Konni Group Weaponizes Google Find Hub to Remotely Wipe Android Devices

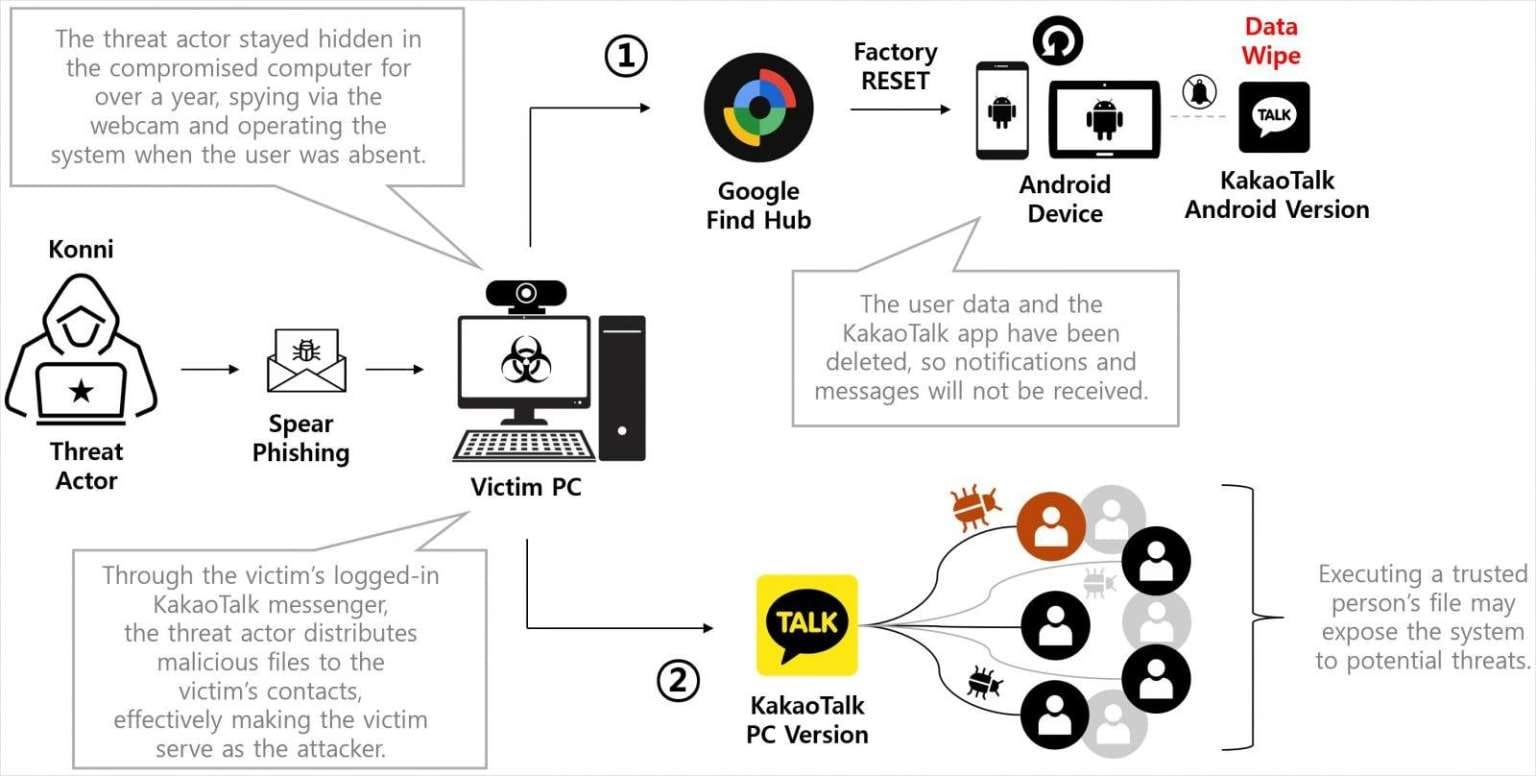
The North Korean hacking group Konni is exploiting Google Find Hub (formerly Find My Device) to track victims' GPS locations and remotely factory reset their Android devices—a destructive tactic marking a shift from the group's typical data theft operations.
Attack Campaign Targets South Korean Users
Cybersecurity firm Genians reports that these attacks target South Korean users through KakaoTalk, a popular local messaging platform. The attackers first infect victims' computers with remote access trojans (RATs), then leverage stolen credentials and Google's legitimate device management tool to destroy data on linked Android devices.
Researchers note that this Konni activity cluster shares targets and infrastructure with known North Korean threat groups Kimsuky (Emerald Sleet) and APT37 (ScarCruft). These groups typically target educational institutions, government agencies, and cryptocurrency companies. While Konni historically focused on data theft through RATs, this campaign demonstrates a clear shift toward destructive attacks.
Multi-Stage Infection Process
The attacks begin with phishing messages on KakaoTalk. Threat actors impersonate South Korea's National Tax Service, police departments, or other government agencies, sending victims malicious attachments—either signed MSI installers or ZIP archives.
When executed, the file runs two scripts: install.bat and error.vbs. The second script displays a fake error message about language pack issues to distract the victim. Meanwhile, the BAT file launches an AutoIT script that establishes system persistence through a scheduled task and connects to a command-and-control server.
The malware then downloads additional modules: RemcosRAT, QuasarRAT, and RftRAT. These tools steal credentials from Google and Naver (a popular South Korean search engine with email services), access victim accounts, modify security settings, and delete logs indicating compromise.
Exploiting Google Find Hub for Destruction
After gaining access to victims' Google accounts, the attackers activate Google Find Hub—Android's built-in tool for locating lost or stolen devices. This legitimate feature allows users to remotely track device location, lock devices, or completely erase all data.
Konni abuses the factory reset function specifically. The group monitors victims' GPS coordinates and triggers the wipe when targets are away from home and unable to respond quickly. In one documented attack, threat actors triggered remote factory resets three times on all of a victim's registered Android devices, completely destroying important data and rendering the devices unusable for an extended period.
Targeted Attack on Vulnerable Population
Genians documented a specific incident on September 5, 2025, where Konni compromised the account of a South Korean counselor who provides psychological support to North Korean defectors. Using his KakaoTalk account, attackers sent a malicious file disguised as a "stress relief program" to a defector student.
After infecting the computer and resetting the smartphone to factory settings, the attackers maintained access to the KakaoTalk PC session on the compromised computer and distributed malware to the victim's contacts.
Strategic Objectives Behind Data Destruction
Researchers believe the smartphone data deletion serves multiple strategic purposes:
- Communication isolation – Cutting victims off from their networks
- Attack concealment – Hiding traces of compromise
- Response delay – Preventing quick recovery efforts
- Security bypass – Disabling defense mechanism alerts
When victims lose access to mobile devices, they don't receive push notifications about suspicious account activity, giving attackers more time to operate undetected.
Google's Response and Security Recommendations
A Google representative clarified that these attacks did not exploit vulnerabilities in Android or Find Hub. Successful compromise required prior PC infection with malware that stole Google account credentials.
The company strongly recommends users enable two-factor authentication or use passkeys to protect accounts from credential theft.
Key Takeaway
This campaign demonstrates how threat actors can weaponize legitimate security tools for destructive purposes once they gain initial access. The shift from data theft to data destruction suggests Konni may be expanding its operational objectives beyond traditional espionage. South Korean users, particularly those working with sensitive populations like North Korean defectors, face heightened risk from these targeted attacks.


