Operation SkyCloak: Advanced Espionage Campaign Targets Russian and Belarusian Defense Sectors

Cybersecurity researchers at Cyble and Seqrite Labs have uncovered a sophisticated espionage campaign targeting defense and government organizations in Russia and Belarus. The operation, designated Operation SkyCloak, deploys a custom backdoor that combines OpenSSH, Tor hidden services, and obfs4 traffic obfuscation to maintain persistent, anonymous access to compromised systems.

Attack Vector and Initial Compromise
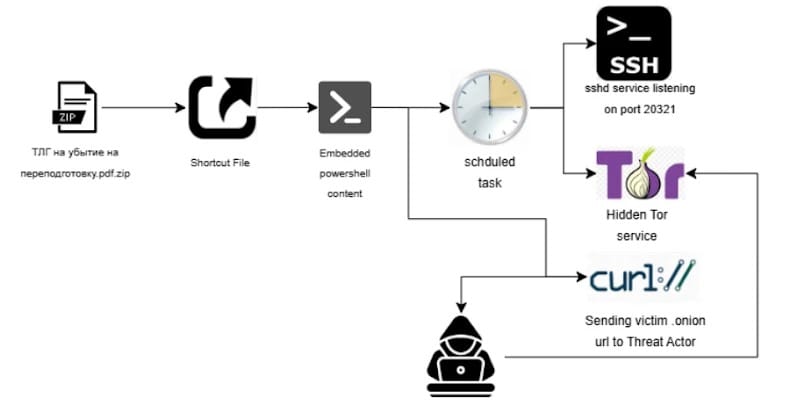
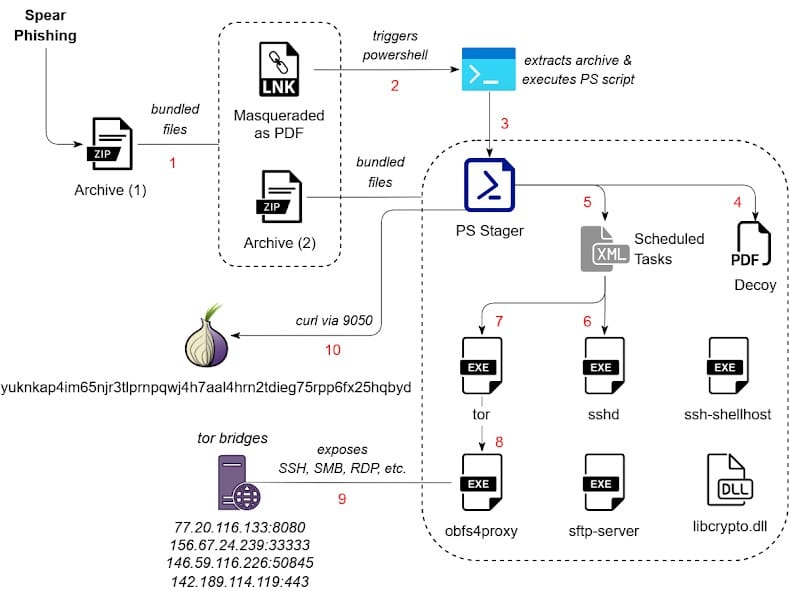
The campaign begins with spear-phishing emails containing military-themed lure documents. These emails direct recipients to open a ZIP archive that contains a deliberately complex structure designed to obscure malicious content:
- A hidden folder containing a second nested archive
- A Windows shortcut (LNK) file that initiates the infection chain
When the victim opens the LNK file, it triggers a multi-stage deployment process that installs the full malware payload.
Initial Execution Chain
The LNK file executes PowerShell commands representing the first-stage dropper. These commands extract and execute additional components from the nested archive structure. According to researchers, samples of these archives were uploaded to VirusTotal in October 2025 from IP addresses geolocated to Belarus, providing early indicators of the campaign's targeting and potential origin.
Anti-Analysis Mechanisms
The malware implements several environment checks to detect sandbox and analysis environments before proceeding with infection. A PowerShell stager component performs the following validation:
LNK file verification: The system must contain at least 10 recent LNK (shortcut) files Process count check: The number of running processes must be greater than or equal to 50
If either condition fails, the PowerShell script terminates immediately without deploying further stages.
These checks exploit common characteristics of analysis environments. Sandboxes typically exhibit fewer user shortcuts and reduced process activity compared to genuine workstations used for daily operations. In my opinion, this represents a straightforward but effective anti-analysis technique that can bypass many automated malware analysis systems.
Lure Deployment and Persistence
After passing environment validation, the malware executes two parallel actions:
Distraction: Displays a PDF document with military-related content to the victim, maintaining the illusion of a legitimate document opening Persistence establishment: Creates a scheduled task named githubdesktopMaintenance that ensures malware execution across system reboots
The scheduled task triggers automatically after user logon and runs daily at 10:21. This timing appears designed to blend with legitimate system maintenance activities that often occur during mid-morning hours when users are actively working.
SSH Backdoor Implementation
The persistence mechanism executes logicpro/githubdesktop.exe—a renamed legitimate sshd.exe file from the OpenSSH project. This technique, known as DLL side-loading or binary renaming, allows attackers to run legitimate remote access software while evading detection systems that monitor for suspicious process names.
The SSH service installation includes several security-focused configurations:
- Pre-installed cryptographic keys stored in the
logicprofolder for authentication - Restricted access controls limiting connections to attacker-controlled systems
- SFTP (SSH File Transfer Protocol) capabilities for data exfiltration and additional tool deployment
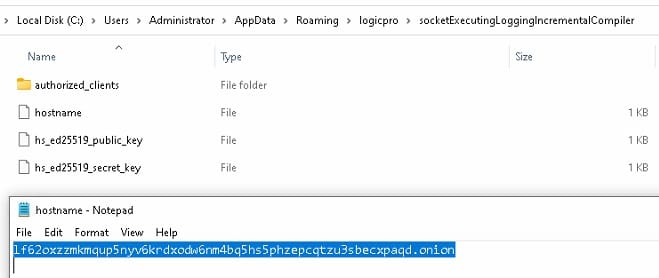
Per the researchers' analysis, all files are stored in C:\Users\<Username>\AppData\Roaming\logicpro\socketExecutingLoggingIncrementalCompiler—a deliberately verbose path name designed to blend with legitimate application directories.
Tor Integration and Traffic Obfuscation
The malware creates a second scheduled task that executes logicpro/pinterest.exe—a customized Tor binary. This component establishes a hidden service that allows attackers to communicate with compromised systems through the Tor anonymity network.
The Tor implementation includes advanced obfuscation:
obfs4 (obfuscation protocol 4): A pluggable transport that makes Tor traffic appear as random data rather than identifiable Tor packets Hidden service architecture: Creates a unique .onion address for each compromised system Bidirectional anonymity: Protects both the victim's location and the attacker's command and control infrastructure
The malware writes an attacker-controlled onion address (yuknkap4im65njr3tlprnpqwj4h7aal4hrn2tdieg75rpp6fx25hqbyd[.]onion) to a file named hostname within the infection directory. This address serves as the command and control endpoint for the backdoor.
In my experience analyzing state-sponsored malware, the use of obfs4 with Tor hidden services represents a sophisticated approach to maintaining operational security. This combination makes network-based detection extremely difficult because the traffic appears as encrypted noise rather than recognizable malware communications.
Port Forwarding and Service Exposure
Beyond SSH access, the malware performs port forwarding for multiple Windows services:
RDP (Remote Desktop Protocol): Provides graphical remote access to the compromised system SSH (Secure Shell): Enables command-line access and file transfer SMB (Server Message Block): Allows file sharing and network resource access
All forwarded services route through the Tor hidden service, ensuring attackers maintain complete anonymity while accessing victim systems. This architecture prevents network monitoring from identifying attacker infrastructure or origin points.
System Reconnaissance and Identification
After establishing the backdoor infrastructure, the malware collects system information including:
- Operating system version and configuration
- Network configuration details
- Installed software inventory
- User account information
- Domain membership status
The malware generates a unique .onion URL hostname to identify each compromised machine within the attackers' infrastructure. This information is transmitted to the command and control server using curl, a legitimate command-line tool for transferring data.
The use of curl rather than custom network code provides several advantages: it's a standard Windows component (in Windows 10 and later), generates less suspicious network traffic, and reduces the malware's code footprint.
Post-Compromise Capabilities
Once the backdoor is fully operational, attackers gain comprehensive remote access through multiple channels:
SSH: Command execution, scripting, and automated task performance RDP: Interactive desktop access for manual operations SFTP: Secure file transfer for data exfiltration and tool deployment SMB: Network resource access and lateral movement preparation
All communications route through Tor hidden services using pre-installed cryptographic keys for authentication. This architecture ensures that even if network defenders detect unusual traffic patterns, they cannot determine the attacker's true location or identify command and control infrastructure.
"The attackers gain access to all critical services through Tor hidden services, ensuring complete control over the system while maintaining anonymity. All communications are routed through anonymous addresses using pre-installed cryptographic keys," the researchers state in their report.
Attribution Assessment
Precise attribution remains challenging based on available evidence. However, several indicators suggest the campaign's potential origins and sponsorship:
Geographic targeting: Focus on Russian and Belarusian defense and government sectors Lure content: Military-themed documents relevant to regional security concerns Technical sophistication: Advanced obfuscation techniques and operational security measures Infrastructure indicators: Initial samples uploaded from Belarus
Cyble researchers note potential links to UAC-0125, a threat actor group previously associated with cyber-espionage operations in the region. However, definitive attribution requires additional intelligence beyond technical indicators.
The researchers assess that the targeting of defense and government sectors, combined with the campaign's technical sophistication and operational security measures, suggests state-sponsored actors rather than financially-motivated cybercriminals. State-sponsored groups typically invest more resources in stealth and persistence because their objectives involve long-term intelligence collection rather than immediate financial gain.
Geopolitical Context
The targeting of Russian and Belarusian defense sectors occurs within a complex regional security environment. Multiple state actors maintain active cyber-espionage programs focused on gathering military and strategic intelligence from these countries.
Without making definitive attribution claims, potential sponsor states for such operations would likely include:
- NATO member countries with intelligence interests in Russian and Belarusian military capabilities
- Regional powers concerned about military developments in Russia and Belarus
- Countries in ongoing conflicts or tensions with Russia
The use of military-themed lures suggests the attackers possess specific knowledge of topics that would interest defense sector personnel, indicating prior intelligence collection or regional expertise.
Detection and Mitigation Strategies
Organizations in the defense and government sectors should implement several defensive measures to detect and prevent Operation SkyCloak infections:
Email Security
- Deploy advanced email filtering that analyzes attachment structures for nested archives
- Implement sandboxing for all email attachments before delivery to end users
- Train personnel to recognize spear-phishing attempts, particularly those with military or security-related lures
Endpoint Security
- Monitor for suspicious LNK file executions, especially those invoking PowerShell
- Deploy endpoint detection and response (EDR) solutions capable of detecting renamed legitimate binaries
- Implement application whitelisting to prevent unauthorized SSH and Tor binaries from executing
Network Monitoring
- Detect Tor traffic on enterprise networks and investigate any Tor connections from workstations
- Monitor for obfs4 traffic patterns, which can be identified through statistical analysis even when obfuscated
- Implement network segmentation to limit lateral movement opportunities
Scheduled Task Monitoring
- Audit scheduled tasks for suspicious names that mimic legitimate software (like "githubdesktopMaintenance")
- Monitor for scheduled tasks created by non-administrative users or processes
- Implement alerting for scheduled tasks that execute from user AppData directories
Service Port Monitoring
- Detect unauthorized SSH services running on non-standard ports
- Monitor for unusual RDP connections, especially those originating from localhost or loopback addresses
- Alert on SMB connections from unexpected sources or to unexpected destinations
PowerShell Security
- Enable PowerShell logging and script block logging to capture command execution
- Implement constrained language mode for PowerShell where possible
- Monitor for PowerShell execution from unexpected parent processes like shortcuts
Indicators of Compromise
Organizations should search for the following IOCs associated with Operation SkyCloak:
File paths:
C:\Users\<Username>\AppData\Roaming\logicpro\- Files named
githubdesktop.exeorpinterest.exein user directories
Scheduled tasks:
githubdesktopMaintenance- Tasks executing from the
logicprodirectory
Network indicators:
- Connections to
yuknkap4im65njr3tlprnpqwj4h7aal4hrn2tdieg75rpp6fx25hqbyd[.]onion - Tor traffic from workstations
- obfs4 protocol signatures
Process indicators:
- Renamed
sshd.exebinaries - Customized Tor binaries running from non-standard locations
- curl.exe making connections to .onion addresses
Industry Implications
Operation SkyCloak demonstrates the continuing evolution of state-sponsored cyber-espionage capabilities. The campaign's technical sophistication—particularly the integration of Tor hidden services with obfs4 obfuscation—represents an advanced approach to maintaining persistent access while evading detection.
The targeting of defense sectors in Russia and Belarus highlights how cyber-espionage operations increasingly focus on gathering strategic military intelligence. As geopolitical tensions persist in various regions, we should expect continued investment in cyber capabilities designed to penetrate defense and government networks.
Furthermore, the campaign's use of legitimate tools (OpenSSH, Tor, curl) rather than custom malware reflects a broader industry trend toward "living off the land" techniques. These approaches leverage built-in operating system capabilities and legitimate software to evade detection, making defense more challenging.
Bottom Line
Operation SkyCloak represents a sophisticated cyber-espionage campaign targeting Russian and Belarusian defense organizations through a combination of social engineering, anti-analysis techniques, and advanced anonymity infrastructure. The operation's use of Tor hidden services with obfs4 obfuscation, combined with multiple remote access channels, provides attackers with resilient, anonymous access to compromised systems. While precise attribution remains uncertain, the campaign's targeting, technical sophistication, and operational security measures strongly suggest state-sponsored actors seeking strategic military intelligence. Defense and government organizations should implement comprehensive detection and prevention measures, recognizing that modern cyber-espionage threats require defense-in-depth strategies addressing both technical controls and personnel awareness.


