Hackers Exploit Post SMTP Plugin to Hijack WordPress Administrator Accounts

Attackers are actively exploiting a critical vulnerability in Post SMTP, a WordPress plugin installed on over 400,000 websites. The flaw allows hackers to seize administrator accounts and take complete control of vulnerable sites.
Post SMTP ranks among the most popular plugins for handling email on WordPress sites. Developers market it as an advanced alternative to WordPress's standard wp_mail() function, offering extended functionality and improved reliability. This widespread adoption makes the current vulnerability particularly concerning.
The Technical Breakdown
Security researcher netranger discovered the vulnerability and reported it to Wordfence on October 11, 2025. The bug received the identifier CVE-2025-11833 with a CVSS score of 9.8 out of 10—placing it in the critical severity category. All versions of Post SMTP from 3.6.0 onward contain this flaw.
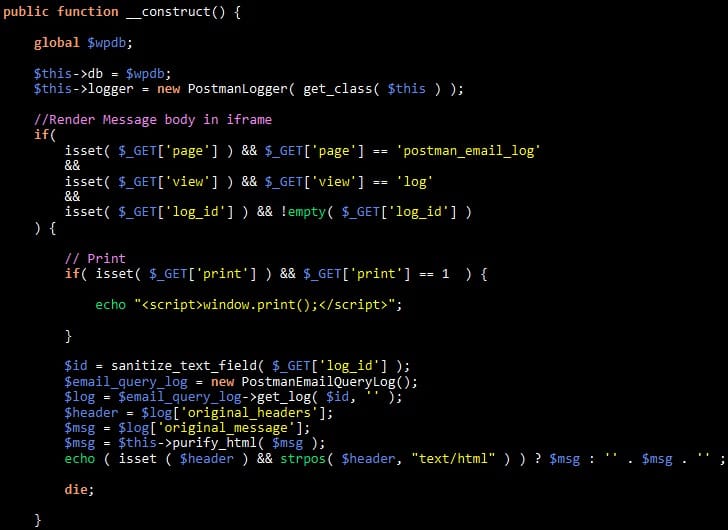
The problem stems from missing access rights verification in the _construct function within PostmanEmailLogs. In practical terms, the component responsible for logging sent emails delivers log contents to anyone who requests them. There's no authentication check, no permission verification—just open access to potentially sensitive email records.
Furthermore, these logs contain password reset messages, including the links users receive to change their administrator credentials. An attacker can read these logs, intercept a password reset email, use the link to change the administrator's password, and gain full control over the site. The attack chain is straightforward and requires no special privileges.
Timeline of Response and Exploitation
Wordfence notified the plugin developer about the critical vulnerability on October 15. The patch didn't arrive until October 29, when version 3.6.1 finally addressed the issue. That two-week window gave attackers time to prepare.
According to WordPress.org statistics, approximately half of Post SMTP users have installed the update. This means roughly 200,000 sites remain vulnerable—a significant attack surface for threat actors.
In addition, hackers wasted no time exploiting CVE-2025-11833. Wordfence recorded the first attack attempts on November 1, just three days after the patch release. In recent days, the company has blocked over 4,500 attacks targeting this vulnerability across their clients' sites.
However, Wordfence protects only a portion of the WordPress ecosystem. The real number of exploitation attempts likely reaches tens of thousands of sites.
A Pattern of Security Issues
This vulnerability represents the second serious security problem in Post SMTP within recent months. In July 2025, PatchStack discovered CVE-2025-24000, a similar flaw that also allowed unauthorized log access and password reset email interception. That vulnerability affected users with minimal privileges, making the attack surface even broader.
The recurrence of similar vulnerabilities in the same component suggests a deeper issue with the plugin's security architecture. Per industry best practices (OWASP's Authentication guidelines), any component handling sensitive data—particularly authentication-related information—should implement multiple layers of access control verification.
What Site Administrators Should Do
If you're running Post SMTP, update to version 3.6.1 immediately. This isn't optional maintenance—it's an urgent security requirement. Attackers are actively scanning for vulnerable installations.
In my opinion, site administrators should also review their administrator account activity logs for any suspicious password changes or login attempts from unfamiliar IP addresses. If you suspect your site was compromised before updating, change all administrator passwords after installing the patch, and consider conducting a full security audit.
Lastly, this incident highlights why relying on a single plugin for critical functions like email handling carries inherent risks. Organizations should evaluate whether their WordPress installations need additional security monitoring, particularly for plugins that handle authentication-related data.
The lesson here extends beyond Post SMTP: popular plugins become high-value targets. Keeping them updated isn't just good practice—it's essential defense against attackers who know exactly which vulnerabilities to exploit and when.


