Norton Researchers Exploit Flaw in Midnight Ransomware, Release Free Decryptor

Norton security researchers discovered a critical weakness in Midnight ransomware—a variant built on leaked Babuk source code from 2021. Despite positioning itself as an "advanced" version with improved encryption, the malware's developers made implementation mistakes that allowed Norton to create a free decryption tool for affected victims.
Technical Background
Midnight follows the same basic structure as Babuk, whose source code became public in 2021 and spawned dozens of ransomware variants. The developers attempted to strengthen the encryption by using ChaCha20 for file contents and RSA to protect the ChaCha20 key. However, Norton researchers identified an error in the RSA key implementation that first enabled partial data recovery, then led to development of a complete decryption solution.
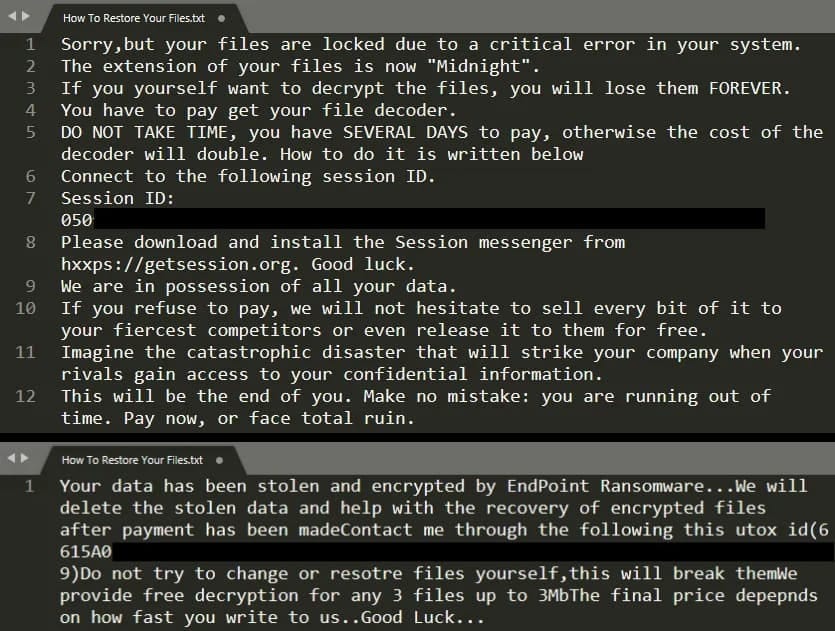
How Midnight Operates
Like Babuk, Midnight uses partial file encryption to increase speed and maximize system disruption before detection. The ransomware encrypts specific blocks within files—the amount depends on file size—making large documents and databases unreadable almost immediately. Recent builds expanded the target list to include nearly all file formats except executables (.exe, .dll, .msi).
On compromised systems, encrypted files receive either .midnight or .endpoint extensions, and sometimes this marker appears embedded in file content. Victims find a standard ransom note (How To Restore Your Files.txt) and occasionally operation logs named report.midnight or debug.endpoint showing the malware's execution details.
Free Decryption Tool Available
Norton released the decryption tool in both Windows x86 and x64 versions. The tool requires no specialized knowledge—it automatically searches for encrypted data, creates safety backups, and begins recovery. Norton strongly recommends keeping the automatic backup feature enabled to prevent accidental data loss during the decryption process.
Key Takeaway
This development demonstrates that ransomware built on recycled code—even with attempted improvements—can inherit or introduce new vulnerabilities. Organizations affected by Midnight ransomware can now recover their data without paying ransom demands.


