North Korean Hacker's Device Infected by Lumma Stealer, Exposes $1.4 Billion Bybit Heist Infrastructure

Malware logs reveal tools, credentials, and operational security failures tied to major cryptocurrency theft.
A North Korean hacker linked to the $1.4 billion Bybit cryptocurrency heist became the victim of their own compromise. Researchers from Hudson Rock discovered that Lumma stealer malware had infected a device used in infrastructure supporting the massive February 2025 attack.
The infection exposed the attacker's tools, credentials, operational patterns, and security failures—providing cybersecurity researchers a rare window into how North Korean state-sponsored hackers conduct operations.
The Discovery
Hudson Rock analysts found the compromised device while analyzing Lumma stealer logs. Among the stolen credentials was the email address trevorgreer9312@gmail.com, which had previously appeared in reports by researchers from Silent Push.
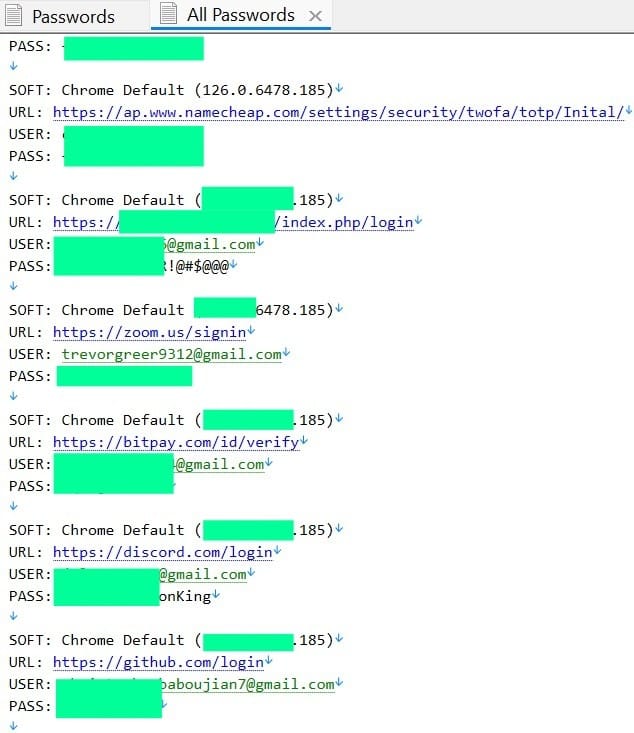
Cross-referencing this data with Silent Push findings led analysts to conclude the infected device was part of infrastructure tied to the Bybit exchange attack. The February 2025 hack has been attributed to North Korean hackers, presumably from the Lazarus group.
The email address was used to register bybit-assessment.com, a domain created just hours before the Bybit heist. The site impersonated the legitimate exchange and served as part of the phishing infrastructure.
Shared Infrastructure Model
The owner of the infected system likely wasn't directly involved in executing the cryptocurrency theft itself. However, researchers note that state-sponsored hackers frequently share resources across different operations, including:
- Development machines
- Phishing domains
- Credential sets
- Communication infrastructure
This shared resource model means a single compromised device can expose multiple operations and operatives.
The Development Workstation
The Lumma-infected device ran on an Intel Core i7 12th-generation processor with 16 GB of RAM. Installed software included Visual Studio Professional 2019 and Enigma Protector.
Enigma Protector is typically used to pack executable files to bypass security systems. The configuration suggests researchers discovered a well-equipped workstation for malware development and infrastructure management.
Operational Security Failures
Browser history and application data revealed multiple security lapses:
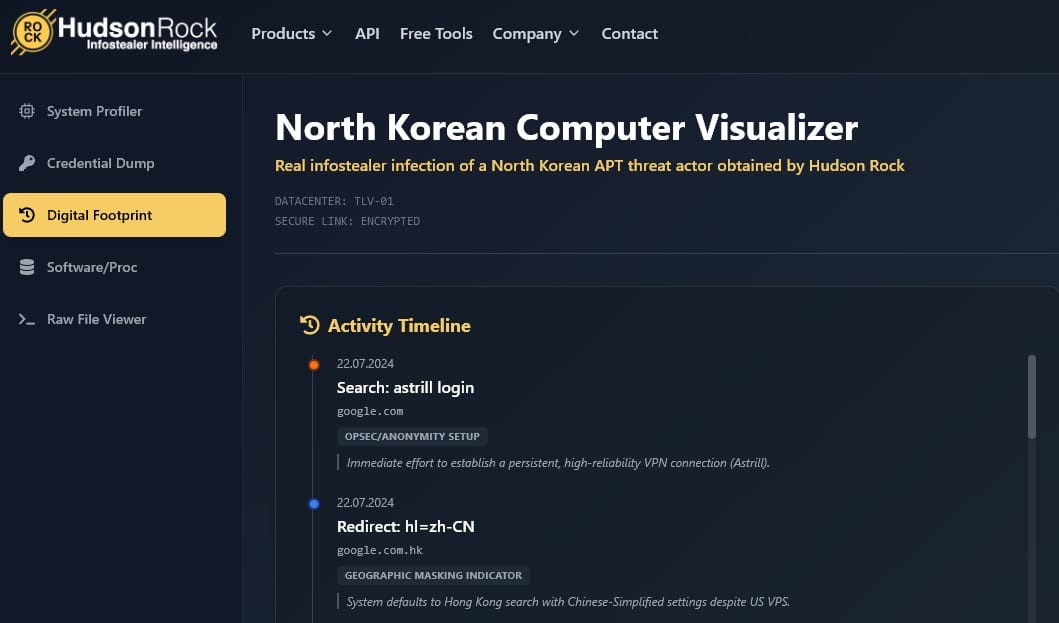
VPN Usage: Traffic was routed through a U.S. IP address via Astrill VPN. This matches patterns identified in other North Korean operations. In November 2025, cybersecurity researcher Mauro Eldritch reported that North Korean hackers posing as job applicants to Western IT companies also used Astrill VPN to mask their IP addresses.
Language Indicators: Browser settings used simplified Chinese, and translation history included direct queries in Korean—clear attribution indicators.
Data Exfiltration: The Dropbox folder structure suggested stolen data was uploaded there for later access, creating another forensic trail.
Preparing New Attacks
Evidence indicates the compromised hacker was preparing for additional phishing campaigns. Researchers found recently purchased domains including:
- callapp.us
- callservice.us
- zoom.callapp.us (subdomain)
These domains were designed to trick victims into downloading fake software or updates. The local IP address of a fake Zoom installer pointed back to the infected machine.
No Detection
Nothing in the logs suggests the hacker detected the compromise. This gave cybersecurity researchers an unprecedented opportunity to study North Korean hacking operations in real time.
Hudson Rock created a simulator of the infected machine, allowing other security specialists to examine the software, browser activity, and stolen data. The simulator provides a controlled environment for studying North Korean operational patterns without compromising ongoing investigations.
Not the First Breach
This isn't the first time a North Korean hacker's device has been compromised.
In June 2025, the legendary hacking publication Phrack (published since 1985) released an extensive investigation titled "APT Down: The North Korea Files." Hackers using the nicknames Saber and cyb0rg detailed their successful breach of a member of Kimsuky (also known as APT43 and Thallium), another North Korean state-sponsored hacking group.
That breach exposed similar operational details, tools, and infrastructure patterns.
What This Reveals
The Lumma stealer infection demonstrates critical lessons about advanced persistent threat operations:
Shared infrastructure creates cascading risk. When state-sponsored groups share development machines and credentials across operations, a single compromise can expose multiple campaigns.
Operational security lapses are common. Even sophisticated nation-state actors make basic mistakes: consistent VPN usage patterns, language settings that reveal origin, and predictable tool choices.
Malware doesn't discriminate. Criminal malware like Lumma stealer infects any vulnerable system, regardless of the victim's technical sophistication or sponsorship.
Attribution becomes easier with access. Direct access to an attacker's workstation provides definitive attribution evidence that external analysis struggles to match.
Intelligence Value
This compromise provides unprecedented intelligence value for defenders:
- Tool identification: Visual Studio configurations, Enigma Protector settings, and development patterns
- Infrastructure mapping: Domain registration patterns, hosting choices, and phishing page designs
- Operational patterns: VPN preferences, language settings, and workflow habits
- Attribution indicators: Korean language queries, Chinese browser settings, and known email addresses
Organizations can use these indicators to identify similar infrastructure in their own threat intelligence feeds and security monitoring.
The Irony
The situation carries obvious irony: a hacker group responsible for stealing $1.4 billion in cryptocurrency was itself compromised by commodity malware. The Lumma stealer—designed to harvest credentials from ordinary users—successfully infected a nation-state hacking operation's development infrastructure.
This demonstrates that even advanced threat actors face the same security challenges as everyone else. No amount of technical sophistication guarantees protection from basic malware threats.


