North Korean Hackers Employ EtherHiding Tactic to Conceal Malware in the Blockchain

Google’s Threat Intelligence Group (GTIG) has uncovered a new North Korean cyber campaign that hides malware within blockchain smart contracts — a sophisticated evasion method known as EtherHiding.
According to GTIG, the group UNC5342 has used this technique since February 2025 in “Contagious Interview” operations aimed at stealing cryptocurrency from software developers. This marks the first known case of a state-sponsored threat actor deploying EtherHiding.
What Is EtherHiding?
The EtherHiding technique was first documented by Guardio Labs in 2023, when researchers observed threat actors embedding malicious code in Binance Smart Chain (BSC) contracts. The concept exploits the immutability and transparency of public blockchains: attackers can store and retrieve encrypted payloads within smart contracts, making them difficult to block or remove.
Because these payloads are fetched using read-only blockchain calls, no visible transaction record appears — providing both stealth and resilience. Updating a payload requires only minor contract modifications, allowing hackers to maintain persistence with minimal cost.
The New Campaign
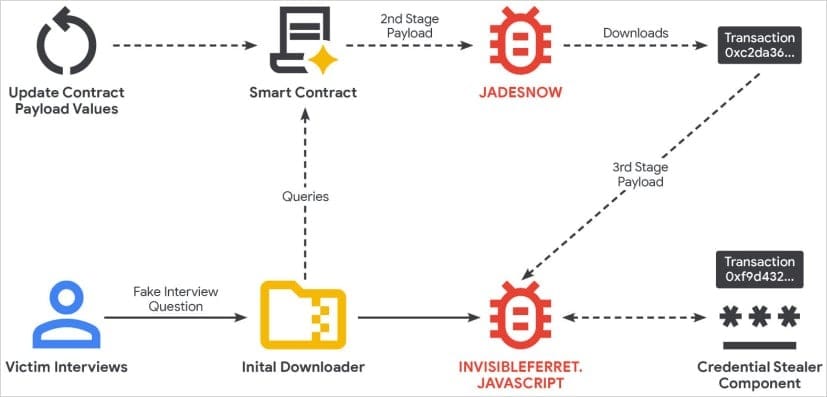
Google’s investigation revealed that UNC5342 used EtherHiding to target developers with fake job interviews. Attackers impersonated companies such as BlockNovas LLC, Angeloper Agency, and SoftGlide LLC, inviting candidates to complete “coding tests.”
When victims ran the provided code, it executed a JavaScript loader that connected to a smart contract hosting the JADESNOW loader. This intermediary payload then retrieved a third-stage script—a JavaScript version of InvisibleFerret, malware commonly used for long-term surveillance and credential theft.
GTIG reports that JADESNOW can pull additional payloads from either Ethereum or BNB Smart Chain, complicating forensic analysis. Once executed in memory, the malware can fetch further components designed to steal browser-stored passwords, cryptocurrency wallet data (MetaMask, Phantom), and credit card information.
Multi-Blockchain Tactics and Low-Cost Updates
“It’s unusual to see attackers using multiple blockchains for EtherHiding activity,” GTIG noted. “This may suggest operational separation among North Korean cyber units.”
Researchers observed the malicious smart contract being updated more than 20 times in its first four months — each update costing roughly $1.37 in gas fees. The frequent, inexpensive updates demonstrate how easily attackers can reconfigure operations while maintaining persistence.
Why It Matters
EtherHiding effectively turns the blockchain into a “bulletproof” hosting platform, leveraging its decentralization and transparency to mask malicious infrastructure. Traditional takedown methods — domain seizures or IP blacklists — are ineffective against this approach.
Once active, the malware awaits commands from a remote command-and-control (C2) server, capable of executing arbitrary commands or exfiltrating files. Exfiltrated data is sent either to external servers or Telegram channels.
“EtherHiding represents a shift toward a new generation of ‘bulletproof’ hosting,” Google’s analysts wrote. “It shows how attackers continue to adapt and weaponize emerging technologies to evade detection.”
Defensive Recommendations
GTIG warns that this campaign illustrates the increasing difficulty of monitoring malicious activity embedded in legitimate technologies. The group advises developers seeking employment to remain cautious during remote interviews — especially when asked to run code samples — and to test all files in isolated environments.


