Hackers Target Transportation Companies for Physical Cargo Theft

Security researchers at Proofpoint have uncovered a large-scale campaign where cybercriminals breach transportation companies and logistics operators to steal physical cargo. These attacks are causing multi-million dollar losses and significant supply chain disruptions across multiple countries.
Attack Methodology
The campaign begins with compromised accounts on freight load boards—specialized online marketplaces where shipping companies post cargo transportation requests. After gaining access to legitimate accounts, attackers create fraudulent shipment listings and wait for carriers to respond.
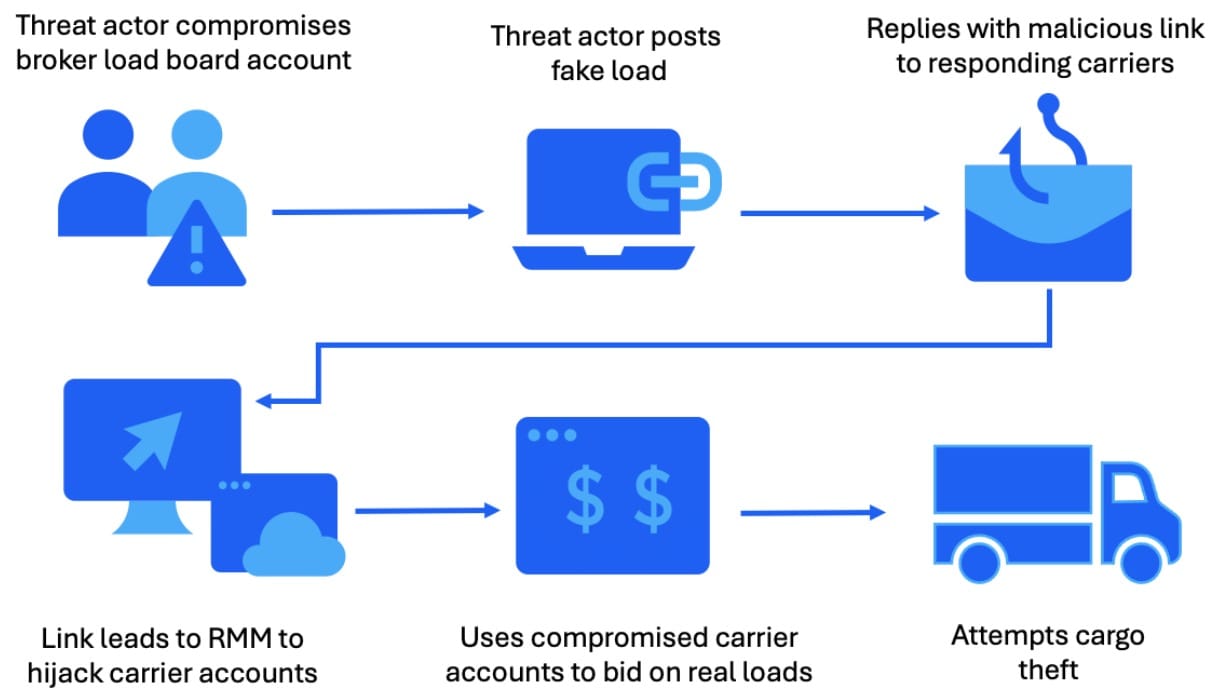
When a carrier expresses interest, the attackers send response emails containing malicious links. These links trigger downloads of legitimate remote access software, including tools commonly used for system administration:
- Fleetdeck
- LogMeIn Resolve
- N-able
- PDQ Connect
- ScreenConnect
- SimpleHelp
The attackers employ an opportunistic approach, targeting any carrier that responds to their fake listings regardless of company size. In my opinion, this indiscriminate targeting makes the campaign particularly dangerous small and medium-sized carriers often lack robust security programs, making them easier targets for initial compromise.
Infection Vectors
Proofpoint researchers have identified three primary attack vectors:
- Malicious responses to fake listings: Carriers responding to fraudulent shipment postings receive emails with malicious links
- Thread hijacking: Attackers compromise legitimate email accounts and insert malicious links into existing business correspondence
- Direct email campaigns: Targeted messages sent directly to carriers, brokers, and logistics service providers
Over recent months, researchers have documented nearly two dozen distinct campaigns using these techniques.
Post-Compromise Activities
After achieving initial access through remote access tools, the attackers follow a structured progression:
Phase 1: Reconnaissance The attackers map the victim's network, identify key systems, and locate credentials stored in browsers and applications.
Phase 2: Credential Theft Attackers deploy credential-stealing tools such as WebBrowserPassView to harvest stored passwords. This allows them to expand access beyond the initial compromise point and move laterally within the target environment.
Phase 3: System Control With expanded access, attackers gain control of critical logistics systems, including scheduling platforms, dispatch software, and shipment tracking tools.
Phase 4: Cargo Diversion The attackers book shipments using the compromised carrier's credentials and manipulate dispatch systems to redirect valuable cargo to accomplices. The stolen goods are subsequently sold through online marketplaces or smuggled internationally.
Scale and Impact
Per Proofpoint's analysis, cargo theft represents a serious global problem with annual losses exceeding $30 billion USD. The activity is primarily conducted by organized criminal groups operating in multiple countries, with thefts most frequently occurring in:
- Brazil
- Chile
- Germany
- India
- Mexico
- South Africa
- United States
Proofpoint assesses with high confidence that these cybercriminals operate within organized criminal groups rather than as independent actors. The stolen cargo varies widely in type and value—from energy drinks to consumer electronics—indicating the attackers target shipments based on opportunity rather than specific goods.
"Such crimes can lead to massive supply chain disruptions and cost companies millions," Proofpoint researchers state in their report.
Timeline and Infrastructure
Proofpoint first detected these attacks in June 2025, but the associated infrastructure has been operational since at least January 2025. This six-month operational history suggests a well-established campaign with sustained resources and planning.
Based on the attackers' techniques and targeting precision, researchers believe the threat actors possess deep knowledge of logistics industry software, services, and internal processes. This specialized knowledge allows them to navigate complex transportation management systems and identify high-value shipment opportunities.
Related Activity Cluster
Proofpoint has identified a separate but potentially related cluster of attacks that operated from 2024 through March 2025. This earlier campaign targeted organizations in the ground transportation sector using different tools:
- DanaBot (infostealer)
- Lumma Stealer (infostealer)
- NetSupport (remote access tool)
- StealC (infostealer)
While the connection between these campaigns remains unconfirmed, the operational overlap and targeting similarities suggest potential coordination or shared tactics among threat actor groups.
Technical Analysis
The attackers' tool selection reveals strategic thinking about detection avoidance. Remote Monitoring and Management (RMM) tools provide several advantages over traditional malware:
Legitimacy: RMM tools are legitimate software used by IT departments for system administration, making them less likely to trigger security alerts
Functionality: These tools provide comprehensive remote access capabilities without requiring custom malware development
Persistence: RMM software often runs continuously and automatically restarts after system reboots
Detection evasion: Security products typically whitelist legitimate RMM tools, allowing attackers to operate undetected for extended periods
Proofpoint researchers note: "Regardless of the final payload, stealers and RMM tools serve one common purpose: remote access to a system for information theft. However, the use of RMM tools allows the attackers to remain undetected for longer."
In my experience covering supply chain attacks, this combination of social engineering (fake shipment listings) with legitimate remote access tools represents a sophisticated approach that blends traditional fraud with modern cyber techniques.
Industry Vulnerabilities
The logistics and transportation sector faces several security challenges that make these attacks effective:
Operational pressure: Transportation companies operate on tight schedules with minimal delays tolerated. This pressure can lead personnel to skip security verification steps when responding to shipment opportunities.
Distributed operations: Carriers often have drivers, dispatchers, and administrative staff working remotely or from multiple locations, creating a larger attack surface.
Legacy systems: Many logistics companies rely on older transportation management systems that lack modern security controls.
Trust-based relationships: The industry operates on established business relationships and trust, making social engineering attacks more effective.
Limited security resources: Smaller carriers often lack dedicated cybersecurity personnel or robust security programs.
Mitigation Recommendations
Transportation companies and logistics operators should implement several defensive measures:
Email Security
- Deploy email filtering solutions that scan links and attachments before delivery
- Implement Domain-based Message Authentication, Reporting, and Conformance (DMARC) to prevent email spoofing
- Train employees to recognize suspicious emails, especially those containing unexpected links or attachments
Access Controls
- Require multi-factor authentication (MFA) for all freight load board accounts and critical business systems
- Implement principle of least privilege—grant users only the access they need for their specific roles
- Regularly audit account permissions and remove unnecessary access
Network Security
- Monitor for unauthorized RMM tool installations
- Implement application whitelisting to prevent unauthorized software execution
- Deploy endpoint detection and response (EDR) solutions that can identify suspicious remote access tool behavior
Operational Security
- Verify new shipment requests through additional communication channels before responding
- Establish verification procedures for unusual shipment changes or route modifications
- Monitor dispatch systems for unauthorized schedule changes
Credential Management
- Prohibit storing credentials in web browsers on systems used for business operations
- Deploy password managers with strong master passwords and MFA
- Rotate credentials regularly, especially after suspicious activity
Incident Response
- Develop and test incident response procedures specific to cargo diversion scenarios
- Establish communication channels with law enforcement agencies that handle cargo theft
- Create rapid response protocols for suspicious shipment modifications
Industry Cooperation
This campaign demonstrates the need for increased information sharing within the transportation and logistics sector. Freight load board operators should implement enhanced verification procedures for new listings and suspicious account activity. Furthermore, industry associations should establish threat intelligence sharing mechanisms to rapidly disseminate indicators of compromise (IOCs) and attacker tactics.
Looking Forward
The logistics industry's digital transformation has created new attack vectors that criminal organizations are actively exploiting. As transportation companies increasingly rely on digital platforms for operations, the intersection of cyber crime and traditional cargo theft will continue expanding.
Organized criminal groups have recognized that compromising digital systems provides easier access to physical goods than traditional theft methods. This campaign represents a concerning evolution where cyber criminals no longer limit themselves to data theft or financial fraud—they're using digital access to steal tangible assets worth millions of dollars.
Companies in the transportation and logistics sector must adapt their security strategies to address this hybrid threat. Traditional physical security measures alone cannot defend against attackers who compromise digital systems to redirect cargo. Similarly, cybersecurity programs focused solely on data protection miss the physical impact of these attacks.
Bottom Line
This Proofpoint research reveals a sophisticated cargo theft operation that combines social engineering, legitimate remote access tools, and deep industry knowledge to steal physical goods worth millions. The attacks demonstrate how organized criminal groups are leveraging cyber capabilities to enhance traditional theft operations. Transportation companies must implement comprehensive security measures that address both digital and physical security risks, recognizing that modern supply chain protection requires defending against threats in both domains. With annual cargo theft losses exceeding $30 billion globally, the stakes are too high to treat cybersecurity and physical security as separate concerns.


