Ransomware Groups Extracted $2.1 Billion from Victims Between 2022-2024

Ransomware attackers collected over $2.1 billion in ransom payments during a three-year period that saw both explosive growth and a sudden decline in attack profitability, according to financial data analyzed by the U.S. Treasury Department's Financial Crimes Enforcement Network (FinCEN).
The agency processed thousands of Bank Secrecy Act reports filed by financial institutions, identifying 4,194 ransomware-related incidents between January 2022 and December 2024. Expanding the timeline back to 2013 brings total ransomware payments to approximately $4.5 billion—though the majority of that sum was paid in just the past three years.
The 2023 Peak and 2024 Decline
The year 2023 marked ransomware's most profitable period. Attackers executed 1,512 recorded attacks and collected roughly $1.1 billion in ransom payments, representing a 77% increase compared to 2022. This growth suggested ransomware was becoming more effective, more widespread, or both.
Then 2024 showed a different pattern. Incident numbers declined slightly to 1,476 attacks, but total ransom payments plummeted by nearly half—dropping to $734 million. This dramatic revenue decrease happened despite attack volumes remaining relatively stable.
Law Enforcement Impact
FinCEN analysts attribute the 2024 decline to targeted law enforcement operations against two dominant ransomware groups. The BlackCat (ALPHV) takedown in late 2023, followed by the compromise of LockBit's infrastructure in early 2024, disrupted the two most prolific ransomware operations.
Both groups dominated the ransomware ecosystem. Their disruption scattered members across smaller groups and forced some attackers to rebuild infrastructure from scratch. This created operational gaps that translated directly into reduced ransom collection.
The law enforcement actions demonstrated effectiveness, but they also revealed the challenge: dismantling individual groups doesn't eliminate the ransomware business model. Attackers regroup, rebrand, and resume operations. The question becomes whether periodic disruptions can suppress ransomware profitability enough to discourage new entrants.
Payment Patterns and Victim Profiles
Most ransom payments remained relatively modest—under $250,000 according to FinCEN data. This suggests attackers often target smaller organizations or negotiate down from initial demands. However, the total revenue numbers indicate enough high-value payments occurred to make ransomware highly profitable.
Manufacturing bore the brunt of attack volume with 456 recorded incidents. Financial services followed with 432 incidents, healthcare with 389, retail trade with 337, and legal services with 334. These sectors share common characteristics: digital dependencies, valuable data, and operational disruption costs that make paying ransoms tempting.
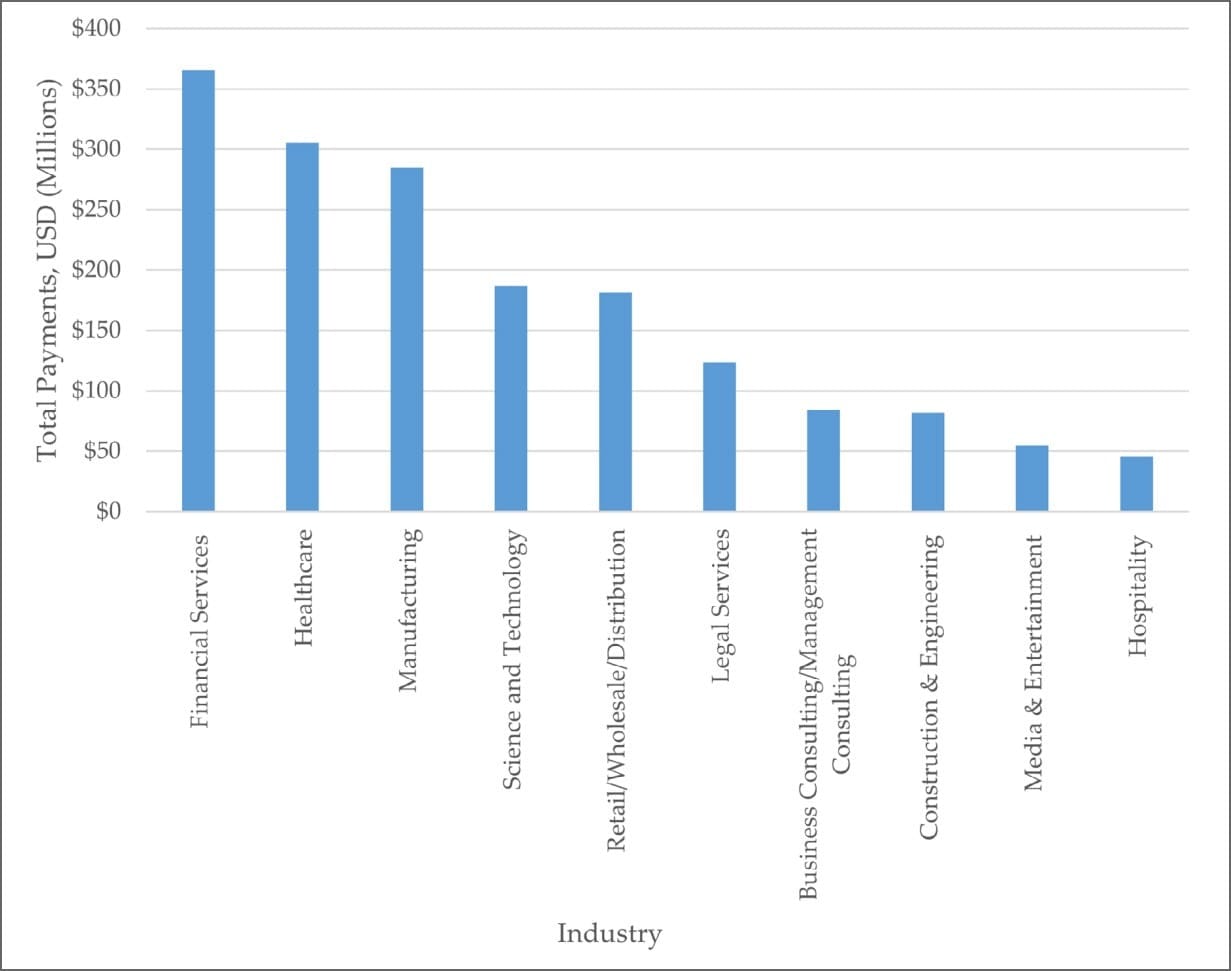
When measuring total ransom payments rather than incident counts, financial services leads with approximately $365.6 million paid. Healthcare follows at $305.4 million, manufacturing at $284.6 million, science and technology at $186.7 million, and retail at $181.3 million.
The disparity between incident counts and payment totals reveals targeting strategies. Manufacturing faces the most attacks but pays less per incident than financial services. Healthcare sits third in incident count but second in total payments, suggesting attackers successfully extract larger ransoms from medical organizations facing immediate patient care pressures.
Dominant Groups and Malware Families
FinCEN identified 267 different ransomware malware families, but concentration remained extreme. A handful of groups generated the vast majority of revenue.
Akira ransomware led in report mentions with 376 cases. However, ALPHV/BlackCat topped the profitability rankings, collecting approximately $395 million in ransom payments before law enforcement intervention. LockBit ranked second with $252.4 million. The top ten groups—including Black Basta, Royal, BianLian, Hive, Medusa, and Phobos—collected roughly $1.5 billion between 2022 and 2024.
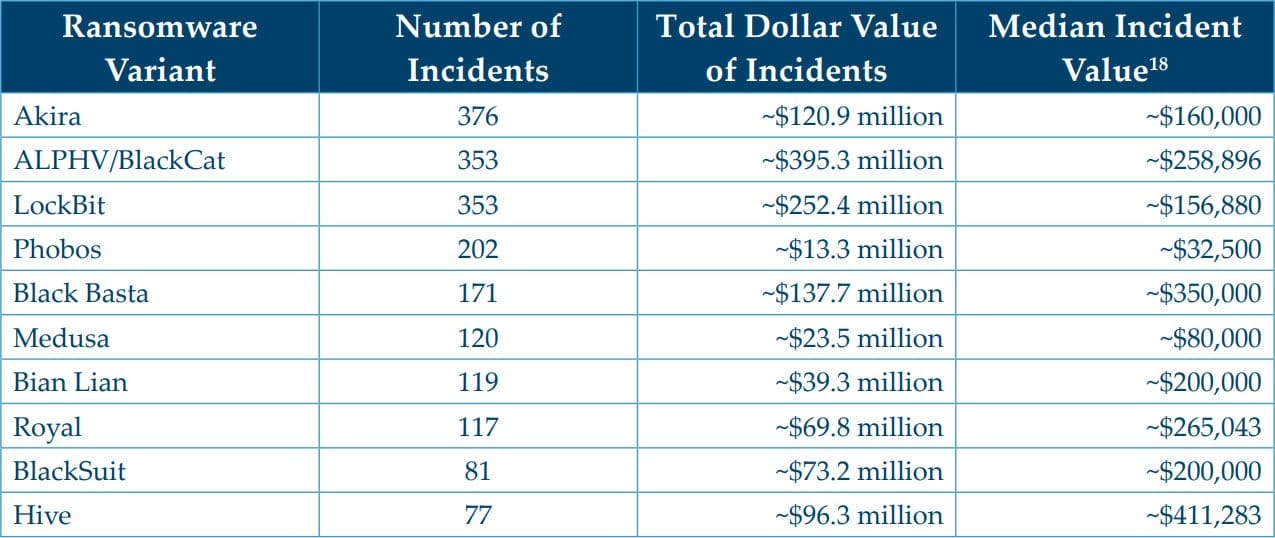
This concentration pattern shows ransomware operates more like an industry with dominant players than a scattered criminal activity. A few well-organized groups capture most revenue, while hundreds of smaller operations generate minimal returns.
Bitcoin Remains Dominant Payment Method
Bitcoin accounted for 97% of ransom payments despite growing concerns about blockchain traceability. Monero, Ether, Litecoin, and Tether saw minimal use. This Bitcoin dominance persists even though privacy-focused cryptocurrencies like Monero offer better anonymity.
The preference likely reflects Bitcoin's liquidity and established exchange infrastructure rather than anonymity features. Attackers need to convert ransoms into usable funds, and Bitcoin provides more offramps than alternatives.
In My Opinion
The 2024 decline in ransom payments represents a significant development, but interpreting it requires caution. Law enforcement disruptions clearly impacted the two largest groups, creating temporary gaps in ransomware operations. However, this doesn't necessarily indicate a permanent trend.
Per the research findings, the concentration of revenue among top groups creates both vulnerability and resilience in the ransomware ecosystem. Disrupting major groups causes immediate revenue drops, as we saw in 2024. But the underlying economics remain attractive—$734 million in a "down year" still represents substantial criminal profit.
The sector targeting patterns reveal why ransomware persists despite enforcement efforts. Healthcare organizations face impossible choices when ransomware threatens patient care systems. Financial services firms risk regulatory penalties and customer data exposure. Manufacturing operations lose production revenue for every hour systems remain encrypted. These pressures make paying ransoms rational from individual organizational perspectives, even though collective payment behavior sustains the ransomware economy.
The payment size distribution—mostly under $250,000—suggests attackers calibrate demands based on victim ability to pay. This pricing strategy maximizes payment likelihood rather than demanding unaffordable sums. It's business strategy applied to cybercrime.
Bitcoin's continued dominance deserves attention. Despite years of discussion about cryptocurrency traceability and law enforcement blockchain analysis capabilities, attackers still overwhelmingly choose Bitcoin for ransom payments. This indicates either that traceability concerns are overstated, that attackers have effective laundering methods, or that Bitcoin's practical advantages outweigh privacy risks.
The fundamental policy question remains unresolved: should organizations pay ransoms? Individual rational decisions—paying to restore operations quickly—collectively fund the ransomware industry. But organizations facing operational shutdowns can't be expected to prioritize collective security over immediate survival.
The 2024 data provides some encouragement. Targeted law enforcement operations can meaningfully disrupt ransomware revenue, at least temporarily. Whether this creates enough operational friction to suppress the business model long-term remains uncertain. The $734 million collected in 2024, even after major group takedowns, suggests ransomware remains highly profitable despite increased law enforcement attention.


