Large Botnet Targets RDP Services Across the U.S.

GreyNoise analysts have identified a large-scale botnet attacking Remote Desktop Protocol (RDP) services across the United States, leveraging more than 100,000 IP addresses. According to the firm, the campaign began on October 8, 2025 and continues to expand globally.
Global Footprint
The campaign was first detected following an unusual spike in traffic originating from Brazil, later mirrored by similar activity from Argentina, Iran, China, Mexico, Russia, South Africa, and Ecuador.
In total, compromised devices from over 100 countries appear to be participating in the botnet’s infrastructure.
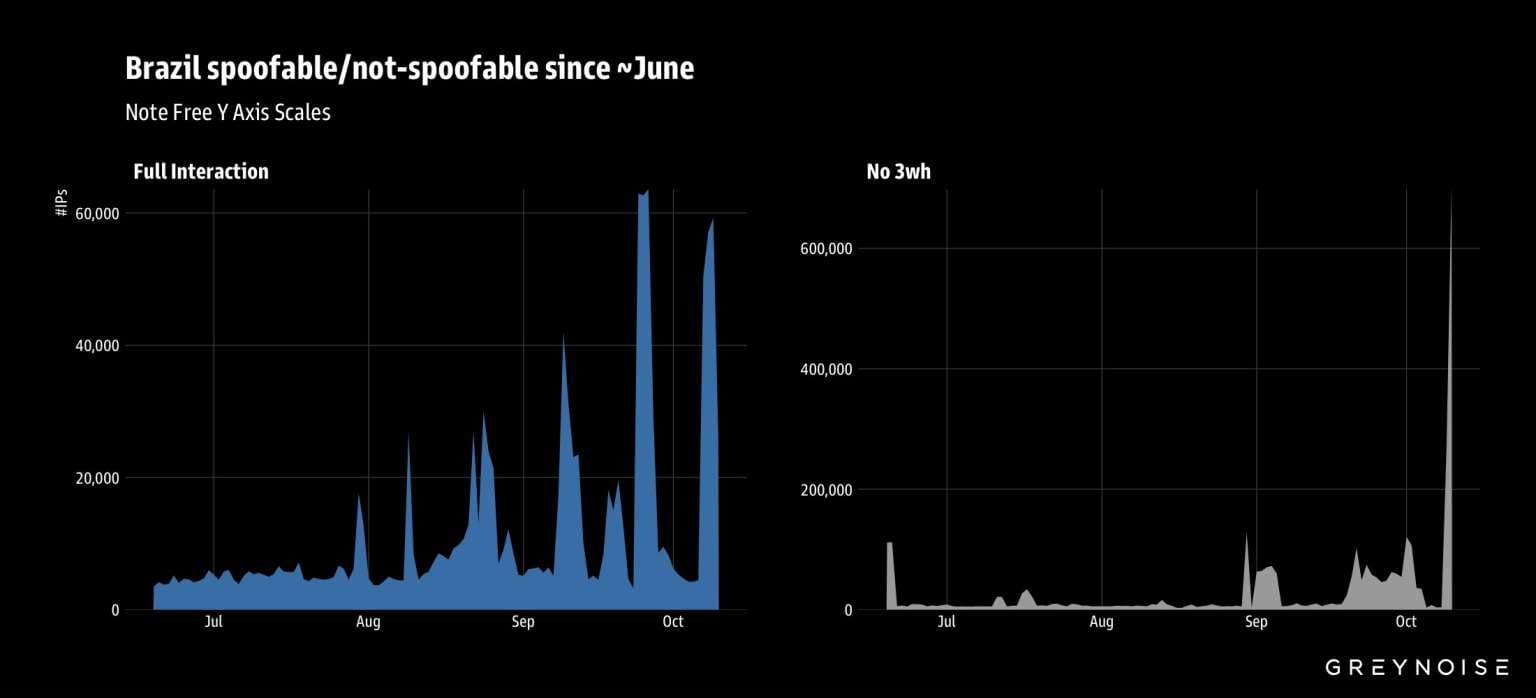
Two Attack Methods
Researchers report that the botnet uses two distinct attack techniques:
- Timing attacks on RD Web Access – scanning RD Web Access endpoints and measuring response-time differences during anonymous authentication attempts to identify valid usernames.
- Credential brute-forcing via the RDP web client – interacting with the RDP Web Client login process and enumerating accounts based on server behavior and response variations.
Coordinated and Centralized
Nearly all of the botnet’s IP addresses share a common TCP signature, with minor MSS (Maximum Segment Size) differences across clusters — indicators of centralized management.
The timing, scale, and uniformity of activity suggest a well-orchestrated campaign rather than random opportunistic probing.
Defensive Recommendations
GreyNoise recommends that system administrators block known malicious IPs, enable multi-factor authentication (MFA) for all remote access points, and monitor network logs for unusual RDP scanning patterns or unauthorized login attempts.
Given the campaign’s size and distributed nature, security teams should remain alert for coordinated RDP brute-force or enumeration activity even outside of known attack windows.
Summary
The emergence of a 100,000-node RDP botnet highlights how remote-access services remain a prime target for global attackers. Despite years of guidance, improperly secured RDP endpoints continue to provide easy entry points for credential theft, network compromise, and ransomware deployment.


