Phishing Service 'Spiderman' Targets European Banks and Crypto Services

Researchers from Varonis have discovered a new Phishing-as-a-Service (PhaaS) platform called Spiderman, which targets users of banks and cryptocurrency services in Europe. Attackers use the service to create copies of legitimate websites to steal login credentials, two-factor authentication (2FA) codes, and bank card information.
Per the researchers, the platform targets financial institutions in five European countries and major banks including Deutsche Bank, ING, Comdirect, Blau, O2, CaixaBank, Volksbank, and Commerzberg.
However, the attacks are not limited to banks. Spiderman can also create phishing pages for fintech services like Sweden's Klarna and PayPal. In addition, the platform supports stealing seed phrases for crypto wallets like Ledger, Metamask, and Exodus.
"Spiderman is modular, making it easy to add new banks, portals, and authentication methods. As European countries update their online banking systems, the service is likely to evolve in parallel," Varonis notes.
Through the Spiderman web panel, operators can monitor victim sessions in real-time, export data with a single click, intercept credentials and one-time passwords on the fly, and collect bank card information (including PhotoTAN codes).
PhotoTAN is a one-time password system widely used by European banks. When logging in or confirming a transaction, the user is shown a colored mosaic that must be scanned with the bank's mobile application. The app decodes the mosaic, generates an OTP for the specific transaction, and the user enters this code on the website.
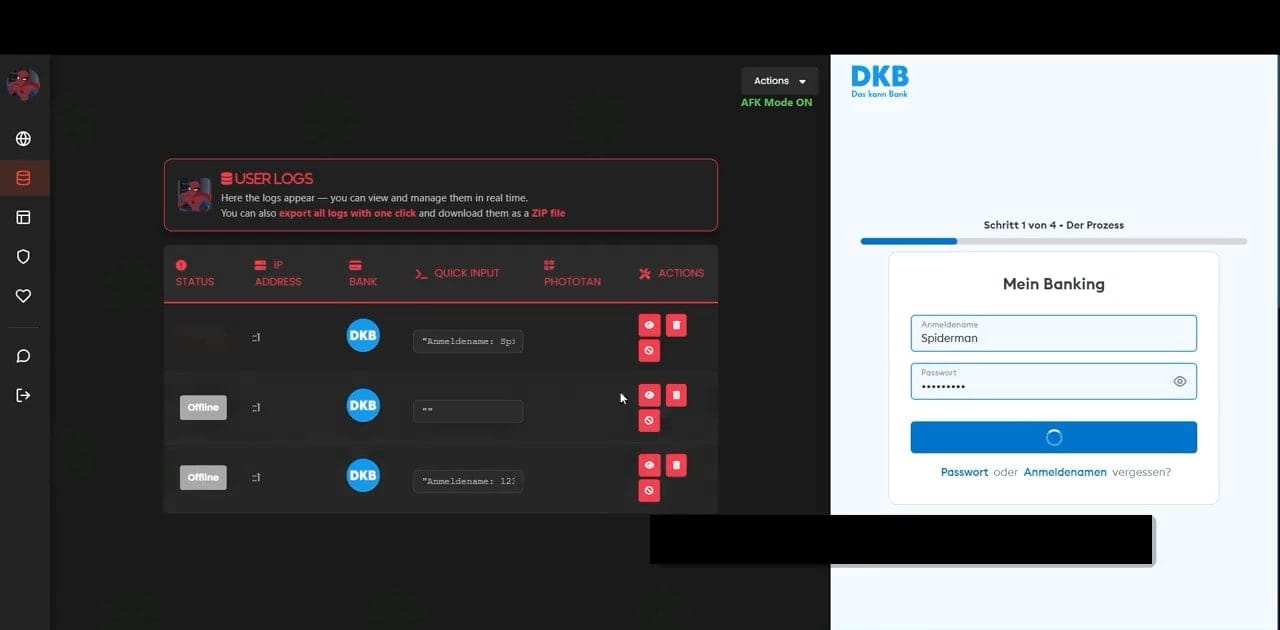
Spiderman operators also have access to targeting settings via the control panel. Attacks can be limited to specific countries, providers can be added to a whitelist, victims can be filtered by device type (mobile or desktop users), and redirects can be configured for visitors who are not suitable for phishing.
Researchers note that all phishing kits rely on the victim clicking a link and navigating to a fake login page. The best defense against such attacks is to carefully check the domain before entering credentials. Users should also be wary of fake browser-in-the-browser windows, which can display a correct URL.