New Android Trojan Sturnus Steals Messages from Signal, WhatsApp, and Telegram

Specialists at ThreatFabric have discovered a new banking Trojan named Sturnus. The malware can intercept messages from end-to-end encrypted messengers (Signal, WhatsApp, Telegram) and gain full control over devices via VNC.
Technical Architecture
Researchers explain that Sturnus uses an advanced communication scheme with its command-and-control (C&C) servers: a combination of plaintext, RSA, and AES encryption. After installation, the malware connects to the command server, registers the victim, and creates two communication channels—an encrypted HTTPS channel for commands and data exfiltration, and an AES-encrypted WebSocket for real-time VNC operations.
Distribution Methods
Sturnus infection typically begins with the download of a malicious APK disguised as Google Chrome (com.klivkfbky.izaybebnx) or Preemix Box (com.uvxuthoq.noscjahae). The exact distribution method is not yet known, but researchers suggest that attackers use malicious advertising or private messages in messengers.
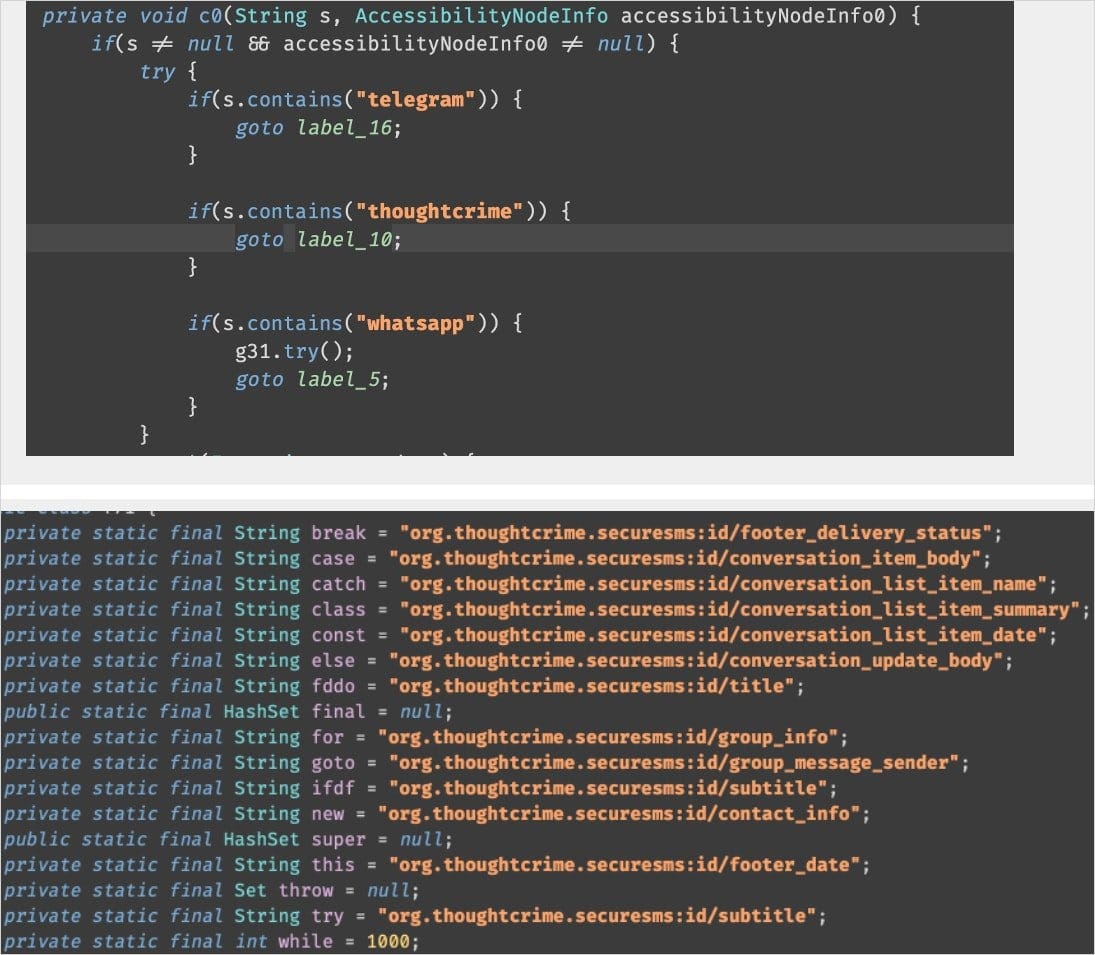
Message Interception Technique
The Trojan does not intercept messages during transmission, but rather after they have been decrypted. The malware reads the content directly from the screen of the infected device. To accomplish this, Sturnus abuses the Accessibility Service, gaining access to everything displayed on the screen: contacts, chats, incoming and outgoing messages.
"This completely bypasses end-to-end encryption by accessing the messages after they have been decrypted by the legitimate application, giving attackers direct access to supposedly private conversations," the researchers note.
Persistence and Control Mechanisms
In addition to reading messages, Sturnus requests administrator rights on Android, allowing it to monitor password changes, remotely lock the device, and evade removal. If the malware's admin rights are not manually revoked, uninstallation and removal via ADB will be blocked.
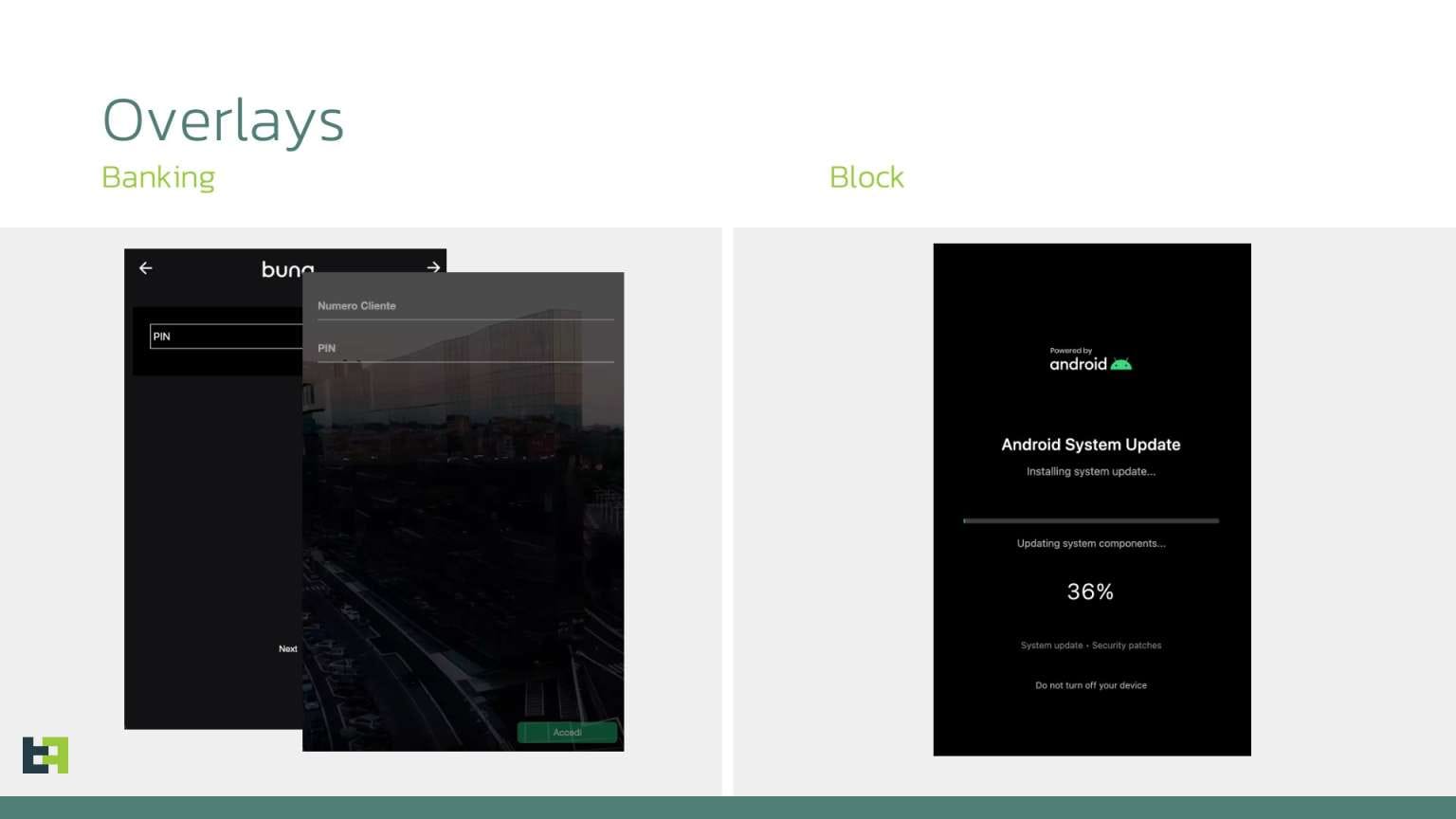
Using VNC, attackers can simulate taps, input text, scroll, and navigate. At the right moment, they can enable a black overlay and perform hidden actions: transfer money from banking apps, confirm dialogs, approve multi-factor authentication, change settings, or install additional applications.
Target Profile and Campaign Status
Sturnus is primarily focused on stealing funds from accounts at European financial institutions and uses regional overlay templates for this purpose. The banker is currently targeting users in Southern and Central Europe. As the scale of the attacks remains small, researchers believe the attackers are conducting testing ahead of larger campaigns.


