Ransomware Group Claims Massive Data Theft from Asus Supplier

Asus confirmed that one of its suppliers suffered a ransomware attack, though the company maintains its own systems remain secure. The Everest ransomware group, however, tells a different story—claiming to have stolen one terabyte of data from three companies: Asus, Qualcomm, and ArcSoft.
What Asus Says
The company's official statement acknowledges the breach but limits the scope. Representatives say attackers accessed portions of source code for smartphone camera software through a supplier compromise. Asus insists no damage occurred to its internal systems, products, or customer data. The company is now reinforcing supply chain security measures but declined to identify the compromised supplier or specify exactly what data was stolen.
What the Hackers Claim
The Everest group posted screenshots of allegedly stolen files on its darknet leak site, painting a far broader picture. The attackers claim their haul includes binary segmentation modules, source code and patches, RAM dumps and memory logs, AI models and weights, internal OEM tools and firmware, test videos and dual-camera calibration data, image datasets, crash logs and debug reports, HDR and post-processing operation information, test APKs and experimental applications, scripts and automation solutions, and binary calibration files.
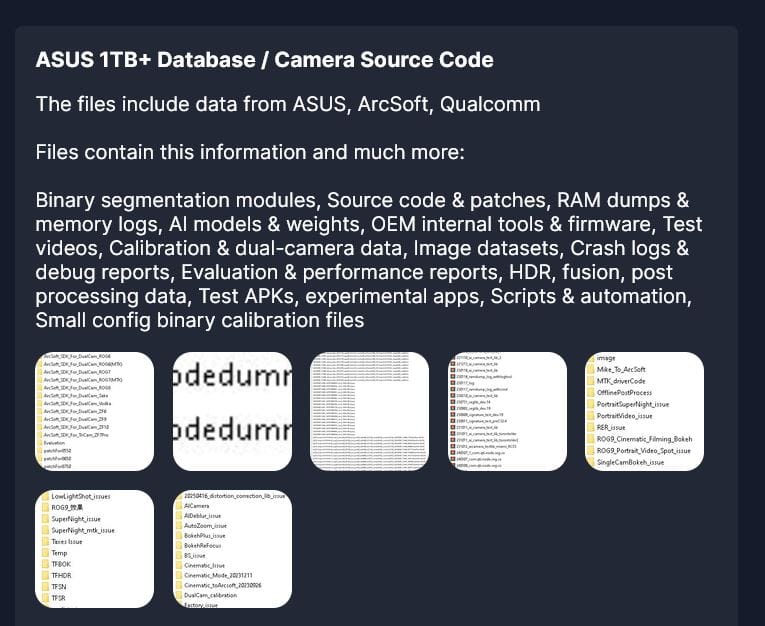
This list represents the technical foundation of smartphone camera systems—from the AI models that enhance photos to the calibration data that ensures cameras work properly.
Unanswered Questions
Asus has not addressed whether the Everest group's claims are accurate. The company also hasn't clarified whether Qualcomm and ArcSoft were actually affected. Neither company responded to media requests for comment.
A critical question remains unresolved: do the stolen materials belong to Asus alone, or do they include intellectual property from its partners? Supply chain attacks create this exact problem—compromising one vendor can expose multiple companies' sensitive data.
In My Opinion
This incident highlights a persistent security challenge: companies can maintain strong internal defenses yet remain vulnerable through their suppliers. Asus may have done everything right on its end, but one compromised vendor potentially exposed proprietary technology from multiple organizations.
The smartphone camera software ecosystem is tightly integrated. Source code, AI models, and calibration data from one vendor often connects to systems from others. A breach at the supplier level doesn't just affect one company—it can cascade across the entire supply chain.
Per the research findings, the Everest group's specific claims about stolen data suggest deep system access, not a surface-level breach. If accurate, this goes beyond typical ransomware attacks that encrypt files for ransom. The attackers appear to have systematically exfiltrated technical documentation and intellectual property.
For now, we're left with competing narratives: Asus minimizing the breach, and the Everest group claiming widespread data theft from multiple tech giants. The truth likely sits somewhere between these positions, but without confirmation from all involved parties, the full scope remains unclear.


