PolarEdge Botnet Targets Cisco, ASUS, QNAP and Synology Devices

Researchers at Sekoia have mapped the internal structure of the PolarEdge botnet, a modular backdoor campaign that consolidates infected networking and NAS devices into a distributed botnet. First described in February 2025, PolarEdge has since been linked to attacks against Cisco, ASUS, QNAP, and Synology hardware; however, the operators’ ultimate goals remain unclear.
Timeline and discovery
Censys analysts expanded the public picture in August 2025, noting that PolarEdge shares traits with Operational Relay Box (ORB) networks and that activity may date back to June 2023. In the February 2025 incidents, actors exploited a known Cisco router flaw (CVE-2023-20118) to fetch an FTP-served shell script named q. That script downloaded and executed the PolarEdge backdoor on compromised appliances.
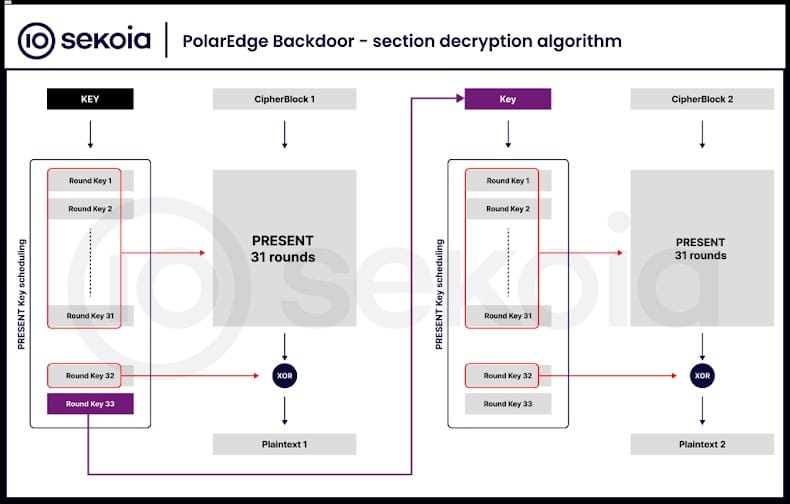
How the backdoor communicates
According to Sekoia, the primary backdoor behavior is straightforward: it collects host telemetry, sends it to a command-and-control (C2) server, then waits for instructions via a built-in TLS server implemented with mbedTLS.
PolarEdge supports two operational modes:
- Reverse mode: The backdoor behaves as a TLS client to download files from a remote host.
- Debug mode: The backdoor enters an interactive state for configuration changes, including updating server addresses.
Configuration data is embedded in the final 512 bytes of the ELF binary and is obfuscated with a single-byte XOR key (0x11). By default the component runs as a TLS server, accepting a custom binary protocol that parses fields such as HasCommand and Command.
When HasCommand equals the ASCII character 1, the backdoor executes the payload in the Command field and returns the command output to the operator.
Local effects and post-exploit actions
On execution, PolarEdge performs a number of local operations, including moving or leveraging /usr/bin/wget and /sbin/curl, and deleting specific files such as /share/CACHEDEV1_DATA/.qpkg/CMS-WS/cgi-bin/library.cgi.bak. The intended purpose of these file operations is not wholly clear from the current analysis.
Anti-analysis and process masquerading
The backdoor uses multiple anti-analysis techniques to hide its network-service footprint and its TLS configuration logic. During initialization it performs process masquerading, randomly adopting a name from a hardcoded list (for example: igmpproxy, wscd, /sbin/dhcpd, httpd, upnpd, iapp) to blend with legitimate processes and avoid simple detection heuristics.
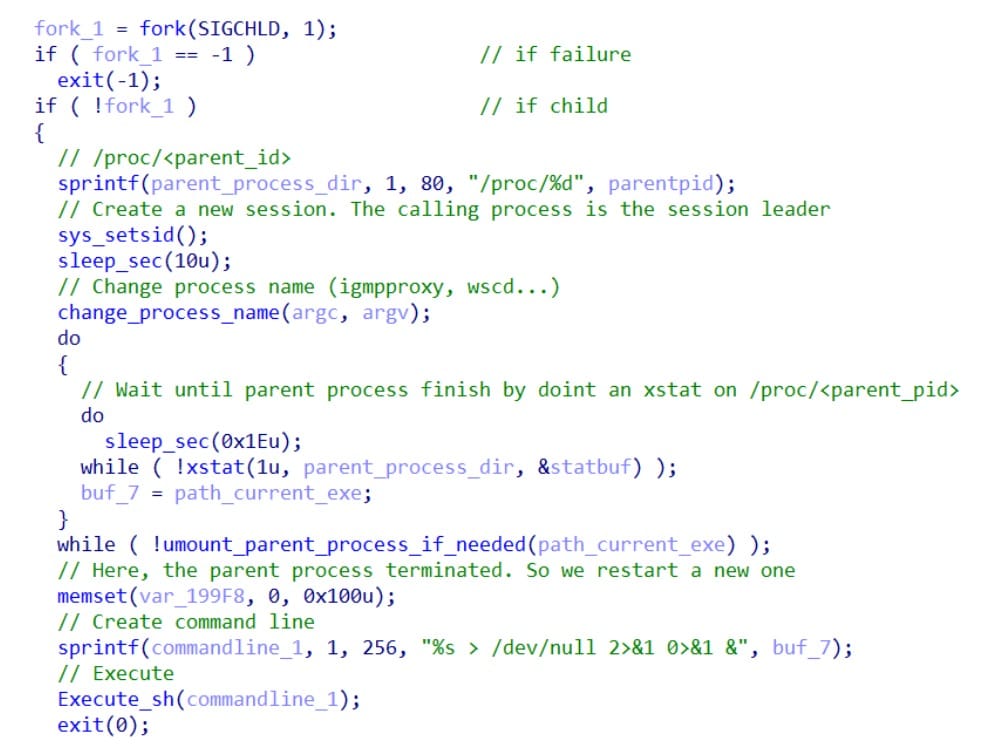
Persistence model
PolarEdge does not guarantee persistence across a full reboot. Instead it uses a lightweight resilience mechanism: the main process forks a child that monitors the parent every 30 seconds by checking for /proc/<parent-pid>. If the parent disappears, the child executes a shell command to relaunch the backdoor. This technique gives the malware an opportunistic, reboot-independent restart capability without installing traditional persistent services.
Why this matters
The campaign illustrates how attackers weaponize appliance-level vulnerabilities to weaponize edge devices into relayable attack infrastructure. Because many embedded devices run minimal monitoring and infrequent updates, router and NAS ecosystems offer attractive targets for long-running botnets that can be repurposed for DDoS, proxying, data exfiltration, or later lateral movement.
Open questions
- What is the operator’s primary intent espionage, DDoS-for-hire, proxying, or something else?
- Are current device firmware update mechanisms and vendor telemetry sufficient to detect similar campaigns early?
- How widespread is cleanup capability given the backdoor’s lightweight restart method but lack of true persistence?


