Microsoft Blocks File Previews to Stop Zero-Click Credential Theft
Windows 11 update disables preview pane for downloaded files after attackers exploit feature to steal authentication credentials
Microsoft has disabled File Explorer's preview feature for files downloaded from the internet, closing a security gap that allowed attackers to steal Windows credentials without victims ever opening a file.
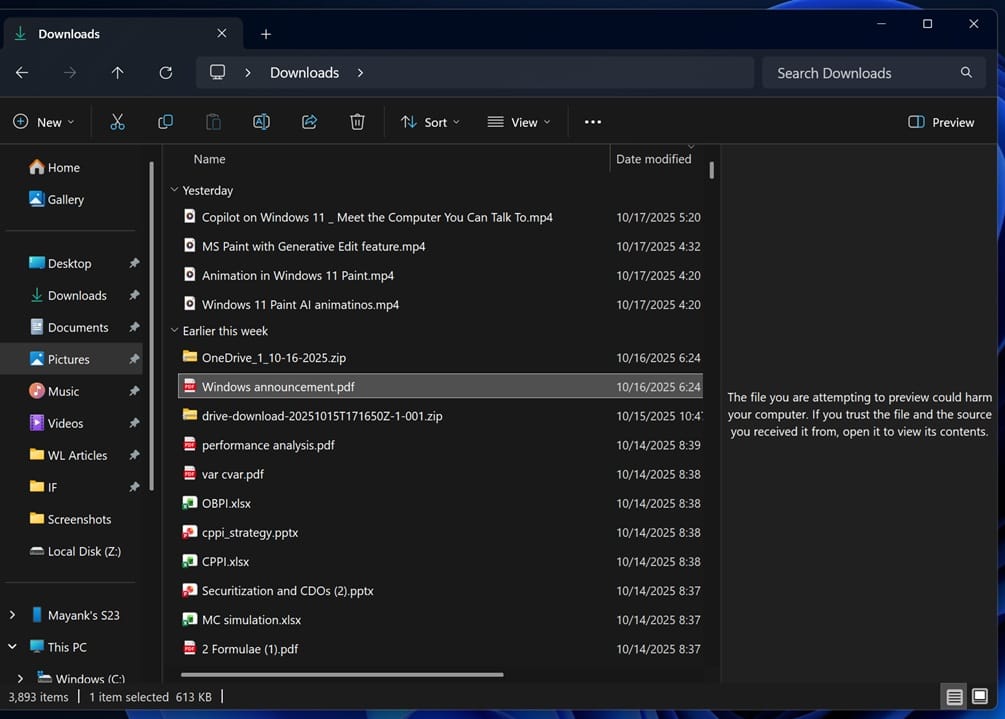
The change, deployed through October 2025 updates for Windows 11 and Windows Server, addresses a critical vulnerability where simply selecting a malicious file for preview could trigger automatic credential leakage.
The Zero-Click Threat
The attack exploits how Windows handles network authentication when previewing files. Malicious documents containing embedded HTML tags—such as <link> or <img src>—can reference external resources on attacker-controlled servers. When Windows attempts to render the preview, it automatically tries to authenticate to those external servers, inadvertently sending NTLM authentication hashes.
Attackers can then capture these hashes and use them to impersonate users or crack them offline to obtain plaintext passwords.
What makes this attack particularly dangerous is its minimal interaction requirement. Users don't need to open, execute, or even double-click the file—merely selecting it in File Explorer is enough to trigger credential theft.
"This attack vector requires almost no action from the user beyond selecting a file for preview," security researchers have noted, making it far more effective than traditional phishing or malware that requires victims to actively open malicious files.
How the Protection Works
Microsoft's fix automatically disables preview functionality for files meeting two criteria:
- Files from external network locations classified by Windows as the Internet zone
- Files with Mark of the Web (MotW) attributes indicating they were downloaded via browser, received as email attachments, or obtained from other external sources
When users attempt to preview such files, they now see a warning message: "The file you are trying to preview could harm your computer. If you trust the file and the source you got it from, open it to see the contents."
The protection is applied by default starting with updates released October 14, 2025, or later.
NTLM Hash Leakage Explained
NTLM (NT LAN Manager) hashes are cryptographic representations of Windows passwords used for network authentication. When Windows connects to network resources, it often sends these hashes to prove user identity.
The vulnerability exploited a Windows feature called "pass-the-hash," where the system automatically provides authentication credentials when accessing network resources—even those embedded in seemingly innocent file previews.
Attackers who capture these hashes can:
- Use them directly to authenticate as the victim (pass-the-hash attacks)
- Crack them offline using password-cracking tools
- Relay them to other services accepting NTLM authentication
This makes NTLM hash leakage a serious security concern, particularly in corporate environments where compromised credentials can lead to lateral movement across networks.
Workarounds for Trusted Files
Users who need to preview files from external sources have two options to bypass the restriction:
For individual files:
- Right-click the file in File Explorer
- Select "Properties"
- Click "Unblock" at the bottom of the "General" tab
- Apply the changes
For entire network shares:
- Open Control Panel and navigate to "Internet Options"
- Select the "Security" tab
- Choose "Trusted Sites"
- Add the network share address to the trusted zone
However, Microsoft recommends only unblocking files from genuinely trusted sources, as doing so removes the security protection.
Broader Context
This isn't the first time Microsoft has addressed NTLM-related vulnerabilities. The aging authentication protocol has long been a security concern, with Microsoft gradually moving toward more secure alternatives like Kerberos and modern authentication methods.
However, NTLM remains widely deployed for backward compatibility, making it a persistent target for attackers. Recent years have seen multiple attacks leveraging NTLM weaknesses:
- PetitPotam (2021): Forced Windows machines to authenticate to attacker-controlled servers
- PrintNightmare (2021): Combined with NTLM relay for privilege escalation
- Various phishing campaigns: Using malicious Office documents with external resource links
The File Explorer preview vulnerability represents another vector in this ongoing pattern, though its zero-click nature makes it particularly concerning.
What Users Should Know
The change primarily affects how users interact with downloaded files, particularly:
- Documents from email attachments that contain embedded links or external resources
- Files downloaded from websites that haven't been explicitly trusted
- Documents on network shares classified as external to the local network
Legitimate files may now require an extra step to preview, but this minor inconvenience significantly reduces the attack surface for credential theft.
For enterprise administrators, Microsoft recommends reviewing trusted sites configurations and educating users about the new behavior to avoid confusion when the preview pane displays security warnings.
The Takeaway
Microsoft's decision to disable previews for externally-sourced files reflects the growing sophistication of attacks that require minimal user interaction. As attackers find ways to weaponize legitimate Windows features, security measures must adapt—even when it means sacrificing some convenience.
For users, the message is clear: even passive actions like previewing files can have security implications. The new restriction serves as a reminder that in cybersecurity, sometimes the safest approach is to assume files are malicious until proven otherwise.
Organizations should view this change as an opportunity to review file handling procedures and ensure employees understand both the risks of NTLM hash leakage and the proper steps for safely handling files from external sources.


