Operation Endgame: Law Enforcement Takes Down Over 1,000 Servers for Rhadamanthys, VenomRAT, and Elysium

Law enforcement agencies from nine countries have dismantled over 1,000 servers used by the Rhadamanthys info-stealer, VenomRAT trojan, and Elysium botnet. This represents the latest phase of Operation Endgame, an international campaign against cybercrime coordinated by Europol and Eurojust.
International Cooperation
The operation brought together agencies from Australia, Canada, Denmark, France, Germany, Greece, Lithuania, the Netherlands, and the United States. Unlike previous phases, this action included specialists from numerous private security organizations: Cryptolaemus, Shadowserver, SpyCloud, Team Cymru, Proofpoint, CrowdStrike, Lumen, Abuse.ch, Have I Been Pwned, Spamhaus, DIVD, and Bitdefender.
The Takedown
From November 10-14, 2025, police conducted searches at 11 locations across Germany, Greece, and the Netherlands. The operation resulted in:
- 20 domains seized
- 1,025 malicious servers taken offline
- One key suspect linked to VenomRAT arrested in Greece on November 3
Earlier this week, dozens of Rhadamanthys customers reported losing access to their malware control panels, suggesting law enforcement involvement. The malware developers themselves speculated that German authorities were behind the disruption after detecting logins from German IP addresses before access to their European-hosted panels was lost. They were correct.
Scale of the Criminal Infrastructure
According to Europol, the disabled infrastructure controlled hundreds of thousands of infected computers containing several million stolen credentials. Many victims remained unaware their systems were compromised.
"The main suspect behind the info-stealer had access to more than 100,000 victims' cryptocurrency wallets, potentially containing millions of euros," Europol stated in its press release.
The agency now urges users to check their devices for infection through dedicated pages at politie.nl/checkyourhack and haveibeenpwned.com.
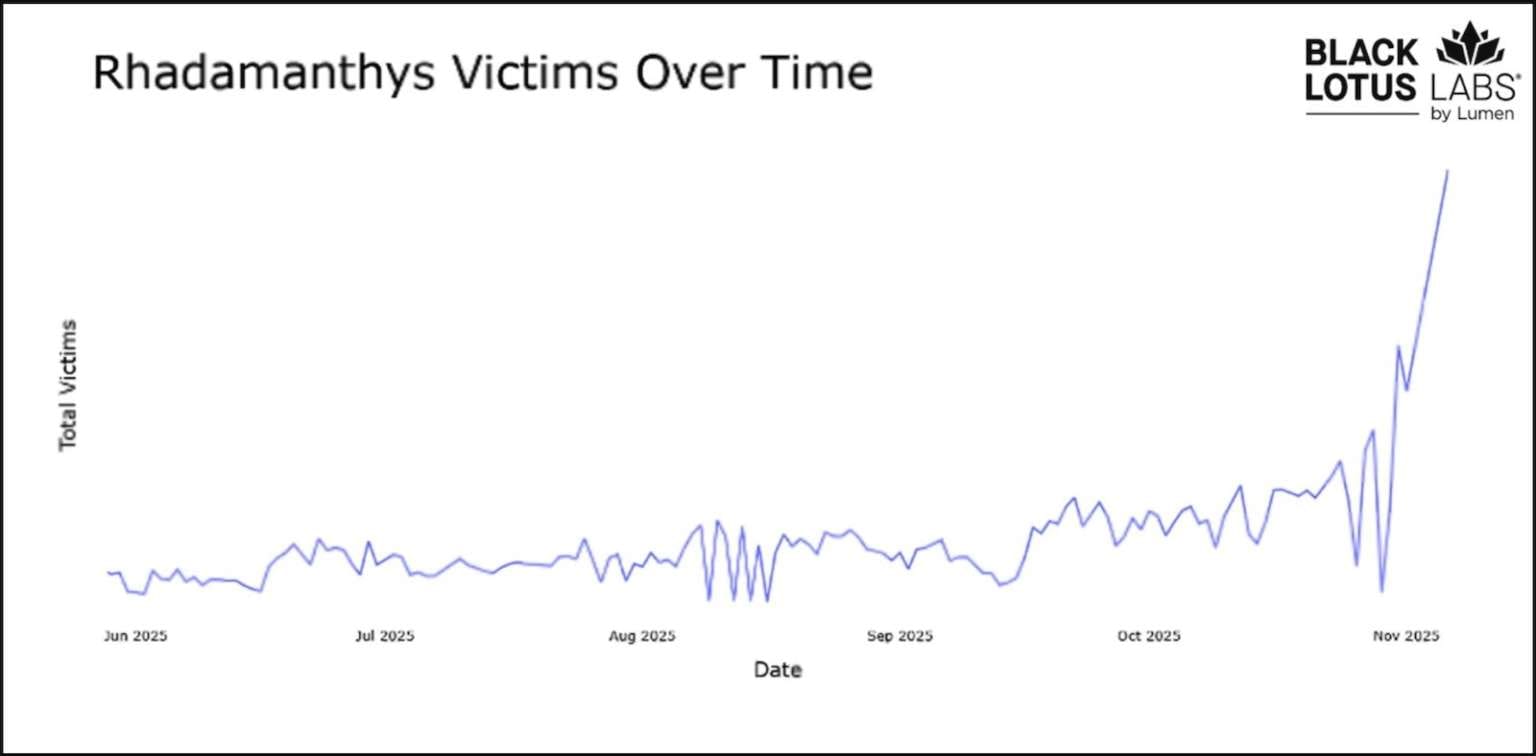
Rhadamanthys Activity Surge
Lumen specialists, who assisted in the operation, documented a sharp increase in Rhadamanthys activity during October-November 2025. Their analysis revealed:
- An average of 300 active servers daily
- A peak of 535 servers observed in October 2025
- Over 60% of command-and-control servers hosted in the U.S., Germany, U.K., and Netherlands
- More than 60% of Rhadamanthys C2 servers remained undetected on VirusTotal
"This explains the recent surge in infections in October 2025, when the malware was infecting an average of over 4,000 unique IP addresses daily," Lumen researchers noted.
Beyond Data Theft
The Shadowserver Foundation emphasized that Rhadamanthys infections likely led to additional malware installations on compromised systems.
"Other malware may also be active on these systems, which could require additional local remediation efforts," the organization warned. "Compromised systems may have been used in past or recent hacking and extortion incidents."
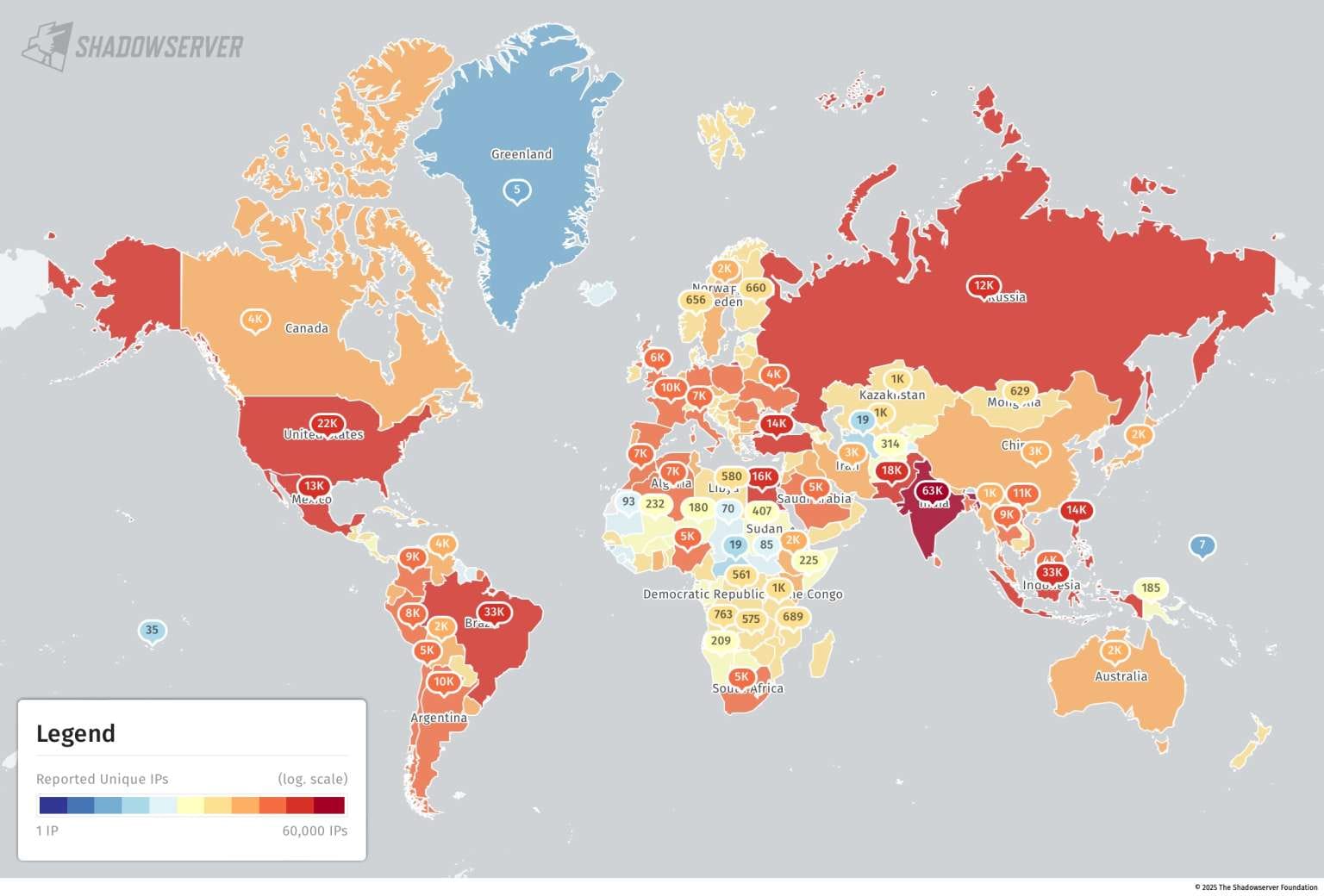
From March to November 2025, Shadowserver identified 525,303 Rhadamanthys infections, followed by over 86.2 million data theft events. Approximately 63,000 victim IP addresses were located in India.
Operation Endgame's Growing Impact
This latest action continues Operation Endgame's track record of disrupting major cybercrime infrastructure. Earlier phases took down:
- The AVCheck service
- Infrastructure for multiple malware families: SmokeLoader, DanaBot, IcedID, Pikabot, Trickbot, Bumblebee, and SystemBC
The operation demonstrates increasing cooperation between international law enforcement and private security firms in combating organized cybercrime at scale.


