PassiveNeuron Targets Windows Servers in Global Attack Campaign

Researchers from Kaspersky Lab have uncovered a new wave of PassiveNeuron infections that ran from December 2024 to August 2025, targeting government, financial, and industrial organizations across Asia, Africa, and Latin America. The campaign’s most notable feature is its focus on Windows Server operating systems, which form the backbone of enterprise infrastructure.
In one confirmed case, attackers successfully executed remote commands on a compromised server through Microsoft SQL, highlighting the group’s focus on high-value server assets.
Tools and Techniques
The PassiveNeuron campaign first surfaced in June 2024, went quiet for several months, and then resumed activity at the end of the year. This new phase introduced three core tools:
- Cobalt Strike – a legitimate penetration-testing framework often misused for post-exploitation.
- Neursite backdoor – a modular tool capable of collecting system information, managing processes, and tunneling network traffic to enable lateral movement.
- NeuralExecutor implant – a custom .NET-based component capable of receiving and executing payloads from command-and-control (C2) servers using multiple communication methods.
Samples analyzed by Kaspersky indicated that Neursite communicated not only with external C2 infrastructure but also with compromised internal systems, suggesting that the attackers had established multiple persistence channels.
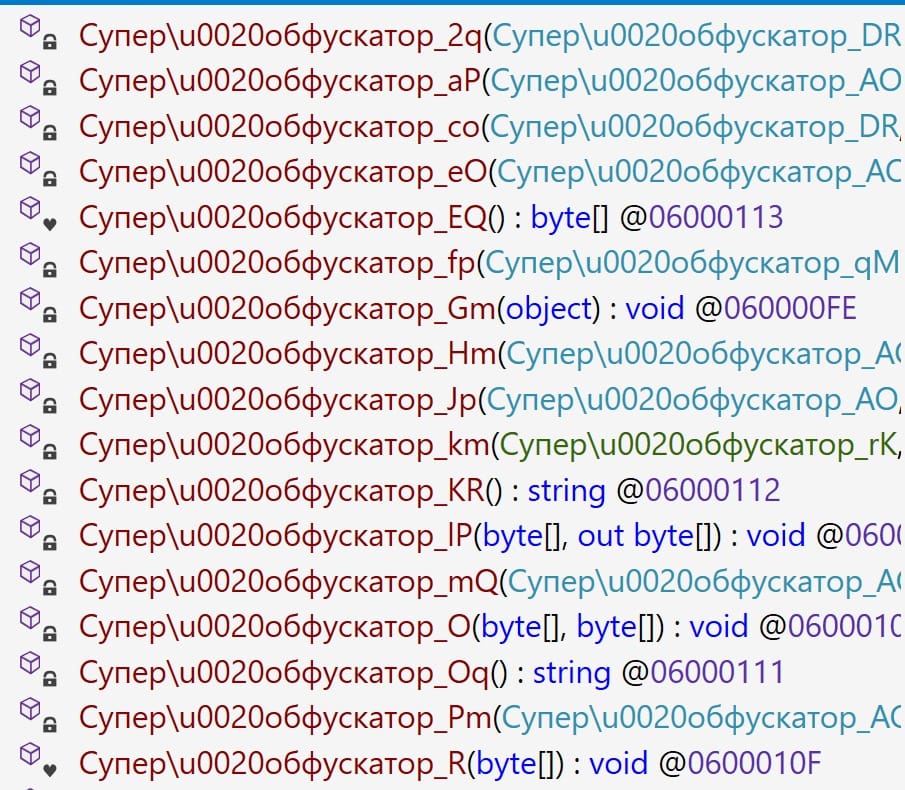
Attribution and Artifacts
During the analysis, researchers noticed that function names in the code were replaced with Cyrillic strings, a deliberate move that could serve as a false flag. Attribution remains uncertain, but based on the tactics, techniques, and procedures (TTPs) observed, Kaspersky currently associates the activity with a Chinese-speaking threat group—though only with low confidence.
Expert Commentary
“In the new PassiveNeuron campaign, the threat actors are focusing on compromising servers that form the backbone of corporate networks,” explained Georgy Kucherin, a security expert with Kaspersky GReAT. “Such systems, especially those exposed to the internet, are of high interest to advanced attackers. A single compromised host can open the door to critical infrastructure. Organizations must minimize their attack surface and continuously monitor server applications to detect and prevent intrusions.”
Summary
The PassiveNeuron campaign reinforces a familiar but dangerous trend: attackers shifting their attention from end-user systems to core infrastructure. The focus on Windows Server, use of Cobalt Strike, and introduction of custom backdoors point to a well-resourced operation designed for persistence and control inside large networks.
Regular monitoring, timely patching, and strict segmentation of exposed services remain key defenses against such targeted attacks.


