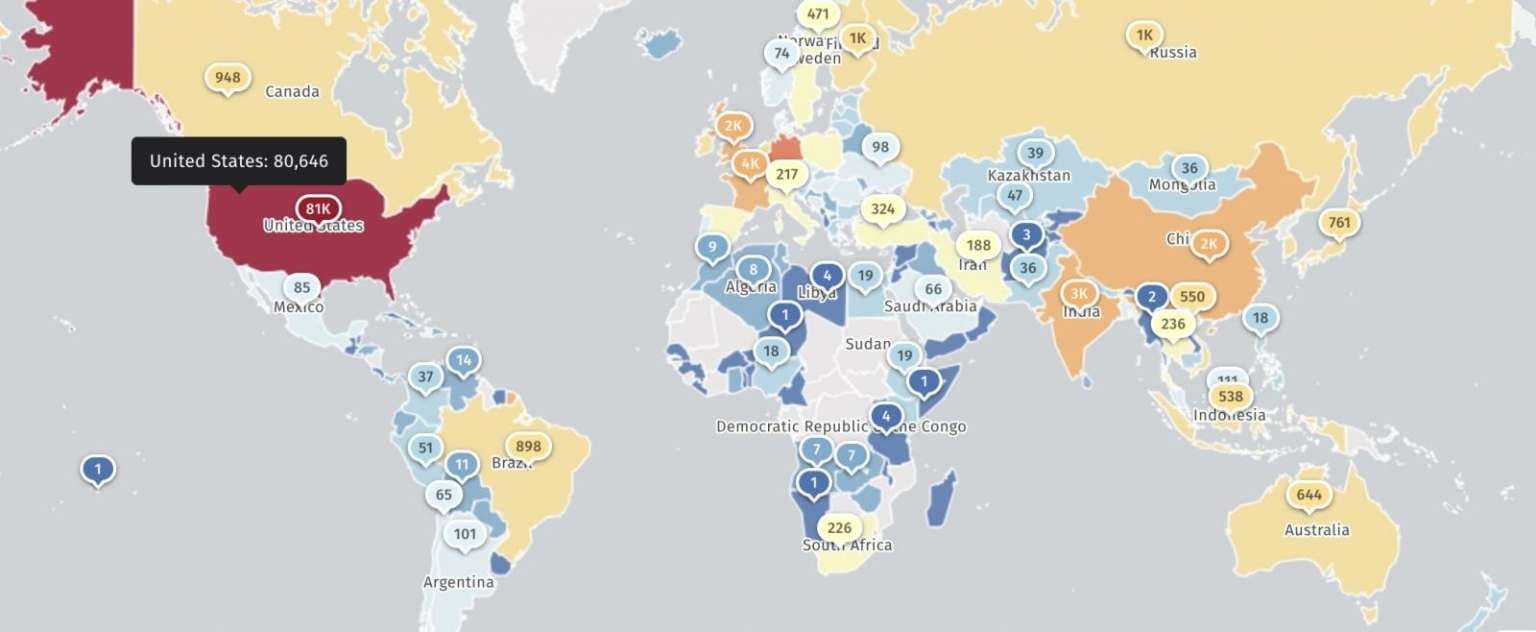
Shadowserver tracks approximately 110,000 IP addresses vulnerable to React2Shell attacks. Over 80,000 are in the USA, with more than 1,000 in Russia.
VulnCheck experts counted over 140 public proof-of-concept exploits for React2Shell by late last week. Roughly half function properly, while the rest are broken or deliberately misleading. Working exploits can load in-memory web shells like Godzilla, scan for vulnerabilities, and deploy lightweight WAFs to block malicious payloads.
Coalition compared React2Shell to the notorious Log4Shell vulnerability from 2021, noting the flaw creates systemic risks across the industry. Rapid7 analysts agree, emphasizing that CVE-2025-55182 exploitation spans the entire threat spectrum—from low-skilled cryptominer and Mirai botnet operators to professional state-sponsored groups.


