Hackers Are Massively Exploiting Outdated WordPress Plugins

Cybersecurity firm Wordfence is sounding the alarm about a large-scale malicious campaign targeting critical vulnerabilities in two popular WordPress plugins: GutenKit and Hunk Companion. In just two days, the company blocked 8.7 million attack attempts against its clients.
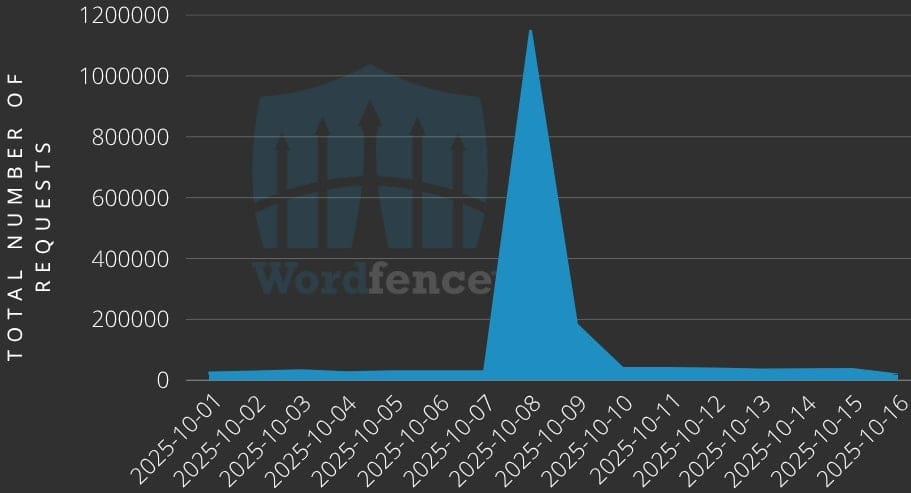
Three Critical Vulnerabilities Under Active Exploitation
Attackers are leveraging three critical bugs, each with a CVSS score of 9.8: CVE-2024-9234, CVE-2024-9707, and CVE-2024-11972. All three vulnerabilities enable remote code execution on affected websites.
CVE-2024-9234 affects GutenKit, a plugin with 40,000 active installations. The flaw stems from an unauthenticated REST endpoint that allows attackers to install arbitrary plugins without any authentication. The vulnerability impacts GutenKit version 2.1.0 and earlier.
Meanwhile, CVE-2024-9707 and CVE-2024-11972 affect Hunk Companion, which has approximately 8,000 installations. Both vulnerabilities involve authorization failures in the plugin's themehunk-import REST endpoint, similarly enabling unauthorized plugin installations. The first bug affects version 1.8.4 and earlier, while the second impacts version 1.8.5 and all previous releases.
The Attack Chain
According to Wordfence, attackers are exploiting these vulnerabilities to inject another vulnerable plugin onto compromised sites, which then grants them remote code execution capabilities.
The threat actors host their malicious plugin in a ZIP archive named "up" on GitHub. The archive contains obfuscated scripts capable of uploading, downloading, and deleting files, as well as modifying file permissions. One script—password-protected and disguised as a component of the All in One SEO plugin—automatically logs the attacker in as an administrator.
These tools provide attackers with complete control over compromised servers, allowing them to maintain persistent access, steal or upload files, execute arbitrary commands, and intercept sensitive data.
When direct exploitation fails, attackers often inject wp-query-console, another vulnerable plugin that permits unauthenticated code execution.
Patches Available, But Sites Remain Vulnerable
Patches for all three vulnerabilities have been available for nearly a year. GutenKit 2.1.1 was released in October 2024, and Hunk Companion was updated to version 1.9.0 in December 2024. Despite this, many websites continue running vulnerable versions, making them easy targets.
What Site Administrators Should Do
Wordfence has published a list of IP addresses generating high volumes of malicious requests. The company recommends that administrators check their logs for suspicious requests to /wp-json/gutenkit/v1/install-active-plugin and /wp-json/hc/v1/themehunk-import.
Site owners should also inspect the following directories for suspicious files: /up, /background-image-cropper, /ultra-seo-processor-wp, /oke, and /wp-query-console.
Most importantly, WordPress administrators should immediately update GutenKit and Hunk Companion to their latest versions to protect against these active threats.


