Leaked Documents Show Which Pixel Phones Cellebrite Can Access

An insider operating under the name "rogueFed" has leaked screenshots from a confidential Cellebrite briefing intended for law enforcement agencies. These documents reveal which Google Pixel smartphone models can be compromised using the company's forensic tools. The leak also shows that GrapheneOS, a privacy-focused custom operating system, provides stronger protection than Google's standard Android implementation.
How the Leak Occurred
The publication 404 Media first reported on these leaked materials, which appeared on the GrapheneOS forums. The anonymous source, rogueFed, obtained access to closed Cellebrite briefings designed for law enforcement personnel. The screenshots they shared detail the capabilities and limitations of Cellebrite's tools when targeting specific Pixel models.
The documents cover Pixel 6, 7, 8, and 9 devices. The recently released Pixel 10 does not appear in these materials, likely because the briefing predates its launch.
Understanding Cellebrite's Business
Cellebrite, an Israeli company, markets itself as a mobile forensics specialist. The company develops tools that extract data from smartphones and other devices. Their customer base includes law enforcement agencies, intelligence services, and private security firms operating globally.
The company typically maintains strict secrecy about its tools' capabilities. This approach protects their methods from public scrutiny and prevents device manufacturers from patching the vulnerabilities their tools exploit. This leak breaks that secrecy, providing rare insight into what these forensic tools can actually accomplish.
The Three Device States Cellebrite Targets
The leaked documents categorize devices into three security states based on their encryption status:
BFU (Before First Unlock)
This state describes a phone that hasn't been unlocked since its last reboot. All data remains encrypted using keys that aren't accessible without the user's password or biometric authentication. Security researchers generally consider BFU the strongest protection state. When a phone sits in this condition, accessing its data requires breaking the encryption or exploiting system vulnerabilities.
AFU (After First Unlock)
After a user unlocks their device following a reboot, the phone enters AFU state. The system retains certain encryption keys in memory to maintain functionality without requiring constant re-authentication. This makes data extraction easier than in BFU state. Many security features remain active, but the device is more vulnerable than in BFU.
Unlocked
When a phone is actively unlocked—screen on, no lock screen displayed—data access becomes straightforward. The user has authenticated, so the system provides access to stored information. This represents the most vulnerable state.
Cellebrite's Capabilities on Stock Pixel Devices
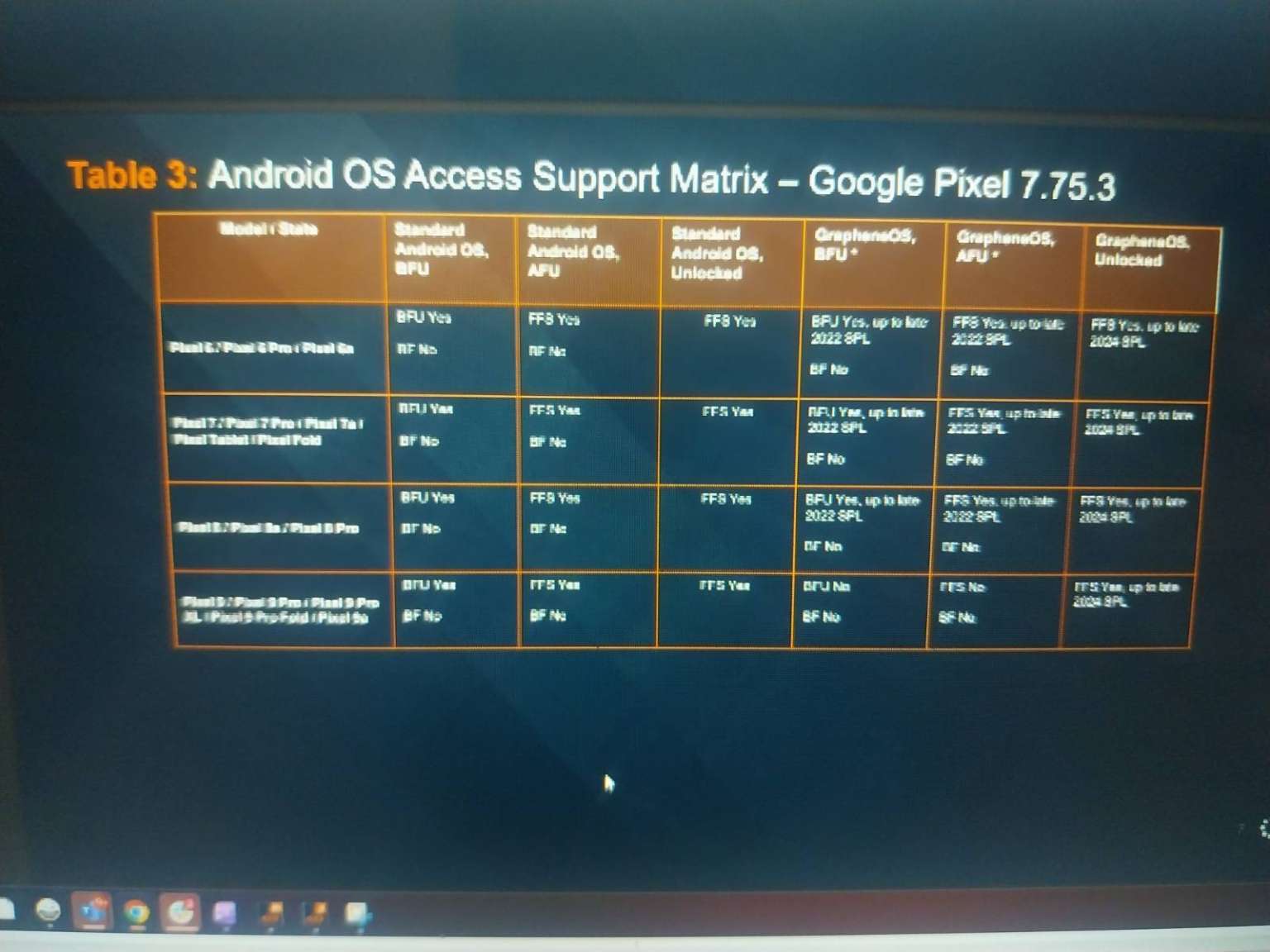
According to rogueFed's leaked materials, Cellebrite's tools can extract data from Pixel 6, 7, 8, and 9 devices running Google's standard firmware across all three states: BFU, AFU, and Unlocked.
This capability doesn't mean Cellebrite can brute-force passwords to unlock devices. The tools use different techniques—likely exploiting vulnerabilities in the operating system or bootloader—to access data without requiring the user's password. The exact methods remain undisclosed in the leaked materials.
One notable limitation: Law enforcement currently cannot copy eSIM data from Pixel devices using Cellebrite tools. This becomes increasingly relevant as Google transitions away from physical SIM cards. The Pixel 10 completely eliminated the physical SIM card slot, relying exclusively on eSIM technology.
GrapheneOS Changes the Security Picture
The situation shifts dramatically for devices running GrapheneOS instead of Google's standard Android. GrapheneOS is an AOSP-based (Android Open Source Project) custom firmware that prioritizes privacy and security above all other considerations.
Cellebrite informed law enforcement participants that their tools only work on devices running GrapheneOS versions older than late 2022. This date serves as a security threshold. Improvements made to GrapheneOS after that point apparently close the vulnerabilities Cellebrite's tools exploit.
This timing matters for newer Pixel models. The Pixel 8 launched in October 2023, and the Pixel 9 arrived in August 2024—both well after the late 2022 cutoff. Any Pixel 8 or 9 running a current GrapheneOS version in BFU or AFU state is protected from Cellebrite's extraction tools.
Recent GrapheneOS Improvements
The leak revealed another significant development. Since late 2024, even fully unlocked devices running GrapheneOS cannot have their data extracted using Cellebrite's tools. Access is limited to whatever the user themselves can see on screen—no deeper data extraction is possible.
This represents a substantial achievement in mobile security. Traditionally, unlocked devices offer forensic tools their easiest access point. If GrapheneOS can protect data even in this vulnerable state, it demonstrates security measures that exceed what most mobile operating systems provide.
What GrapheneOS Actually Does
GrapheneOS (previously called CopperheadOS) builds on the Android Open Source Project foundation but implements aggressive privacy and security enhancements. The system supports specific phone models, with Pixel devices being the primary target hardware.
The operating system ships without Google services—no Google Play Services, no Google Play Store, no built-in Google apps. This absence eliminates a significant tracking vector. Users who want these services can install them in sandboxed profiles with limited permissions, but the default configuration excludes them entirely.
The system attracts users who prioritize privacy. Journalists working in hostile environments, activists concerned about surveillance, security professionals, and privacy advocates make up much of the user base. The system's security hardening goes beyond what typical users need, but for those facing sophisticated threats, GrapheneOS provides meaningful protection.
My Analysis of These Findings
In my opinion, this leak provides valuable data for understanding the mobile forensics industry. Cellebrite operates largely in secrecy, sharing details only with law enforcement and government clients. This confidentiality prevents public accountability and makes it difficult to assess whether these tools are used appropriately.
Per the leaked documents, the security gap between stock Android and GrapheneOS is substantial. Google implements reasonable security measures in stock Pixel firmware, but those measures don't prevent Cellebrite's tools from accessing data. GrapheneOS, through its additional hardening, closes vulnerabilities that commercial forensic tools exploit.
The Arms Race Between Forensics and Security
This leak illustrates the ongoing competition between device security and forensic capabilities. When security researchers or privacy-focused operating systems close vulnerabilities, forensic tool companies search for new ones. When forensic companies develop new exploitation techniques, security researchers work to defend against them.
Cellebrite will likely update its tools to address GrapheneOS's protections. The company employs skilled security researchers who search for new vulnerabilities. However, GrapheneOS developers also continue improving their system. This creates a cycle where neither side achieves permanent advantage.
Practical Implications for Different Users
Law Enforcement and Legal Issues
This leak raises questions about the tools available to law enforcement. In legitimate criminal investigations, accessing suspects' devices can provide critical evidence. Forensic tools serve a valid purpose in these scenarios.
However, these same tools can be misused. Authoritarian governments purchase Cellebrite's products. Agencies in countries with poor human rights records can use these tools to access activists' devices, journalists' sources, or dissidents' communications. The technology itself is neutral, but its applications vary widely.
Privacy-Conscious Users
For individuals concerned about device security—whether because they handle sensitive information, work in journalism, or simply value privacy—GrapheneOS offers demonstrated protection against commercial forensic tools. The leaked documents provide rare confirmation of this protection's effectiveness.
Installing GrapheneOS requires technical knowledge and comes with trade-offs. Users lose convenient Google service integration. Some banking apps and other security-focused applications refuse to run on custom operating systems. The user experience differs from standard Android in ways that can be frustrating.
However, for users whose threat model includes sophisticated adversaries with access to commercial forensic tools, these trade-offs may be acceptable.
Device Manufacturers
This leak puts pressure on Google and other Android device manufacturers. If a third-party custom operating system provides stronger security than the manufacturer's default firmware, questions arise about the manufacturer's security priorities.
Google has made significant security investments in recent years. Features like Titan M security chips, verified boot, and regular security updates demonstrate commitment to protecting users. But the Cellebrite tools' capabilities suggest room for improvement.
The Source and Future Vetting
RogueFed's leak included interesting operational details. According to their statements, they joined two separate closed Cellebrite briefings without being identified as an unauthorized participant. This security failure on Cellebrite's part allowed the leak to occur.
In one screenshot, rogueFed revealed the name of the meeting organizer. This disclosure will likely help Cellebrite identify how the breach occurred. Journalists covering this story suggest Cellebrite will strengthen vetting procedures for future online briefings.
The source's motivations remain unclear. They might be a law enforcement insider concerned about these tools' capabilities. They could be a security researcher who gained access to expose forensic industry practices. Or they might have other reasons for the disclosure.
Broader Context: Mobile Forensics Industry
Cellebrite isn't alone in the mobile forensics market. Companies like Grayshift (makers of GrayKey), MSAB, and others develop similar tools. Each company guards its methods closely, creating an industry that operates with minimal public accountability.
These tools regularly appear in court cases, but details about their functionality rarely become public. Defense attorneys often cannot examine the tools' reliability or accuracy because companies claim trade secret protection. This dynamic creates challenges for defendants and raises questions about due process.
Leaks like rogueFed's provide rare windows into this secretive industry. Previous leaks have revealed:
- Which iOS versions different tools can access
- Pricing structures for law enforcement purchases
- Success rates for different device models and security states
- Vulnerabilities being actively exploited
Each leak helps security researchers understand the threat landscape and develop better protections.
Recommendations for Users Concerned About Forensic Tools
Basic Security Practices
Even if you're not ready to switch to GrapheneOS, several steps improve your device's resistance to forensic tools:
- Restart your device regularly: This puts the phone back into BFU state, which provides the strongest protection. Make restarting a daily habit.
- Use strong passwords: Biometrics like fingerprints and face recognition are convenient, but a strong alphanumeric password provides better security. Use at least 12 characters mixing letters, numbers, and symbols.
- Enable automatic lockdown: Many Android devices offer a "lockdown mode" that temporarily disables biometric authentication and requires password entry. Learn how to trigger this quickly if needed.
- Keep software updated: Security patches address vulnerabilities that forensic tools exploit. Install updates as soon as they become available.
- Enable full-disk encryption: Modern Android devices encrypt data by default, but verify this setting is enabled.
For High-Risk Users
If your threat model includes sophisticated adversaries with access to commercial forensic tools, consider:
- GrapheneOS installation: Despite the learning curve and compatibility issues, it provides demonstrated protection against current forensic tools.
- Compartmentalization: Use separate devices for different purposes. Keep sensitive communications on a hardened device that doesn't contain other personal data.
- Minimal data retention: Don't store information on your phone that you don't need. Delete old messages, clear browsing history, and remove unnecessary files regularly.
- Encrypted messaging: Use Signal or other end-to-end encrypted messaging apps. Enable disappearing messages for sensitive conversations.
- Regular security reviews: Periodically audit your device for unexpected apps, unusual permissions, or suspicious behavior.
The Takeaway
This leak confirms what security researchers have long suspected: commercial forensic tools can access data from most consumer devices, but privacy-focused operating systems like GrapheneOS provide meaningful additional protection.
The forensics industry will continue developing new capabilities. Device manufacturers and security-focused projects will continue improving protections. Users caught between these forces should understand the risks their devices face and make informed decisions about their security posture.
For most people, standard device security—strong passwords, regular updates, encrypted messaging—provides adequate protection. For those facing sophisticated threats, custom operating systems like GrapheneOS offer demonstrated advantages against commercial forensic tools. This leak provides rare confirmation of that protection's real-world effectiveness.


