North Korean Hackers Stole Over $2 Billion in 2025

According to blockchain analysts at Elliptic, North Korean hackers stole more than $2 billion USD in cryptocurrency during the first nine months of 2025 — setting a new all-time record.
This brings the total confirmed amount of cryptocurrency stolen by DPRK-linked threat actors to over $6 billion USD. The United Nations and several U.S. government agencies believe these funds are being used to help finance North Korea’s nuclear weapons program.
Elliptic reports that the amount stolen in 2025 is nearly three times higher than in 2024, and significantly exceeds the previous record of $1.35 billion USD in 2022, when the Ronin Network and Harmony cross-chain bridge were attacked. The largest share of this year’s total stems from the Bybit exchange hack in February 2025, in which hackers stole approximately $1.46 billion USD.
Based on blockchain analysis, laundering activity, and related data, Elliptic attributes around 30 cryptocurrency thefts this year to North Korean operators. Other notable incidents in 2025 include attacks on LND.fi, WOO X, Seedify, and the Taiwanese exchange BitoPro, from which the Lazarus Group allegedly stole about $11 million USD.
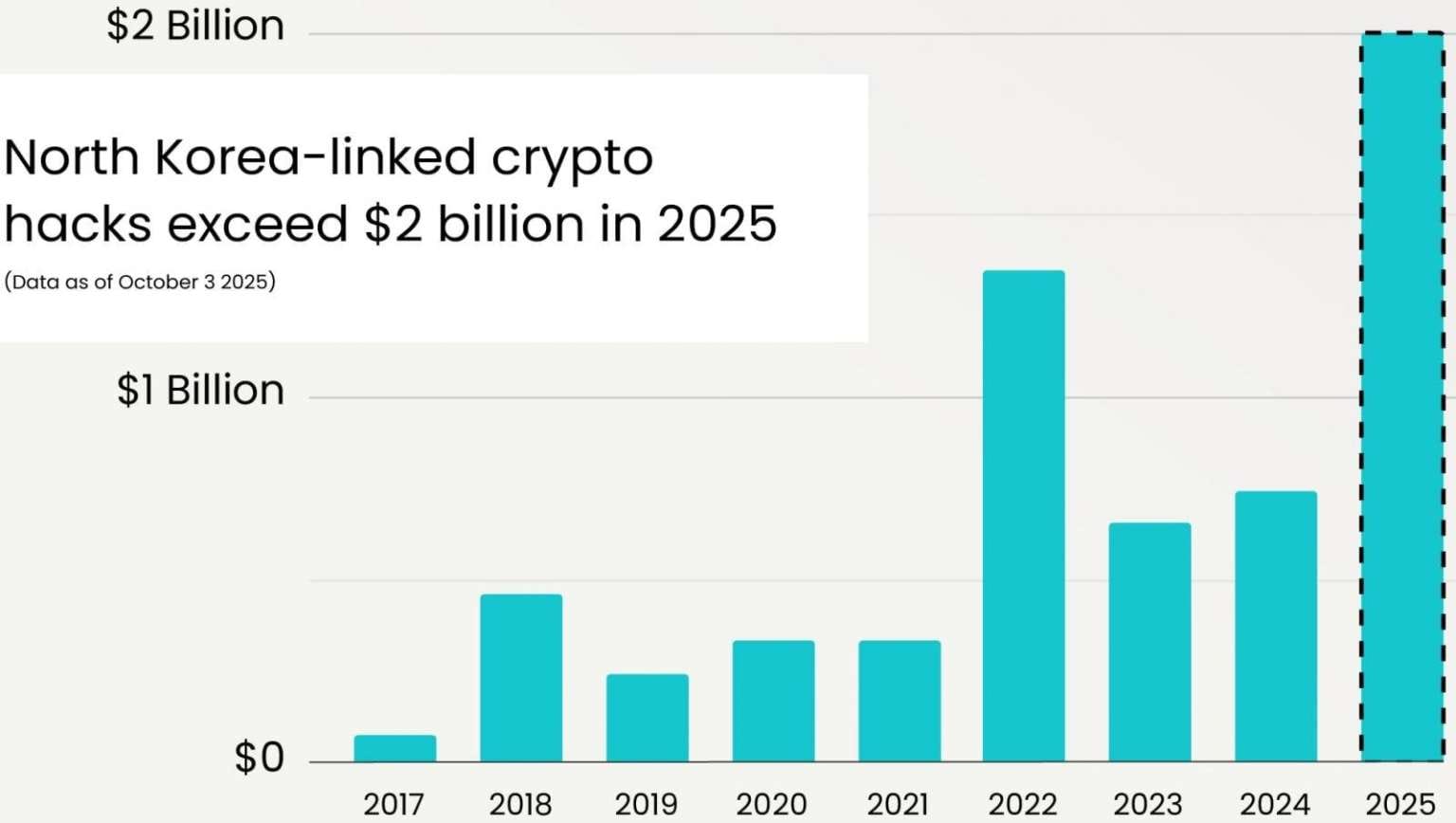
Elliptic stresses that these figures represent a conservative estimate, noting that many incidents remain unreported or lack sufficient attribution confidence.
A Shift in Strategy
Researchers identify one of the defining trends of 2025 as a tactical pivot from large-scale exchange breaches to targeted attacks on individuals — particularly high-value crypto holders and exchange employees. Social engineering now plays a growing role, replacing traditional exploitation of DeFi vulnerabilities as the main initial access vector.
Evolving Laundering Methods
Money laundering techniques are also becoming more sophisticated. North Korean groups are increasingly using multi-layered mixer operations, cross-chain transfers, lesser-known blockchains, and utility token purchases to obscure transaction origins. They also exploit return addresses and deploy custom tokens issued by laundering networks, creating a highly complex and resilient laundering infrastructure.


