"Jingle Thief" Hackers Steal Millions Through Gift Card Fraud Scheme

Moroccan cybercrime group infiltrates retailers' cloud systems to mass-issue unauthorized gift cards, maintaining hidden access for over a year
A sophisticated hacking operation is targeting retail and consumer service companies worldwide, exploiting cloud infrastructure vulnerabilities to generate and steal gift cards worth potentially millions of dollars.
The group, dubbed "Jingle Thief" by Palo Alto Networks researchers, has perfected a fraud scheme that combines long-term network infiltration with intimate knowledge of victims' gift card systems—allowing them to issue unauthorized cards that are nearly impossible to trace back to the attackers.
The name reflects the group's operational pattern: attacks intensify during holiday shopping seasons when gift card usage surges and fraudulent transactions can more easily blend into legitimate activity.
The Perfect Crime: Why Gift Cards?
Gift cards represent an ideal target for cybercriminals seeking to monetize network access. Unlike traditional financial fraud, gift cards offer several advantages:
- Easy monetization: Cards can be quickly sold on gray markets or used directly for purchases
- Minimal personal data required: Most retailers allow gift card redemption with limited identity verification
- Difficult to trace: Gift card transactions are harder to track than credit card fraud
- High volume during holidays: Fraudulent issuances blend into legitimate seasonal spikes
This combination makes gift card fraud particularly attractive—and particularly damaging to victim companies that may not detect the theft until long after cards have been used.
Morocco-Based Operation with Year-Long Persistence
Palo Alto Networks tracks the group as CL-CRI-1032 and links it with moderate confidence to Atlas Lion and Storm-0539, hacker groups operating from Morocco since 2021. What sets Jingle Thief apart is their extraordinary patience and operational security.
"Jingle Thief can maintain its position within compromised organizations for months, sometimes retaining access to the victim company's network for over a year," researchers noted.
In one documented case during April-May 2025, attackers maintained network access for approximately 10 months and compromised 60 employee accounts before detection. During this extended dwell time, the hackers conducted extensive reconnaissance, moved laterally through cloud infrastructure, and successfully evaded security monitoring.
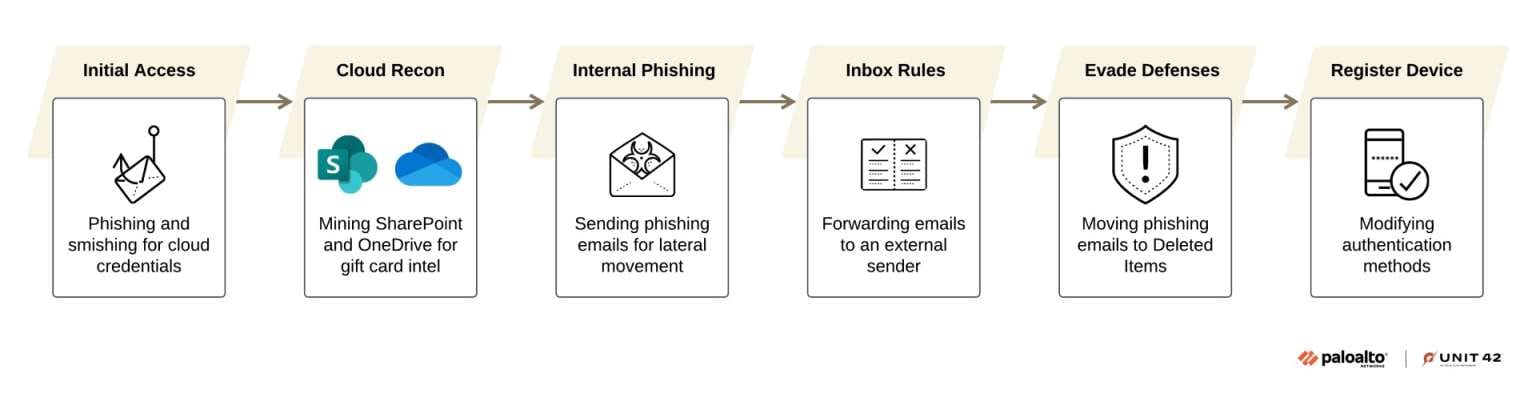
Attack Chain: From Phishing to Privilege Escalation
Jingle Thief operations follow a methodical multi-stage approach:
Initial Access: Attackers begin with targeted reconnaissance of potential victims, then launch phishing and smishing (SMS phishing) campaigns to steal Microsoft 365 credentials from employees. The campaigns are highly targeted, focusing on individuals likely to have access to relevant systems.
Intelligence Gathering: Once inside, attackers thoroughly study the victim's SharePoint and OneDrive repositories, searching for:
- Gift card issuance and tracking procedures
- Business operations documentation
- Financial process workflows
- VPN configurations
- IT access guides and system documentation
This intelligence phase is critical—understanding internal processes allows attackers to issue fraudulent gift cards that appear legitimate within company systems.
Lateral Movement: Armed with operational knowledge, Jingle Thief sends additional phishing emails internally, impersonating IT department communications to expand their access. They create email forwarding rules to automatically exfiltrate correspondence from compromised accounts, then cover their tracks by moving sent messages to deleted folders.
Persistence Mechanisms: To maintain access even after security responses, the group employs sophisticated techniques:
- Registering fake authenticator applications to bypass multi-factor authentication
- Enrolling attacker-controlled devices in Microsoft Entra ID (formerly Azure AD)
- Establishing multiple access pathways that survive password resets and session token revocations
Cloud-Native Techniques Evade Detection
A defining characteristic of Jingle Thief operations is their exclusive focus on abusing legitimate cloud services and identity systems rather than deploying custom malware.
"Gift card fraud combines stealth, speed, and scalability, especially when accessing cloud environments," researchers explained. "To exploit these systems, attackers need access to internal documentation, which they obtain by stealing credentials and maintaining a hidden presence in Microsoft 365 environments."
This "living off the land" approach makes detection significantly more difficult. Security tools designed to identify malicious software struggle to distinguish attacker activity from legitimate employee actions when both use the same cloud platforms and authentication systems.
Coordinated Campaign Targets International Companies
During April-May 2025, Palo Alto Networks observed a wave of coordinated attacks against multiple unnamed international companies. The timing suggests either a deliberate campaign to maximize returns during spring retail activity or an escalation following successful reconnaissance of multiple targets.
The researchers declined to name specific victims, but noted that targeted companies span retail and consumer services sectors where gift card programs are common revenue drivers and customer loyalty tools.
Financial Impact Remains Unclear
While Palo Alto Networks hasn't disclosed the monetary value of stolen gift cards, the scale and sophistication of Jingle Thief operations suggest substantial losses. With access maintained for months and dozens of accounts compromised in single incidents, attackers could potentially generate thousands of fraudulent gift cards before detection.
For retailers operating on thin margins, such fraud can significantly impact profitability—especially during critical holiday periods when legitimate gift card sales represent major revenue streams.
Detection and Prevention Challenges
The cloud-native nature of these attacks creates significant detection challenges for traditional security tools. Organizations must shift from malware-focused defenses to monitoring for anomalous identity and access patterns:
Warning signs include:
- Unusual access to gift card management systems, especially from unexpected locations
- Employee accounts accessing SharePoint/OneDrive documents outside normal patterns
- Creation of email forwarding rules, particularly to external domains
- Registration of new authenticator apps or device enrollments without legitimate requests
- Access to gift card documentation by accounts not associated with relevant business functions
Protecting Against Gift Card Fraud
Security experts recommend multi-layered defenses:
Identity Security:
- Implement phishing-resistant MFA using hardware tokens or passkeys
- Monitor for suspicious device enrollments in Entra ID
- Alert on unusual authenticator app registrations
- Regularly audit email forwarding rules across the organization
Access Controls:
- Limit gift card system access to essential personnel only
- Implement privileged access management for high-value systems
- Require additional verification for gift card issuance activities
- Segment networks to prevent lateral movement from initial compromises
Monitoring and Detection:
- Establish baseline behaviors for accounts with gift card access
- Alert on after-hours or holiday access to sensitive systems
- Monitor for bulk gift card generation patterns
- Track access to documentation about gift card processes
Vendor Relationships:
- Work with gift card processors to implement fraud detection
- Establish alert mechanisms for unusual issuance patterns
- Develop procedures for rapid card deactivation upon suspected compromise
Broader Implications
The Jingle Thief campaign highlights an evolving threat landscape where attackers increasingly target business logic and legitimate processes rather than exploiting technical vulnerabilities. As organizations migrate to cloud platforms, traditional perimeter defenses become less effective against adversaries who compromise identities and abuse authorized access.
The connection to previously identified Moroccan hacking groups suggests a mature and ongoing operation with refined techniques developed over years of activity. The group's ability to maintain access for a year demonstrates serious gaps in many organizations' security monitoring and incident response capabilities.
The Bottom Line
Gift card fraud may lack the dramatic impact of ransomware or data breaches, but it represents a financially motivated threat that's harder to detect and prevent. Jingle Thief's success stems from patience, thorough reconnaissance, and deep understanding of victim business processes—qualities that make them formidable adversaries.
For retailers and consumer service companies issuing gift cards, the message is clear: these programs aren't just customer convenience features—they're high-value assets requiring the same security scrutiny as financial systems. The attackers already understand this; defenders must catch up.
Organizations should audit their gift card programs now, before holiday seasons when Jingle Thief becomes most active. The cost of implementing proper controls is far less than the financial and reputational damage of discovering months later that attackers have been printing money from inside your systems.


