Microsoft Warns of Hack Group Stealing University Employee Payrolls

Microsoft has warned that the cybercrime group Storm-2657 has been targeting universities across the United States since March 2025, hijacking employee accounts and redirecting payroll funds to attacker-controlled bank accounts.
“Storm-2657 is actively attacking U.S. organizations—particularly employees in the higher education sector—to gain access to third-party HR platforms such as Workday,” the Microsoft Threat Intelligence team reported.
Researchers note that any SaaS platform managing HR data, payroll, or banking details could be vulnerable.
Payroll Pirates: Social Engineering, Not Software Exploits
The campaign—nicknamed Payroll Pirates—was previously documented by Silent Push, Malwarebytes, and Hunt.io.
Unlike typical cyberattacks, Storm-2657 does not exploit software vulnerabilities. Instead, it relies on sophisticated phishing and social engineering tactics to steal credentials and take advantage of accounts lacking multi-factor authentication (MFA).
Once access is gained, attackers modify payment details in HR systems, rerouting legitimate salaries to their own accounts.
Inside the Attack
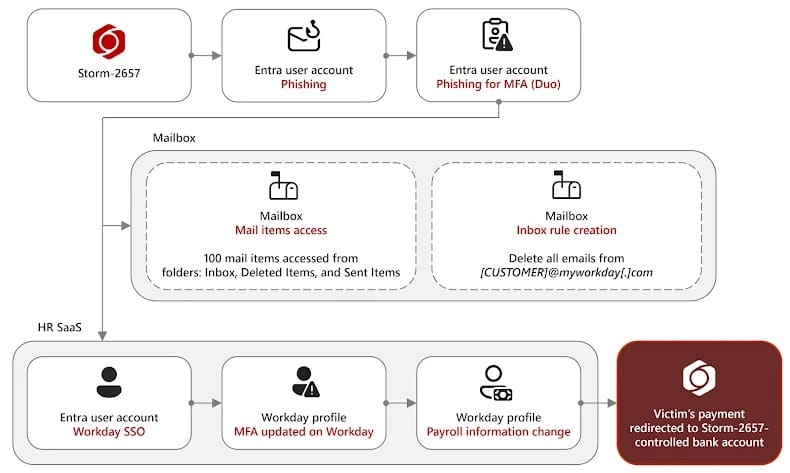
In one campaign observed in early 2025, Microsoft analysts found that the attackers gained initial access through phishing emails designed to harvest credentials and MFA codes.
Compromised Exchange Online accounts were then used to access victims’ Workday profiles via single sign-on (SSO).
To hide their activity, Storm-2657 created mailbox rules to delete warning messages from Workday, concealing unauthorized changes. They then updated payout settings, ensuring future paychecks were deposited into attacker-controlled accounts.
To maintain persistence, the group linked its own phone numbers to the compromised accounts for MFA verification. The hijacked mailboxes were subsequently used to launch new phishing campaigns targeting other employees and universities.
Widening Impact
Since March 2025, Microsoft has identified 11 successfully compromised accounts across three universities. Those accounts were then leveraged to send phishing messages to nearly 6,000 recipients at 25 other academic institutions.
The fraudulent emails often referenced employee illness or campus violation notices, exploiting urgency to trick victims into clicking malicious links.
Recommended Defenses
Microsoft recommends implementing phish-resistant, passwordless MFA methods such as FIDO2 security keys and Microsoft Authenticator number matching.
Administrators should also review accounts for signs of compromise, including:
- Unknown MFA devices or phone numbers
- Suspicious mailbox rules
- Unauthorized HR or payroll changes
The company’s analysts emphasize that social engineering remains a primary threat vector, even for institutions with strong technical defenses.
Takeaway
The Storm-2657 campaign serves as a reminder that the weakest link isn’t always the software—it’s the user’s trust.
As universities expand their digital ecosystems, attackers are finding ways to turn convenience into compromise. Microsoft’s message is clear: no amount of cloud automation replaces the need for human awareness and robust authentication.


