Phishers Are Using the npm Infrastructure to Target Industrial and Technology Companies

Threat actors are exploiting the legitimate npm infrastructure in a new phishing campaign dubbed Beamglea. Unlike typical npm-based attacks, these malicious packages do not execute harmful code locally. Instead, they abuse the legitimate unpkg[.]com CDN service to host and display phishing pages to victims.
In late September, security researchers from Safety detected 120 npm packages linked to the campaign. That number has since grown to more than 175, according to security firm Socket.
The packages were designed to target over 135 organizations in the energy, industrial, and technology sectors. Among the victims are Algodue, ArcelorMittal, Demag Cranes, D-Link, H2 Systems, Moxa, Piusi, Renishaw, Sasol, Stratasys, and ThyssenKrupp Nucera. Most attacks have focused on Western Europe, with additional targets in Northern Europe and the Asia-Pacific region.
In total, the malicious packages have been downloaded over 26,000 times. However, many of these downloads are believed to come from researchers, automated scanners, and analysis tools rather than actual victims.
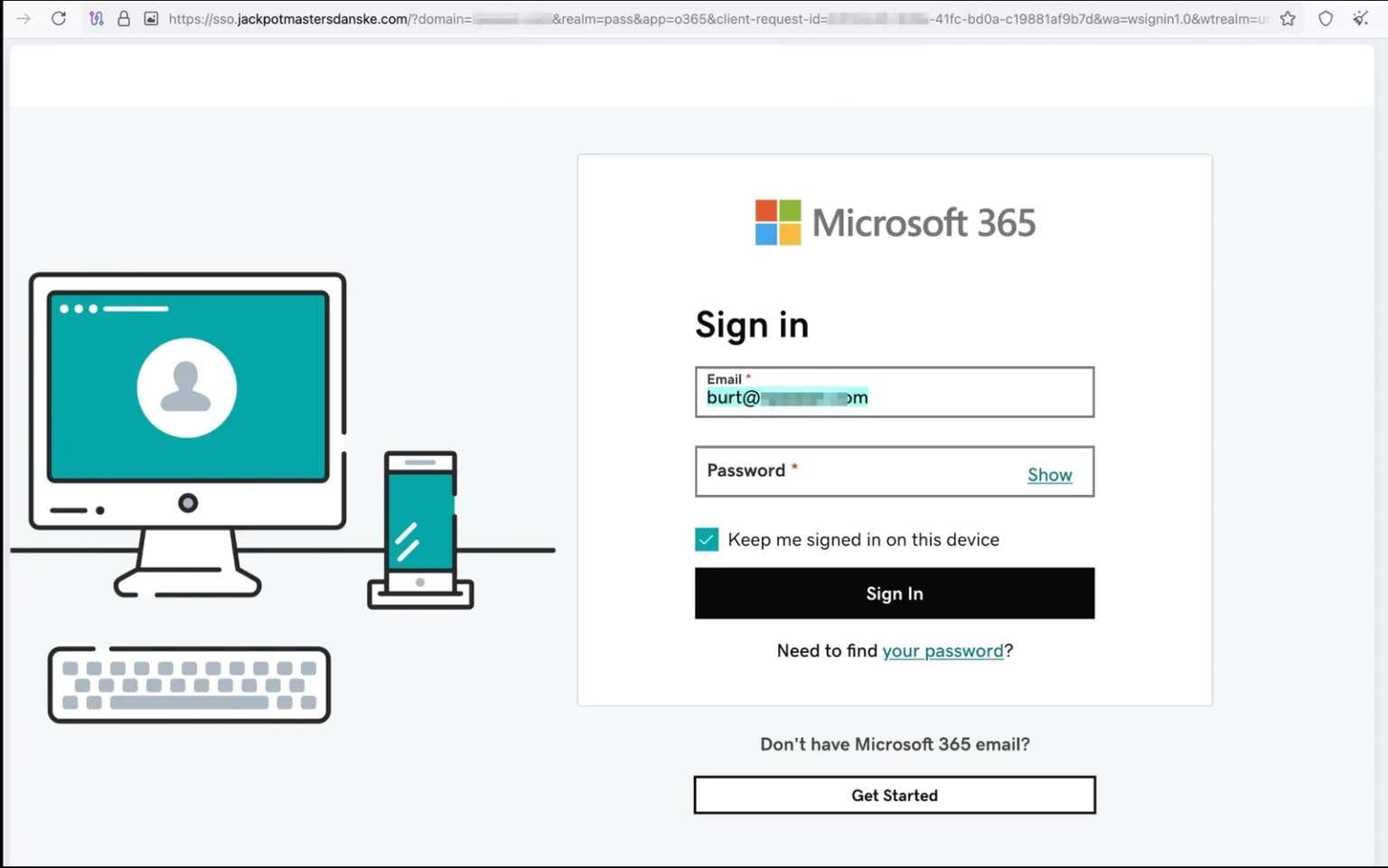
How the Attack Works
The malicious packages follow a consistent naming pattern:redirect-[a-z0-9]{6} — a random six-character string appended to “redirect.”
Once published on npm, they immediately become accessible through unpkg[.]com HTTPS CDN links.
According to Socket, “the attackers can distribute HTML files among target users, disguised as purchase orders and project documents. While the exact delivery method remains unclear, the business-related themes and victim-specific customization suggest delivery through email attachments or phishing links.”
When a victim opens one of these malicious HTML files, JavaScript from the npm package is loaded via unpkg[.]com, redirecting the user to a phishing page that prompts for credentials.
Automation Behind the Campaign
Researchers also discovered that the attackers are using a Python toolkit to automate the process. The script checks whether a victim is logged in, requests credentials, injects the stolen email and phishing URL into a JavaScript template (beamglea_template.js), generates a package.json, publishes it as a public package, and creates a corresponding HTML file linking back to the npm package via unpkg[.]com.
“This automation allowed the attackers to create 175 unique packages targeting different organizations without manually handling each victim,” Socket reported.
Phishing Pages and Campaign Indicators
Researchers observed more than 630 HTML files associated with the campaign, each containing the identifier nb830r6x in its meta tags. The phishing files mimic purchase orders, technical specifications, and project documentation.
“When victims open the HTML files, JavaScript immediately redirects them to the phishing domain, passing the victim’s email address in the URL fragment. The phishing page then pre-populates the email field, creating the illusion of a legitimate portal that already recognizes the user,” experts explained.
Additional Findings
Researchers from Snyk have identified additional npm packages using the "mad-*" naming scheme that exhibit similar behavior, though they are not yet conclusively tied to Beamglea.
“The package contains a fake Cloudflare Security Check page that covertly redirects users to an attacker-controlled domain fetched from a remote GitHub file,” Snyk noted.


